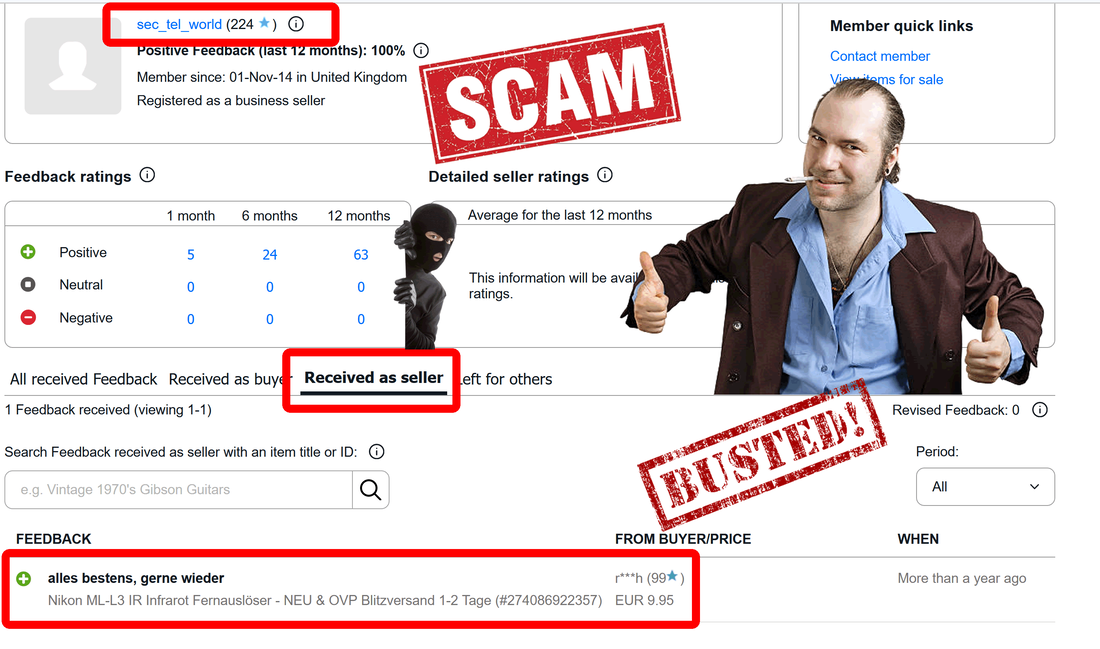
This article is just an update on previous one.
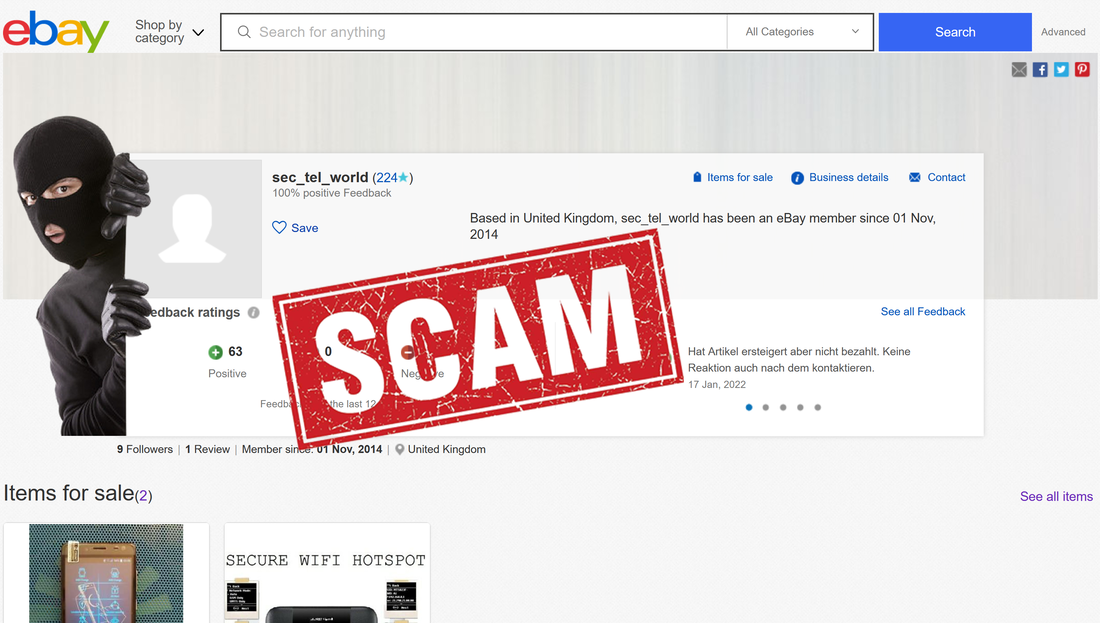
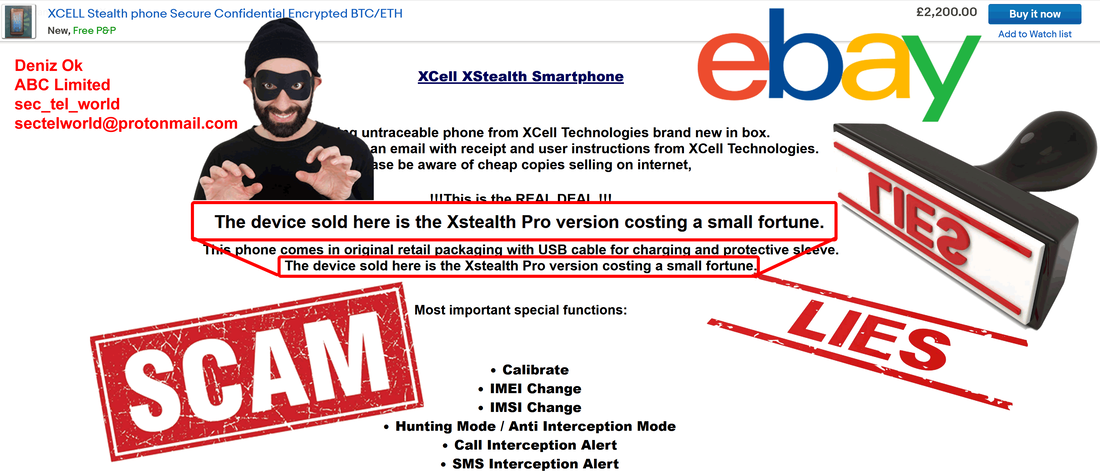
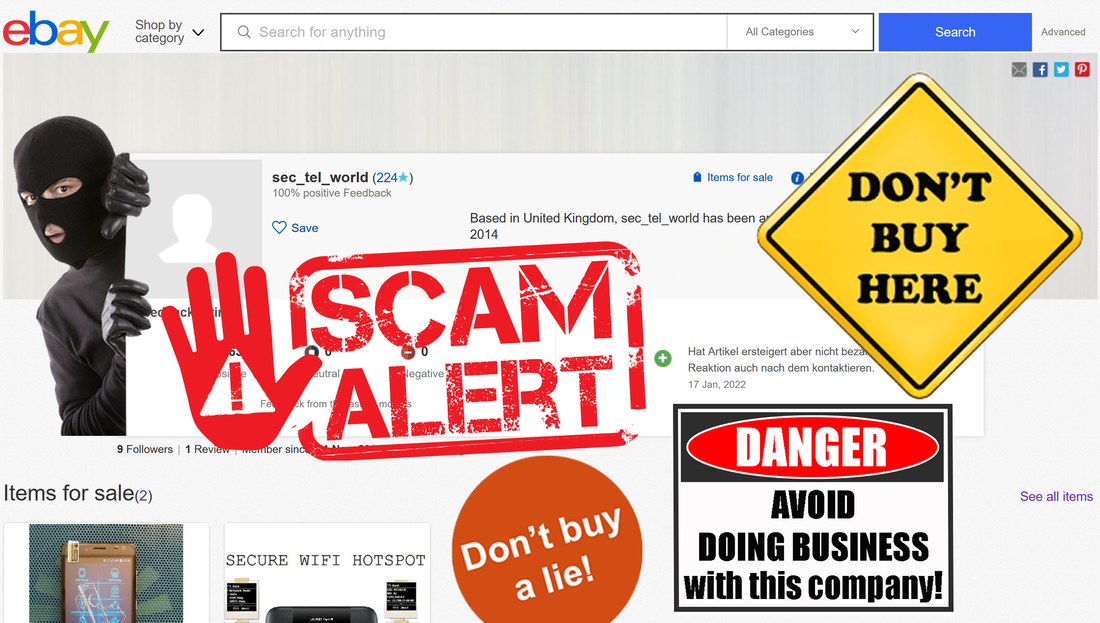
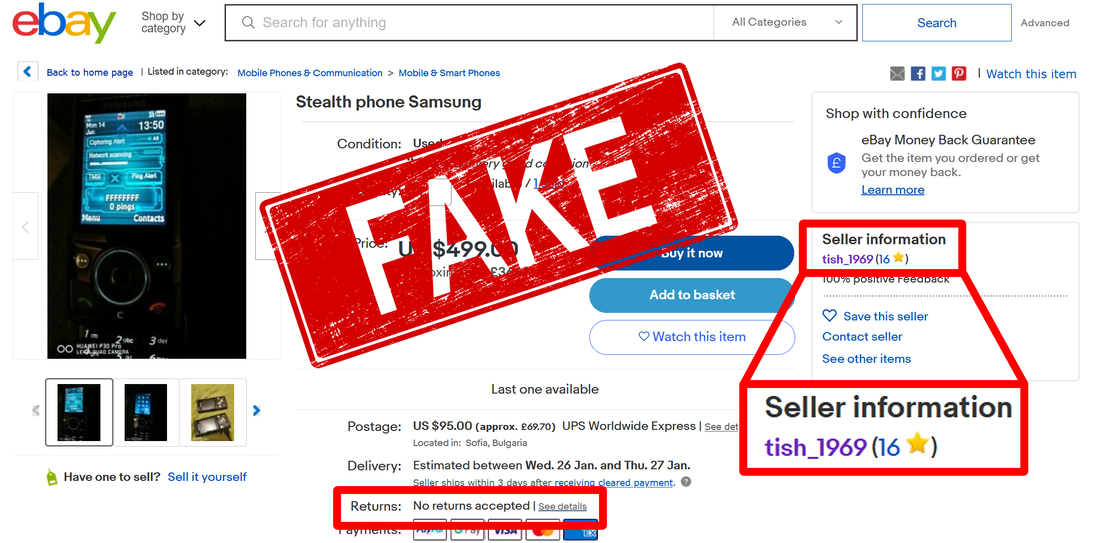
Following first blog article revealing his scam, Deniz Ok changed his eBay account name from sec_tel_world to secure_gsm.
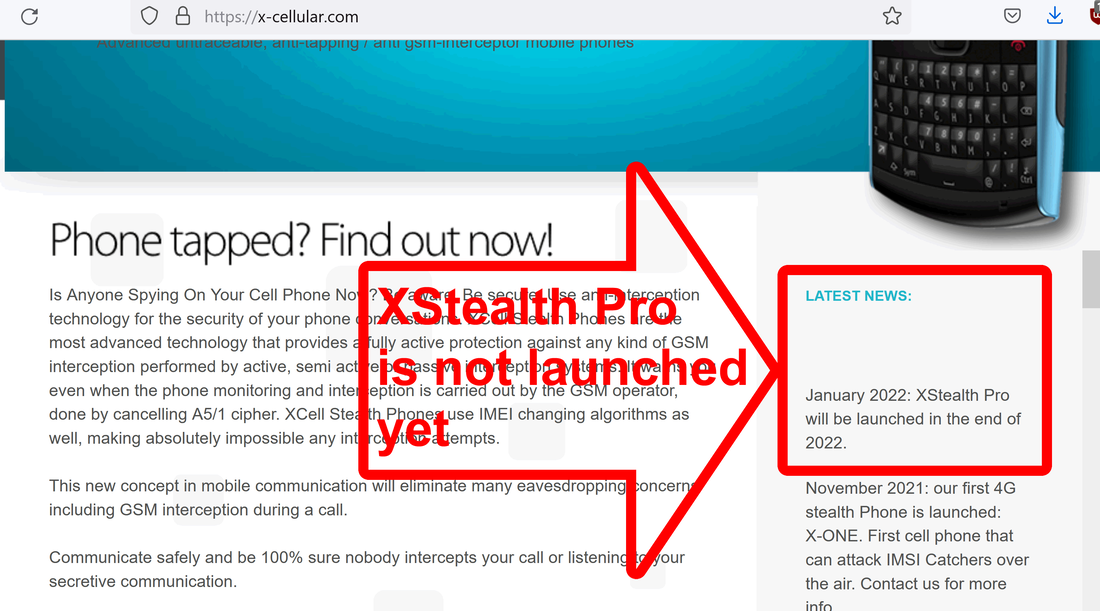
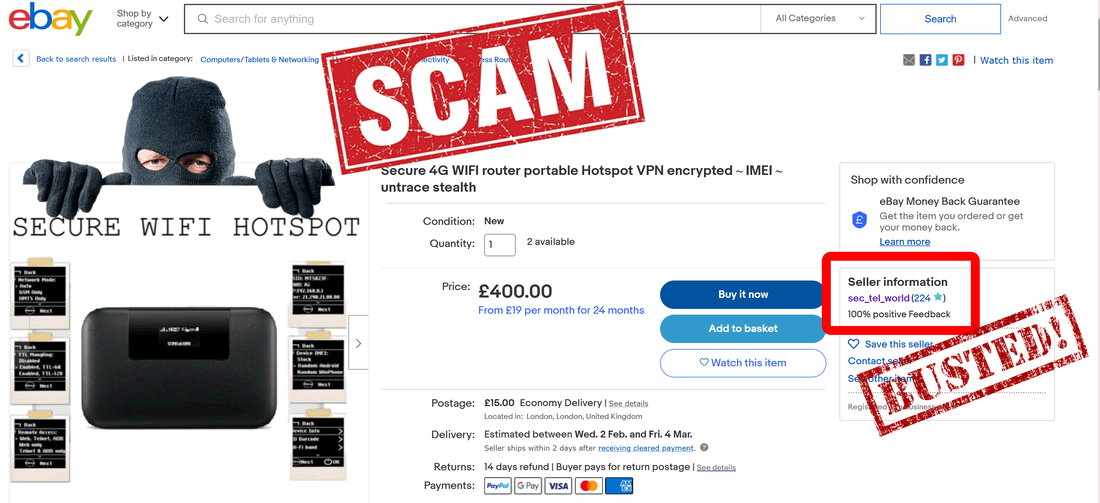
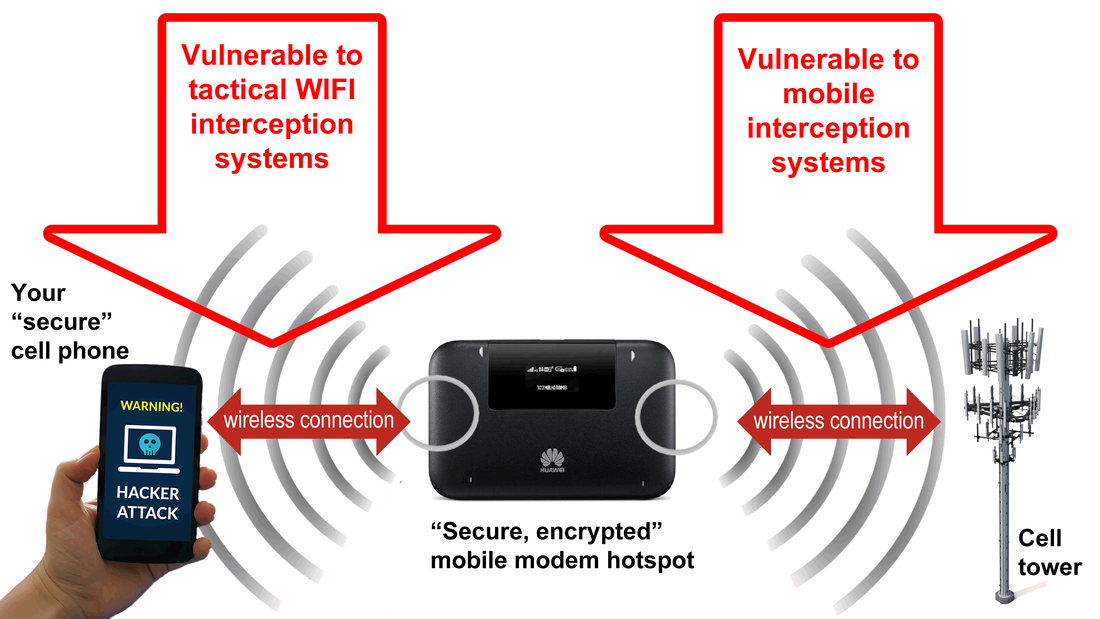
Also, the scammer removed from eBay the other scam: "Secure 4G WIFI router".
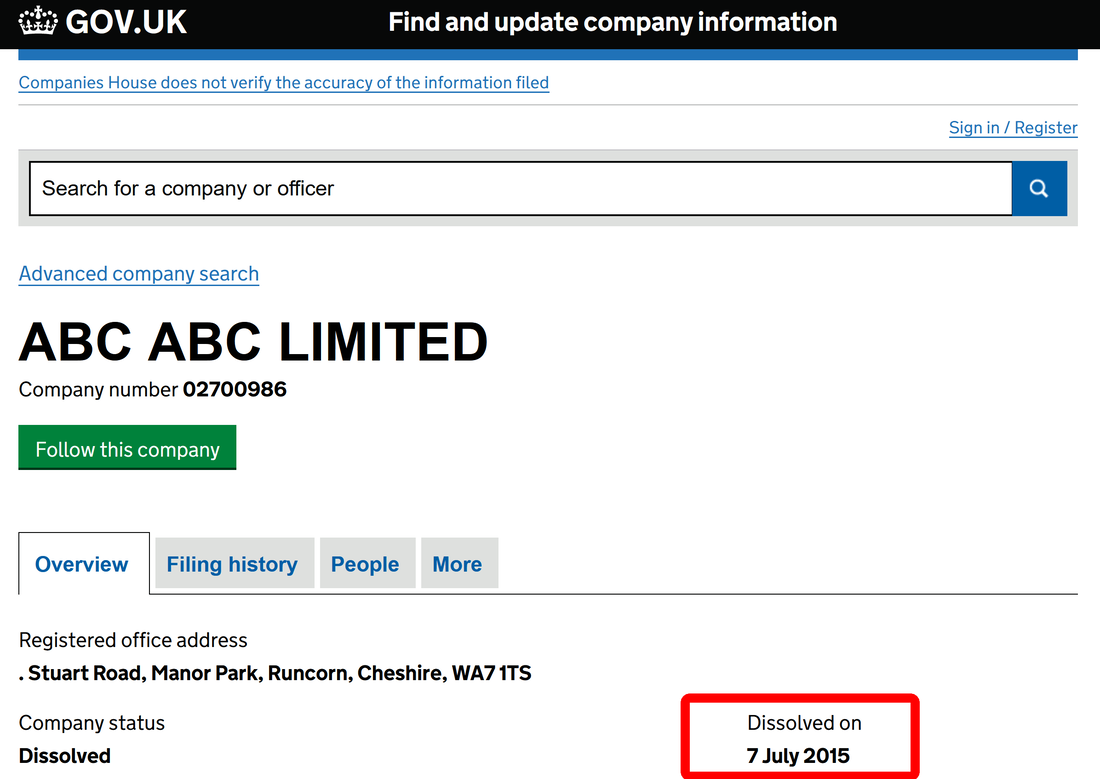
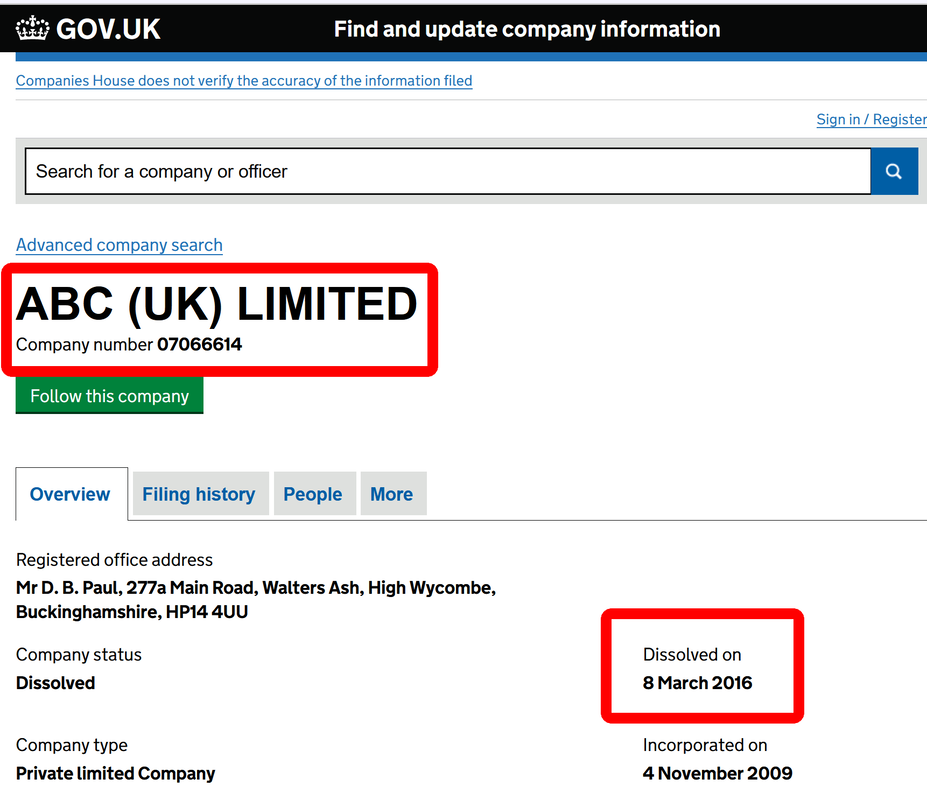
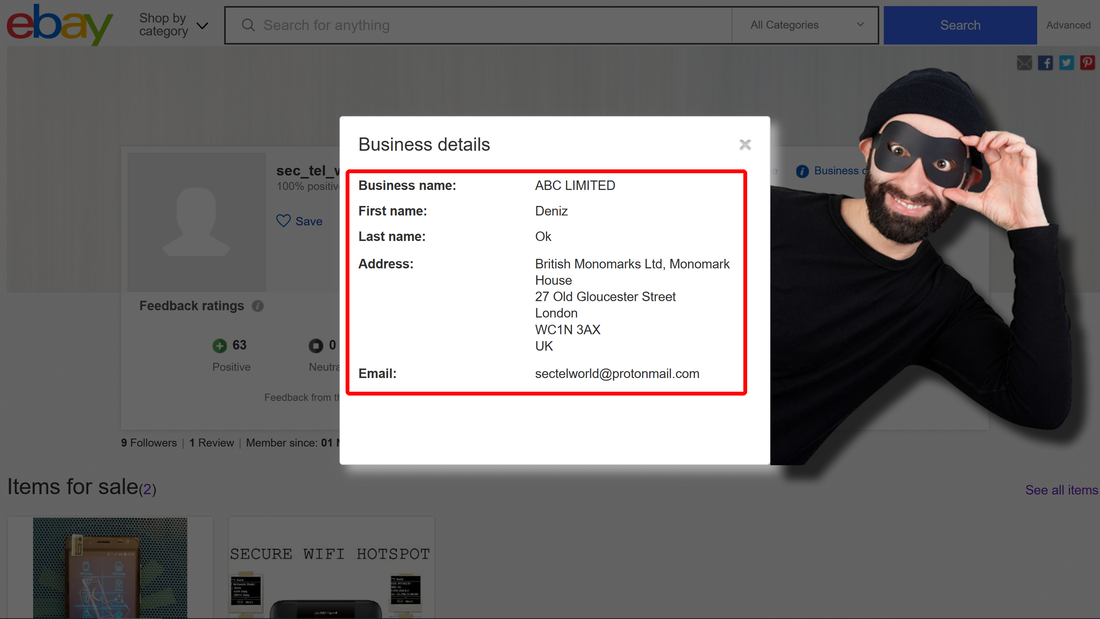
Trying to erase scam traces, Deniz Ok has changed a company fake postal address with another one, as fake as first one: ABC LIMITED (Deniz Ok) 22 Eastcheap, London EC3M 1EU, United Kingdom. What he is actually trying to say is that his "company" is located in the heart of London, next door to London Tower, a very expensive London area, paying a rent for an expensive office, selling on eBay some stealth phones manufactured by other company. No company website, no real address and no registration. How much credibility can have this hilarious cover?
Also, there is no ABC Limited company registered in the UK: check here.
Late edit 1 (2nd April): we have sent one of our friends from London, to visit ABC Limited "company", on that specific address. Updates in few days.
Late edit 2 (9th April). Have a wild guess: on that address is no ABC Limited company. Our London friend has asked about Deniz Ok, as well. The same result: there is no Deniz Ok on that location. Busted. Again.












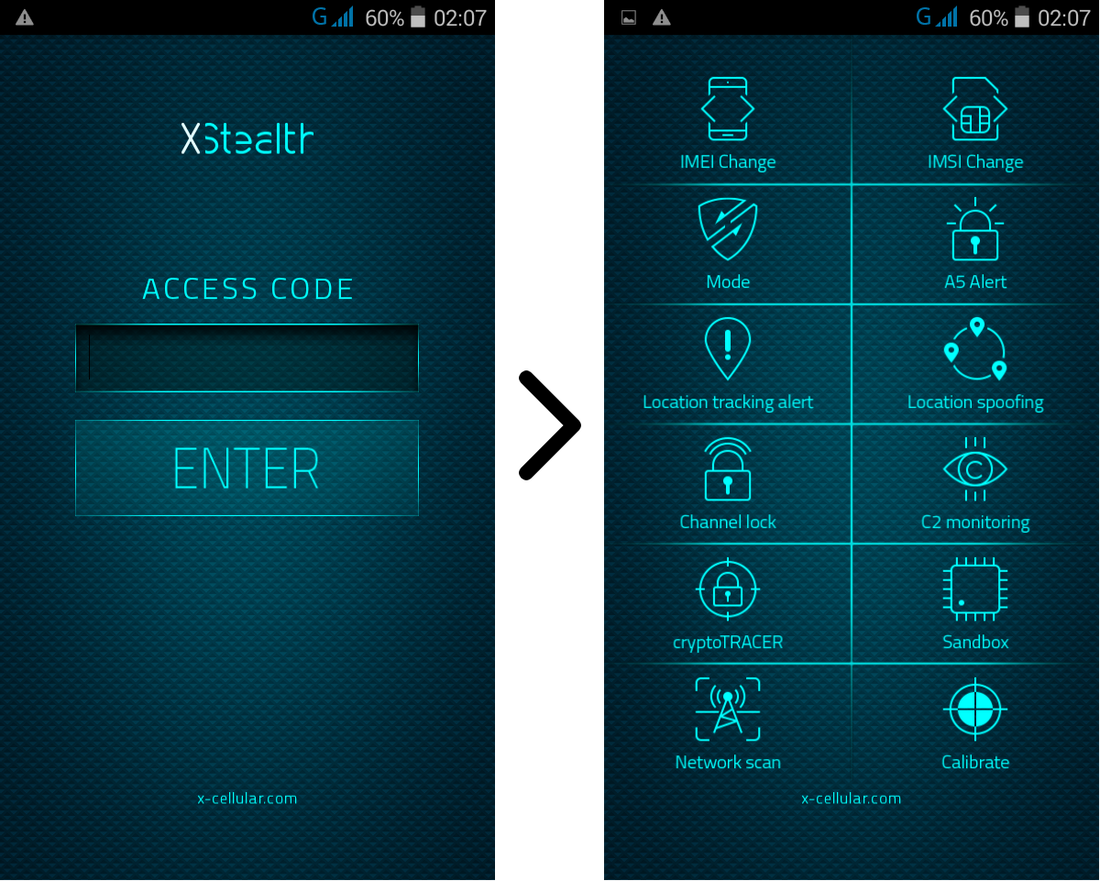
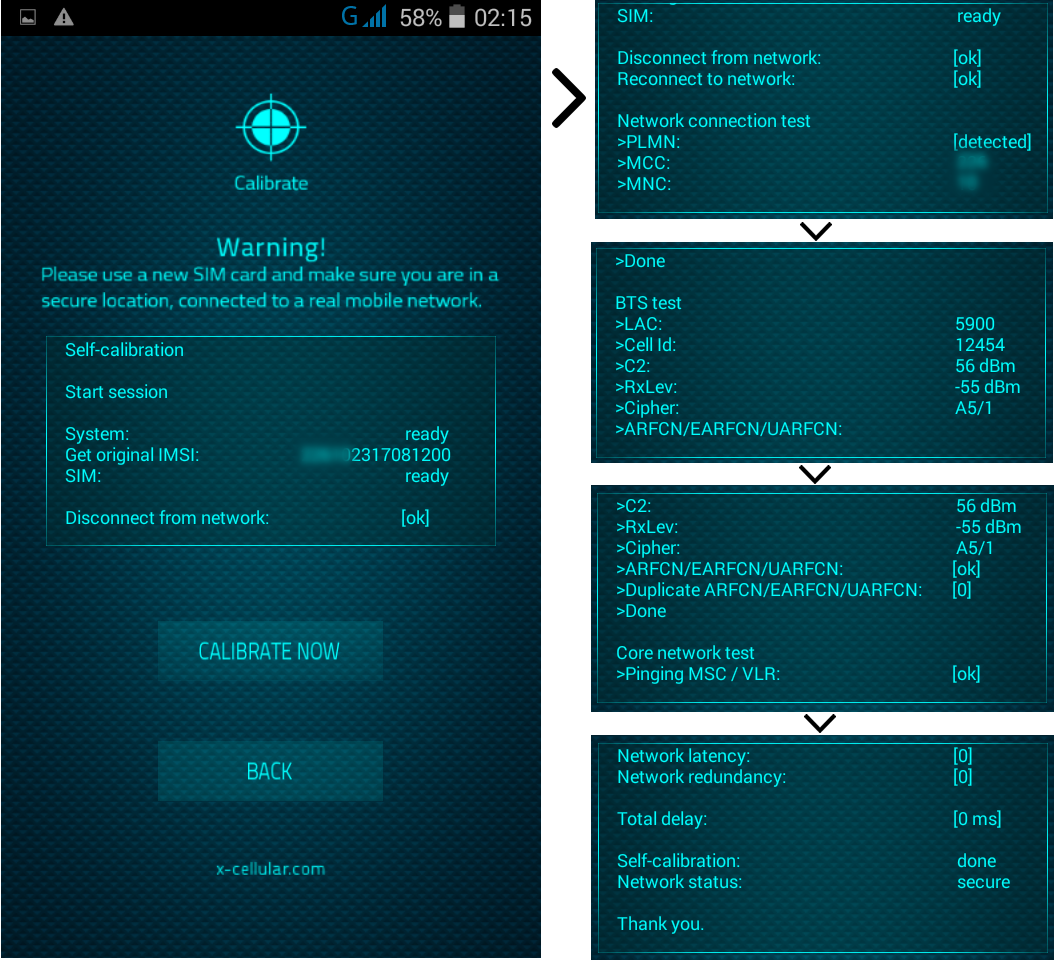
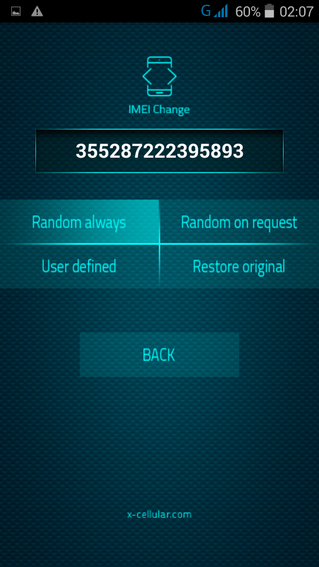
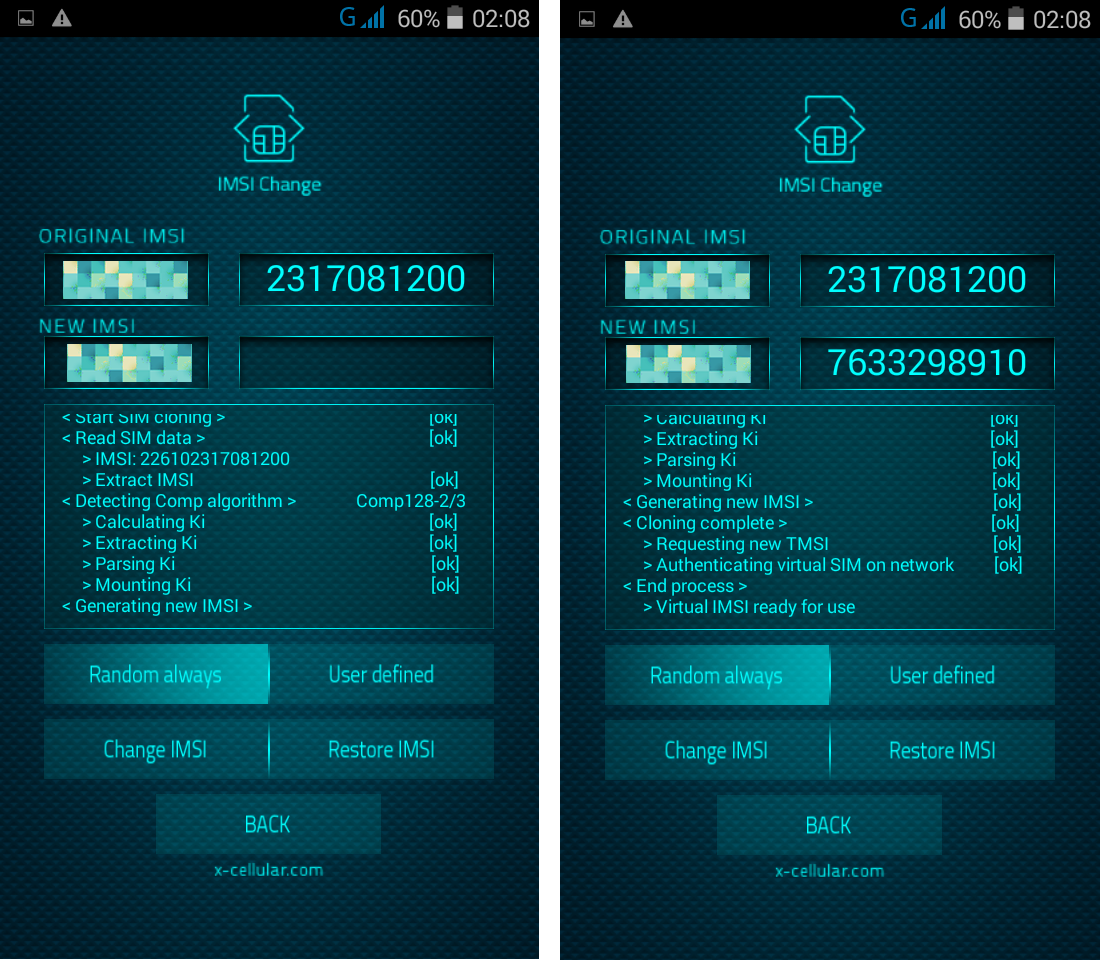
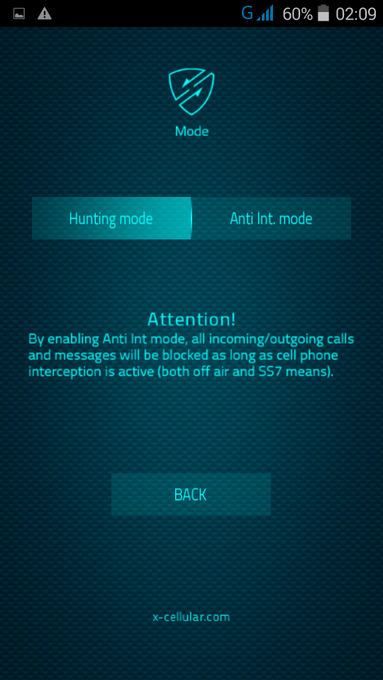
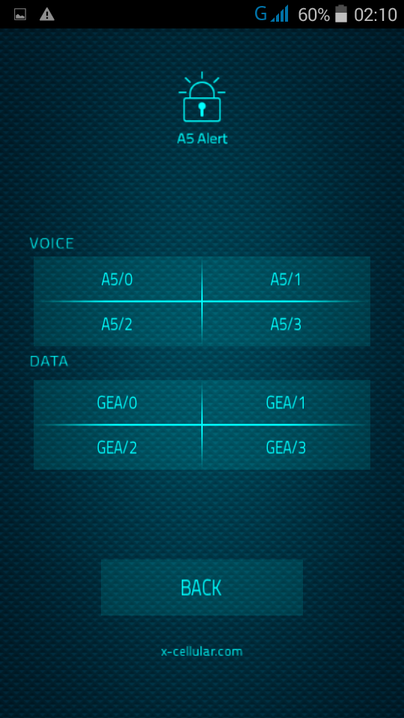
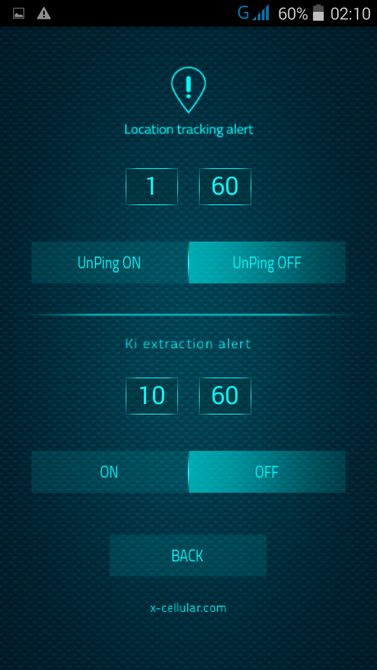
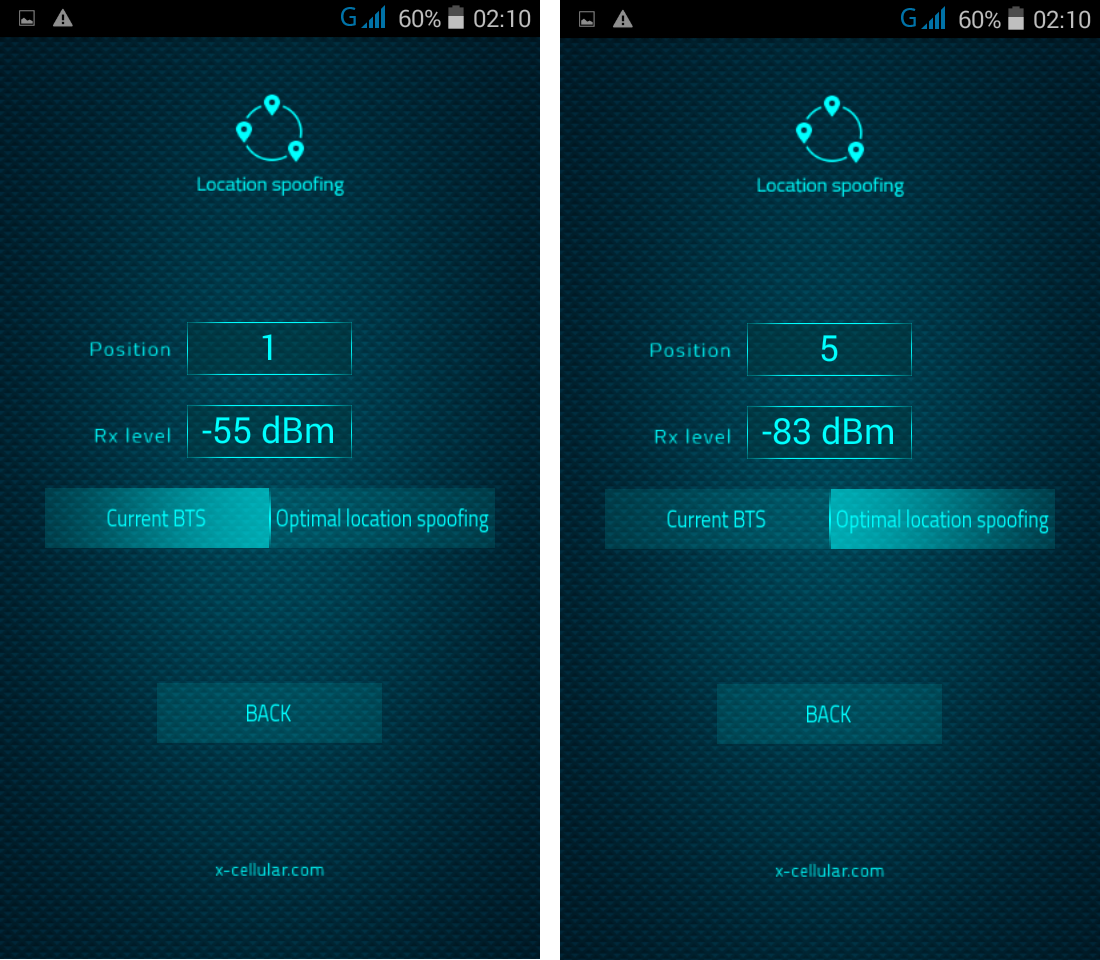
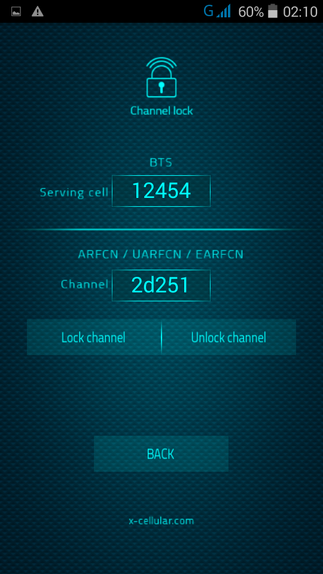
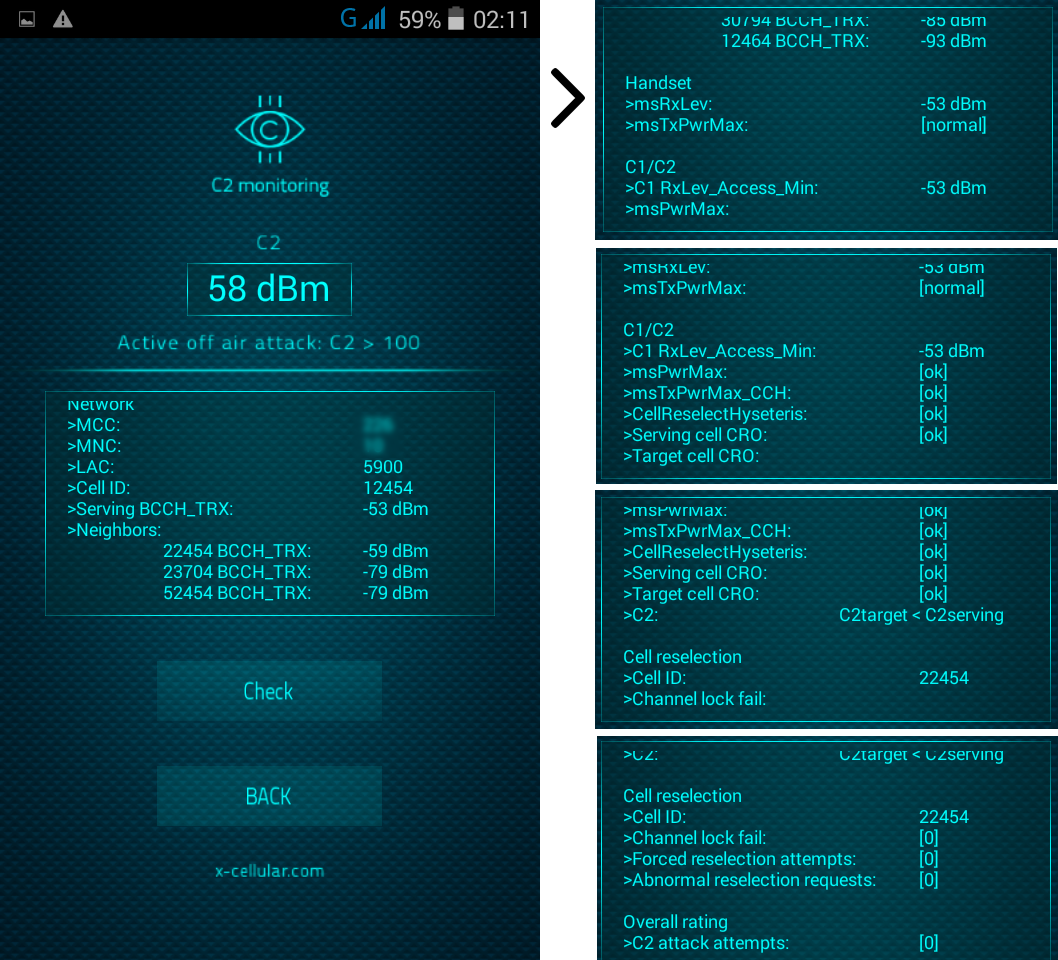
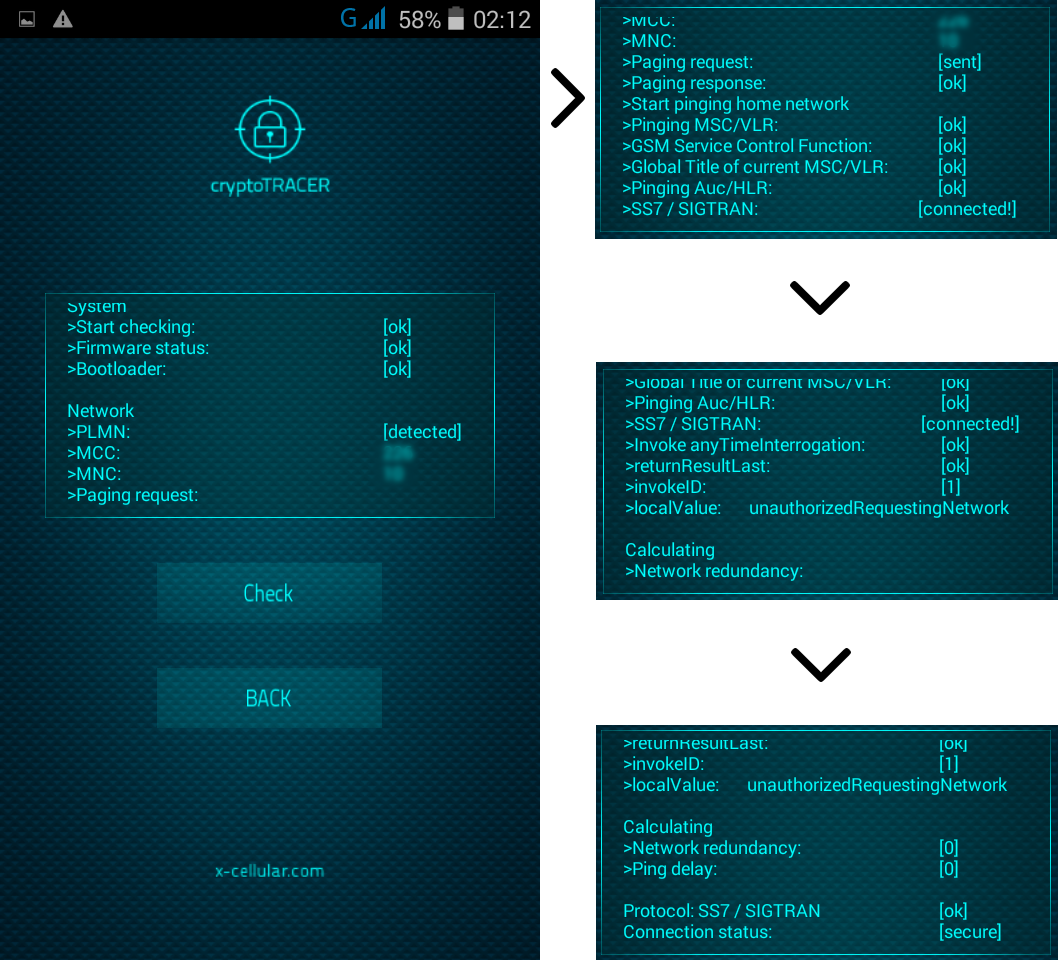
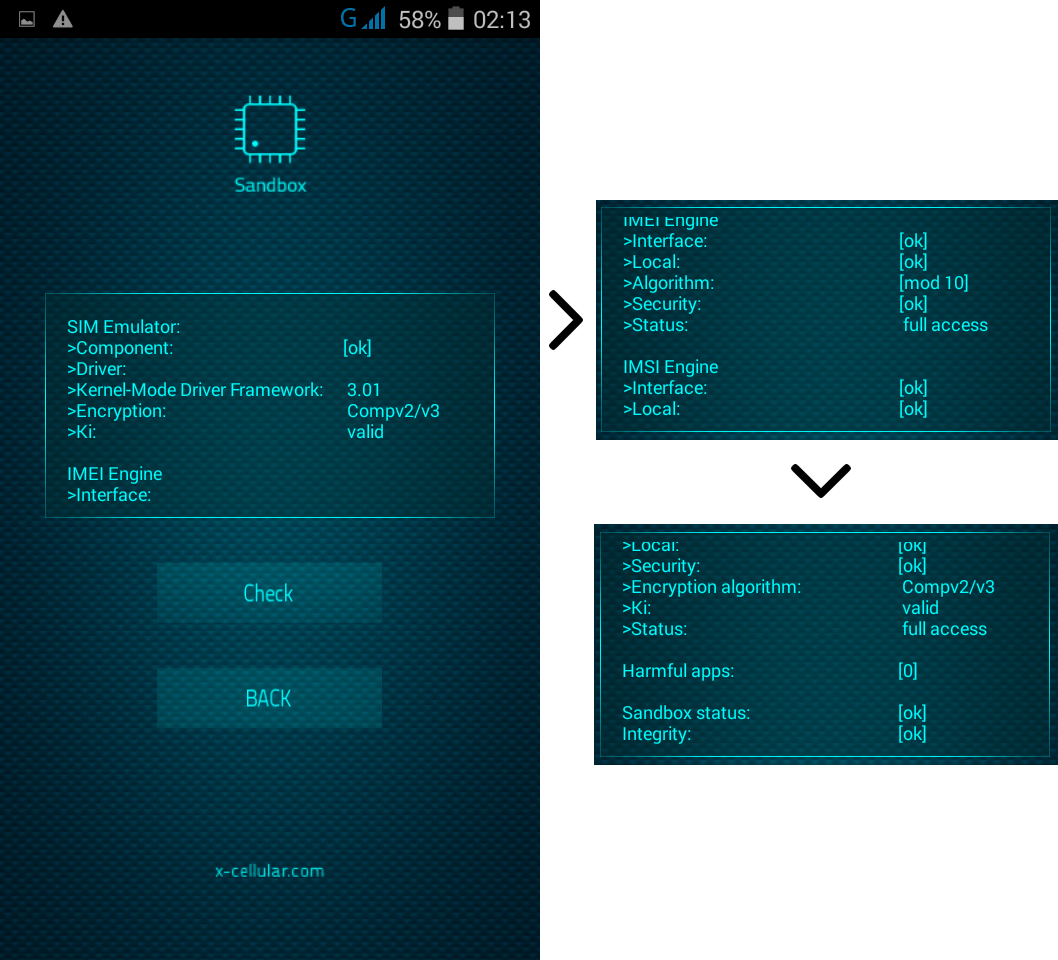
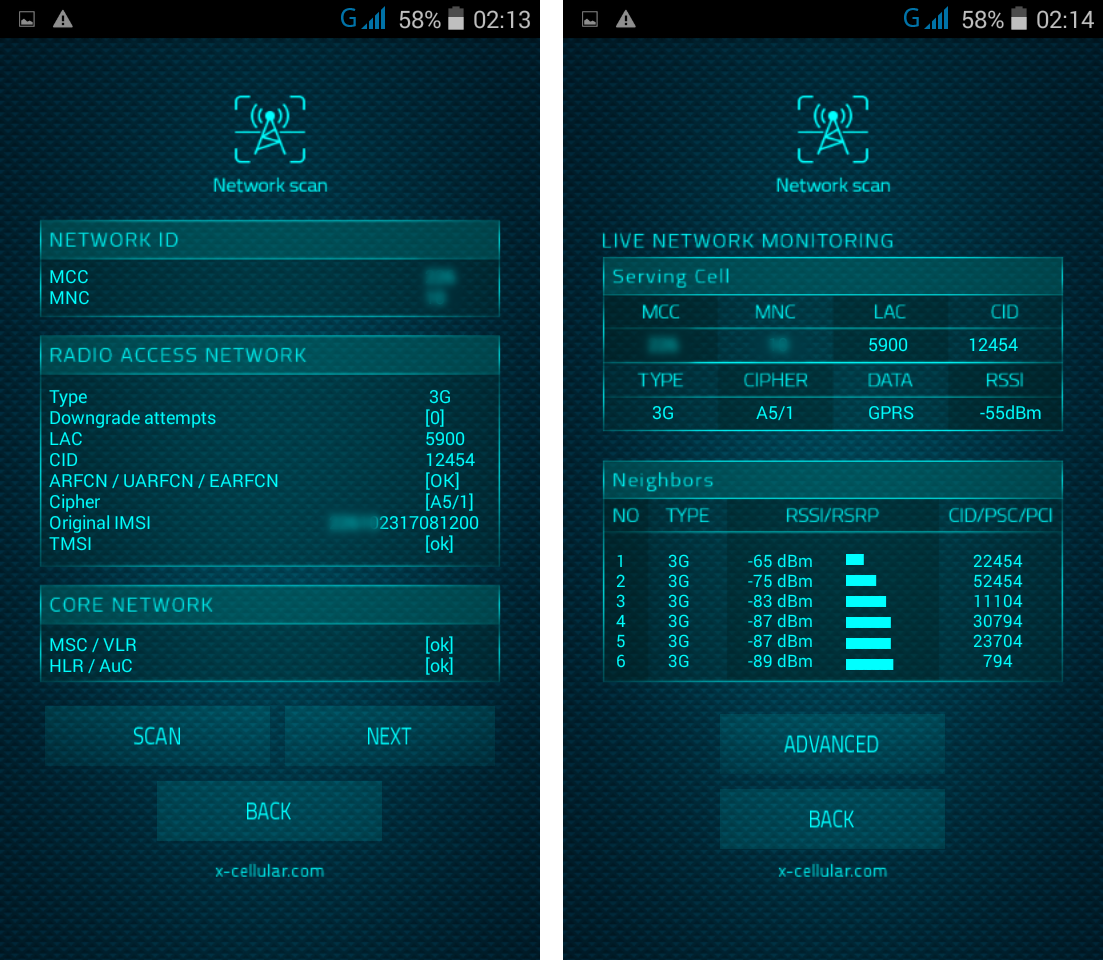
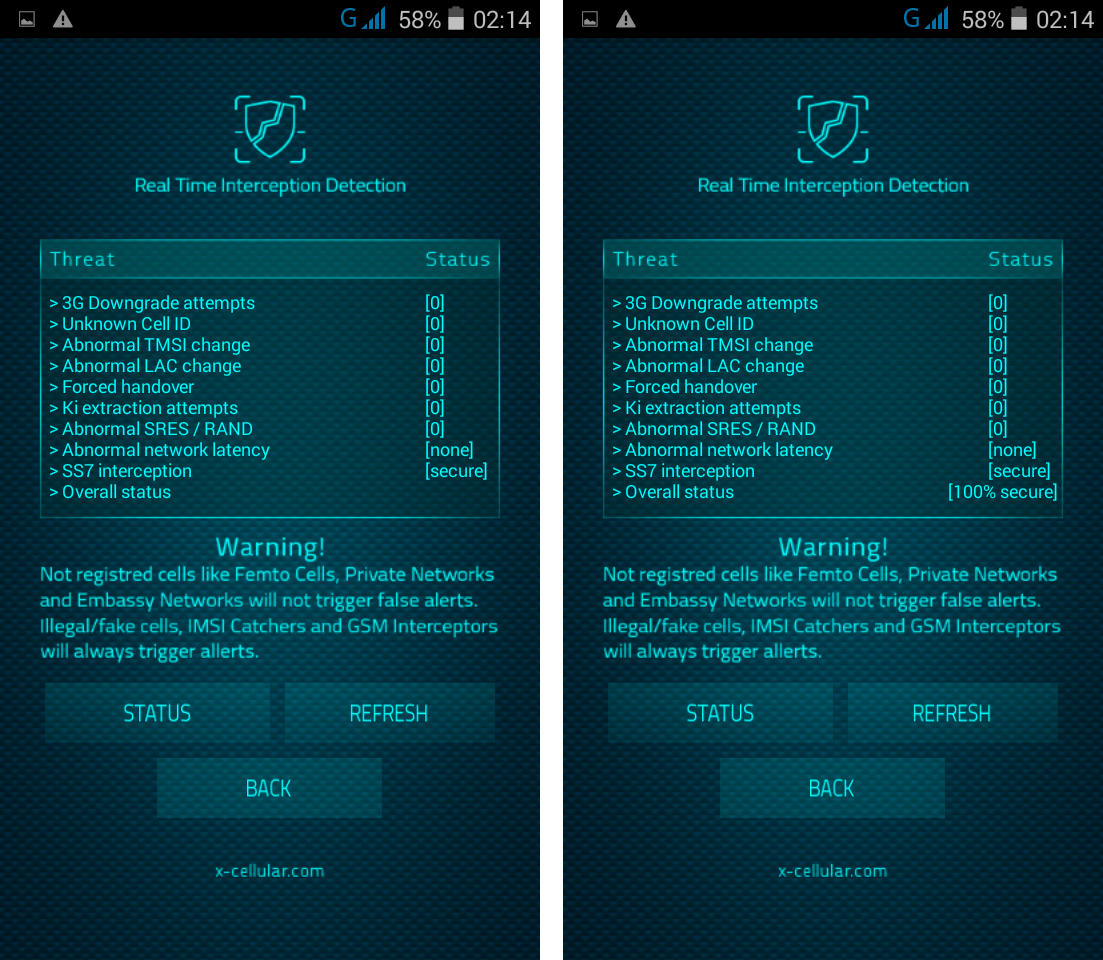
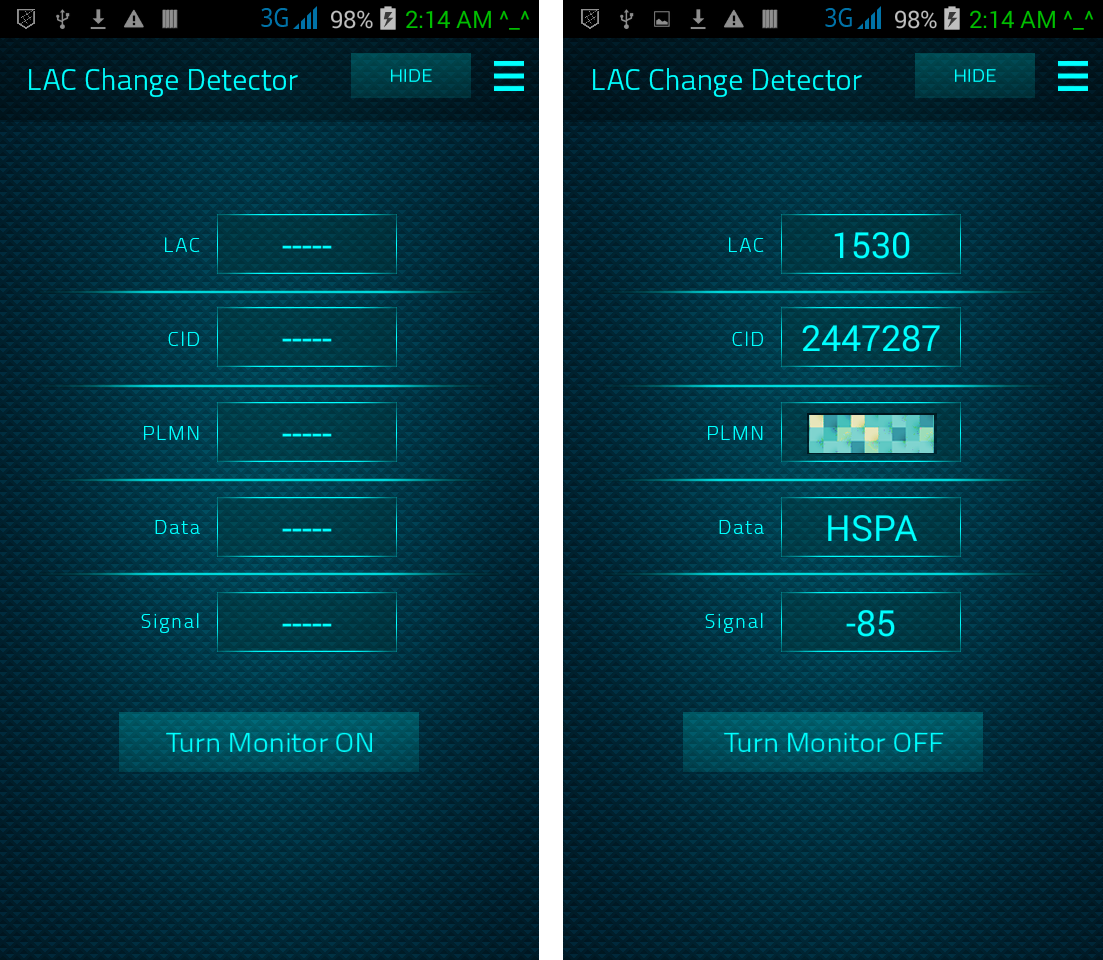
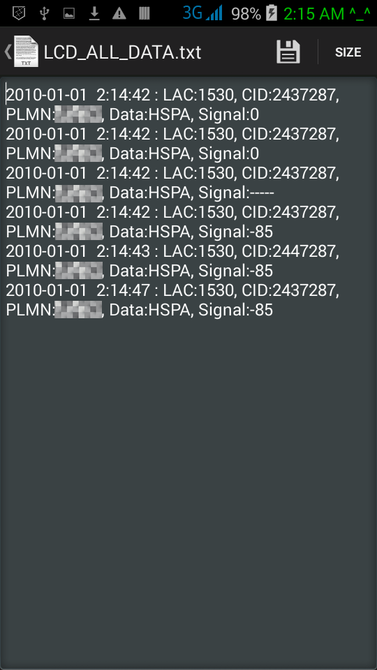
 RSS Feed
RSS Feed