|
Recently browsing eBay, we have discovered 2 old scammers located in the UK, that are using 2 new accounts, selling fake stealth phones since 2011: Here is the fake stealth phone type sold by spdirect on eBay: What you have to do, just to make sure you will not buy from a scammer, a fake stealth phone? Nothing complicated: avoid fakes by buying from official distributors or directly from manufacturer.
0 Comments
SMS ENCRYPTION REDEFINED A revolutionary innovation: Multi-Layer Security Protocol - MLSP® by XCell Technologies Real end-to-end encryption and protection If you are either super important, super paranoid or a super spy, there are times when you need to be able to use a cell phone and not leave a trace or any chance to anyone to intercept your calls and text messages, including law enforcement and intelligence agencies. Secure = encryption? Well, think again... Nowadays, interception issue affects most of the people, even if they are not aware of it. Not to mention so called “off air GSM interception systems” or also known as “IMSI-catchers”, "GSM Interceptors" or "StingRays", it has been known since 2014 that using the legacy SS7 (Signaling System No. 7) protocol SMS based traffic text messages can be easily intercepted by using diameter based networks independently of device or OS type. Signaling System No. 7 vulnerabilities are easy to be exploited even by hackers, being a 50-year old protocol that is probably part of a majority of cell phones and text messages in the world. Generally speaking, most of aware users regarding cell phone interception by above technologies, believe that using encryption solutions will secure their calls and text messages. It is encryption a real solution? Let's see... Law enforcement, homeland security and other related actors have plenty of methods to intercept messages and read text content, even when using encryption. Ranging from SS7 exploit, encryption backdoors or intentionally weaken popular encryption algorithms to lawful hacking that circumvent encryption and hitech decryption technology, all are there at their fingertips. Encryption will not protect your privacy. At all Recent headlines warn that the government now has greater authority to hack your coell phones, in and outside the US. Changes to federal criminal court procedures known as Rule 41 are to blame; they vastly expand how and whom the FBI can legally hack cell phones. But just like the NSA's hacking operations, FBI hacking isn't new. In fact, the bureau has a long history of surreptitiously hacking us, going back two decades. Back-doors provided for law enforcement Encryption back doors remain largely viewed as weakening everyone’s protections all the time for the sake of some people’s protections on rare occasions. As a result, workarounds like the FBI found are likely to be the most common approach going forward. Indeed, in recent years, law enforcement agencies have greatly expanded their hacking capabilities. Many reputable encryption developers and companies have chosen to retain the ability to read and use their customers’ content, or perhaps they decided there is not a sufficient business case to add end-to-end encryption or user-controlled encryption. Their users’ encrypted content is more readily available to law enforcement because they hold the decryption keys. The same companies offer their services in a way that encryption does not preclude their ability to hand over the content to law enforcement in response to a warrant. Are those services as secure? Lawful hacking Most of national security agencies had been shown to have immense surveillance capabilities actively deployed on a mass scale, especially in those countries where the functions of law enforcement and national security overlapped. Beside encryption master-key and built-in back doors that provide law enforcement exceptional access to anyone secrets and privacy, they now have unprecedented access to information through open-source intelligence, collection of metadata, sophisticated traffic analysis tools and data analysis algorithms. Many local and international laws are mandating insecurity by requiring government access to all data and communications that permits lawful hacking (otherwise known as encryption circumvention). Encryption vendors and law enforcement work together to solve access "problem". One suggested fix is one way information sharing where vendors make law enforcement aware of unpatched exploits, allowing the government (and anyone else who discovers it) to use these vulnerabilities to gain access to communications and data. It's a horrible suggestion - one that puts vendors in the liability line of fire and encourages continued weakening of device and software security. Several individuals with backgrounds in security and systems have begun to explore possible technical mechanisms to provide government exceptional access. XCell approach regarding SMS encryption and protection XCell Technologies is really serious about mobile security, bringing you the most advanced SMS security solutions. Concerns about government mass surveillance and their ability to decrypt anything by using given master-keys, backdoors, lawful hacking or effective decryption solutions were the factors driving us to develop a brand new and 100% secure SMS communications which use not only strong military grade encryption but adding a new security layer by exploiting GSM network via MLSP®, to make sure there is no way to intercept text messages or metadata, even in encrypted mode. All above overleap existing commercial-encrypted apps, services, devices, and also law enforcement access to your sensitive info. GSM provides by default only a basic range of security features to ensure adequate protection for both the operator and customer. Over the lifetime of a system threat and technology change, and so the security is periodically reviewed and changed here on XCell Technologies, and then applied on our products. Taking advantage on GSM network architecture and SMS Transport Protocol, our SMS encryption technology is capable to send/receive encrypted and non-interceptable messages. Our SMS encryption application called XCrypt use a groundbreaking multi-layer technology to protect SMS from being intercepted and decrypted. As a unique encryption application, beside strong military grade encryption, XCrypt use a brand new patented technology in order to send/receive encrypted messages: discrete GSM channels or Multi-Layer Security Protocol®. That will protect not just encrypted text messages but also metadata which is not encrypted. XCrypt concept. An insight into techniques used for 100% secure text messages Definitions
MLSP® Multi-Layer Security Protocol - MLSP® consist in: 1. Physical layer: encrypted text message. The phone will encrypt text messages by using following protocols: • RSA • AES 256 • Elliptic Curve (ECIES) 256 • SHA256 • Protected by ITSEC Evaluation level 3 2. Multi-layer routing and transport protocol. Encrypted SMS data is randomly segmented and distributed in bursts by Application Port Addressing Technology, via discrete GSM channels which usually are not "listened" by mobile interception systems (IMSI Catchers, GSM Interceptors or StingRays), both in air interface (UM Interface in terms of GSM networks) and Abis, A and C-G mobile network interfaces. This way, SMS data which is usually sent over GSM Layer 1 (and widely intercepted on Layer 1) will be sent by using a combination of GSM Layer 1 and GSM Layer 2 (LAPDm). By consequence, no mobile interception systems (as GSM Interceptors) and lawful interception systems (SS7 interception also known as network switch based interception or interception by the help of network operator) will be able to intercept the whole message but only a few bursts which are encrypted anyway. 3. Metadata protection. Regular SMS metadata is not saved in a separate file (called a metadata file). XCrypt separate metadata and the data it describes (SMS encrypted text), sending metadata file in bursts over the network, by the same Port Addressing technology. Metadata is of little value without the data file (SMS) it relates too. At the same time, metadata makes the data more usable and therefore, more valuable. An encrypted text message with separate metadata file will reveal nothing about SMS sender and receiver. How does it work 1. Phone level At phone level XCrypt use a technology called port directed SMS, which is widely implemented in J2ME MIDP on mobile devices. The concept is basically that when an user send an encrypted SMS message to "B-Party" phone, a particular port number will be specified along with encrypted message, so only the device which is "listening" on that particular port will be able to receive an encrypted message. When a message is received on a port that the application is listening on, the message gets directly routed to secure Inbox instead of going to the standard message Inbox. XCrypt will locally encrypt text messages at military level, then by message segmentation and Port Addressing will send randomly splitted bursts (bit streams) along with certain port address data by adding redundant bits to information binary string, to "B-Party" phone. Along with encrypted split message, the application on "A-Party" phone will send Port Addressing data, which will trigger opening certain Port Address on "B-Party" phone. This way, encrypted message will go through, avoiding standard phone Inbox and arriving directly on secure Inbox. All this steps are transparent on receiving ("B-Party") phone, which also require user interaction which have to allow message to be routed to secure Inbox and decrypted by inserting the right password. On "B-Party" phone, by port destination address, encrypted bursts will be selectively received, concatenated, decrypted and displayed only on "B-Party" phone which use the same XCrypt application that "listen" on certain receiving ports. If on the "B-Party" (destination phone) is not also installed XCrypt app, then received message will not be delivered nor displayed by the phone (not even in encrypted/unreadable mode) due to Port Addressing technology which filter messages by port address. When encrypting SMS, metadata file will be generated separately from text message and not as an integral part of the message as regular SMS do. Metadata file will be then truncated and sent in bursts over GSM network, by Port Addressing technology. This way no metadata can be intercepted by SS7 means. At this level, handset vulnerability refer to forensic grade hardware and software that intend to extract system files and private data off the phone, including decrypted messages stored on XCrypt secure Inbox. XCell phones are protected against forensic procedures by USB volatile filters which does not permit any unauthorised USB connection, triggering motherboard self-nuke. Moreover, XCrypt run on Sandbox partition which is 100% encrypted and protected against file extraction by self-delete mechanism. 2. Um level Um interface (the radio link between the cellular network and the subscriber handset) is the most vulnerable and exploited part of the GSM network by MItM attacks (IMSI Catchers, GSM Interceptors and StingRays), since no network operator help or target consent is needed. XCrypt will make use of GSM network architecture and SMS Transport Protocol in order to protect (already) encrypted messages to be intercepted even in encrypted mode. After encryption, the modulation signal has a carrier wave using GMSK (Gaussian Minimum Shift Keying) modulation. GMSK is a two-state modulation based on the frequency keying stroke. On Um interface XCrypt will use MLSP® technology: encrypted message bursts are not sent only on usual L1 SMS channels - SDCCH (Standalone Dedicated Control CHannel) signaling channels, but also on other available channels which are not subject of SMS interception, forcing Signaling Layer 2 (data link layer based on LAPDm protocol) for SMS Transport. Since GSM Interceptors are "listening" only SDCCH physical channels in order to intercept text messages, will catch only a few encrypted bursts sent over SDCCH but not the whole encrypted message which is split and sent over multi-channel by MLSP® technology. Same for metadata file: is sent over the network in bursts, separately from encrypted message body. No metadata extraction is possible at this level. 3. Core network level The four-layer transport protocol stack of SMS (application, transfer, relay, and link) is used at this level and the transfer layer of this stack is the one which secure text message. GSM core network consist in Mobile switching center (MSC), Home location register (HLR), Authentication center (AuC), Visitor location register (VLR) and Equipment identity register (EIR), which are all vulnerable to network switch based interception, also known as SS7 interception or lawful interception. This kind of interception can be successfully performed only by law enforcement and homeland security agencies, by the help of network provider that allow monitoring hardware installation (SS7 boxes) at their core network based on Communications Assistance for Law Enforcement Act (CALEA). CALEA's purpose is to enhance the ability of law enforcement agencies to conduct lawful interception of communication by requiring that telecommunications carriers and manufacturers of telecommunications equipment modify and design their equipment, facilities, and services to ensure that they have built-in capabilities for targeted surveillance, allowing federal agencies to selectively wiretap any telephone traffic. CALEA covers mass surveillance of communications rather than just tapping specific lines and not all CALEA-based access requires a warrant. Generally, lawful Interception implementation is similar to the implementation of conference call. While A and B are talking with each other, C can join the call and listen silently. At this network level, the main security vulnerability consist in lawful interception. XCrypt is taking advantage on GSM core network, sending both encrypted and non-interceptable text messages by using MLSP® technology. Core network protocols cannot be enforced as Um interface can. Actually there is no need to manipulate those protocols and transfer layers as long as message bursts that transit this part of the mobile network can be logically concatenated (fit together) by Port Addressing and decrypted only by "BParty" phone which run the same XCrypt application and by knowing the right password. By consequence, no text messages can be entirely intercepted by a third party that use CALEA - lawful interception. A few encrypted SMS bursts which are eventually intercepted by SS7 cannot lead by any means to SMS interception. Thus no private data will be collected by this method, phone user privacy being preserved peer-to-peer from "A-Party" to "B-Party" phone. Let's face it: most of nowadays encryption solutions are taking care only on text itself, neglecting message metadata which are still sent on plain text over the network, due to network requirements. Law enforcement and other actors are taking advantage on this, collecting unencrypted metadata to characterize the encrypted data, metadata being this way a valuable source of information for them. By using MLSP® technology on both Um and Core network levels, collecting unencrypted message metadata is not possible, thus no way to extract any additional info beside encrypted message. It has long been said that it doesn’t matter how secure your organization, or personal information and assets, are if you connect them with third parties that are less secure. So take note: servers are third parties. A real end-to-end encryption require no third parties involved on the way from "A-Party" to "B-Party" phone. For maximum level of security and privacy, XCrypt does not require any Internet connection, third party servers or monthly subscriptions. All processes and protocols run locally on the phones (on Sandbox partition) providing this way not just a real end-to-end unbreakable encryption, but also non-interceptable messages by the reasons explained above. XCrypt has been already implemented as standard on XCell Basic v3 Stealth Phones, both on Basic and Advanced versions. Back in 2018, XCell Technologies has launched a new Stealth Phone series, based on legendary Nokia 3310 2017: XCell Basic v3 Stealth Phones. There are available both 2G and 3G global versions which are compatible with Canadian and Australian 3G mobile networks. Advanced Nokia 3310 Stealth Phone have the following functions: 1 - Call/SMS interception alert (active, passive and SS7 interception); 2 - IMSI Change which is transforming the phone in a real sophisticated counterintelligence weapon. IMSI Change function does not require any Internet connection, third party servers or monthly subscription. This special function runs locally on the phone (Sandbox partition), being a unique function which no other phones offer at this time. IMSI Change function allow user to change IMSI value (SIM registration number stored on the SIM card), by keeping the same phone number (MSISDN). How does it work? The phone will clone any SIM card inserted (please use only MNO SIM Cards) by using a Sandbox located app: IMSI Virtual Engine. Once cloned, the real SIM will be quarantined, being used instead a virtual SIM card which can change its IMSI by by generating valid IMSI’s. Please note that abusing this function can generate SIM network rejection (network dependent). Use it carefully. IMSI Change does not work automatically, as IMEI change works. The user should launch IMSI Change every time when a new IMSI is needed, generating a new virtual IMSI and then exiting the application. The new generated IMSI will be used only for the next outgoing or incoming call. After that, the phone will return to original IMSI. If a new IMSI will be needed, the whole process should be repeated. Please note that MSISDN (the phone number) will not change when using IMSI change function. IMSI change function will transform your Nokia 3310 Stealth Phone in one of most powerful communications weapon: you will literally have a new SIM (IMSI) for every single phone call. Use it with precautions. 3 - cryptoTRACERⓇ, which is a function that can detect lawful interception performed by SS7 Boxes (aka Network Switch Based Interception); 4 - Sandbox IMEI engine and other software components has been moved in a separate partition (Sandbox) in order to make them working faster and smoother. System restarting has been suppressed in case of any abnormal network characteristics (i.e. generated by IMSI Catchers/GSM Interceptors). 5 - Interception Instant Check Once launched, the function will start checking both Active and Passive interception, step by step. Regarding interception performed with Active/Semi Active GSM Interceptors, the phone will check: 1. BTS parameters 2. RSSI 3. Cell ID 4. LAC 5. ARFCN 6. Ki retrieving attempts (ciphering key stored on the SIM card). 7. Baseband attack attempts. Regarding interception performed by Passive GSM Interceptors, the phone will check: 1. Uplink. 2. Downlink. 3. Will ping HLR/VLR core network, computing network redundancy and abnormal ping delays. 4. In the end, will generate a Network Security Rating. 6 - C1/C2 monitoring By forcing cell reselection (C2 parameter), Active and Semi Active GSM Interceptors will force any cell phones to disconnect from home network and connect to the rogue BTS impersonated by the equipment. This is called also BCCH manipulation, being used by all modern GSM Interceptors. When launching this function, the phone will: 1. Extract C1 value, from serving cell. Will compute C2 value by using a special algorithm, the same used by any GSM network 2. Will look for at least other 6 neighboring cell towers, ordered by RSSI value. Will compare C1 to C2. 3. Will trigger alert if no neighboring cells are found (a clear indication that a GSM Interceptor is active within area). Will look for CPICH, RSCP and BCCH. 4. Will display forced handover attempts (if any). 5. Will display Channel lock fails (if any). 7 - Military grade SMS encryption. Please note that you need at least 2 units in order to use SMS encryption feature. 8 - Anti Interception: as long as phone is under surveillance by any means (no matter if IMSI Catcher, GSM Interceptor or SS7), voice calls and SMS will be blocked (both incoming and outgoing). 9 - Real Location Spoofing: user can hide GSM location by selecting the farthest BTS which phone is connected to, avoiding this way triangulation procedures widely used by law enforcement for location tracking purposes. Will work both when stationary and on the move. You see below actual pictures of special functions added to XCell Basic v3 Advanced Stealth Phone. Moreover, XCell Technologies added on XCell Basic v3 Advanced Stealth Phone an absolutely new breed of secure SMS which is not just encrypted but use a brand new technology patented last month, which makes SMS also non-interceptable. This is a revolutionary innovation called Multi-Layer Security Protocol - MLSP®, developed and patented by XCell Technologies. Taking advantage on GSM network architecture and SMS Transport Protocol, our SMS encryption technology is capable to send/receive encrypted and non-interceptable messages. Please note that for exchanging encrypted messages you need at least 2 phones: sender phone will encrypt the message and receiver phone will decrypt the message. MLSP® consist in: 1. Physical layer: encrypted text message. The phone will encrypt text messages by using following protocols: • RSA • AES 256 • Elliptic Curve (ECIES) 256 • SHA256 • Protected by ITSEC Evaluation level 3 2. Multi-layer routing and transport protocol. Encrypted SMS data is randomly segmentated and distributed in bursts by Application Port Addressing Technology, via discrete GSM channels which usually are not "listened" by mobile interception systems (IMSI Catchers, GSM Interceptors or StingRays), both in air interface (UM Interface in terms of GSM networks) and Abis, A and C-G mobile network interfaces. This way, SMS data which is usually sent over GSM Layer 1 (and widely intercepted on Layer 1) will be sent by using a combination of GSM Layer 1 and GSM Layer 2 (LAPDm). By consequence, no mobile interception systems (as GSM Interceptors) and lawful interception systems (SS7 interception also known as network switch based interception or interception by the help of network operator) will be able to intercept the whole message but only a few bursts which are encrypted anyway. 3. Metadata protection. Regular SMS metadata is not saved in a separate file (called a metadata file). XCrypt separate metadata and the data it describes (SMS encrypted text), sending metadata file in bursts over the network, by the same Port Addressing technology. Metadata is of little value without the data file (SMS) it relates too. At the same time, metadata makes the data more usable and therefore, more valuable. An encrypted text message with separate metadata file will reveal nothing about SMS sender and receiver. XCell Technologies SMS encryption application use a groundbreaking multi-layer technology to protect SMS from being intercepted and decrypted. As a unique encryption application, beside strong military grade encryption, XCrypt use a brand new patented technology in order to send/receive encrypted messages: discrete GSM channels or Multi-Layer Security Protocol®. That will protect not just encrypted text messages but also metadata which is not encrypted.
You can download the whole PDF document regarding MLSP@ technology and XCrypt applications, by clicking on image below: We are back after a long holiday, with a good news for stealth phones enthusiasts: back in 2018 XCell Technologies has launched a new product range: Law Enforcement Product Line. It comes with 3 different improved stealth phones: XCell Dynamic IMEI v4, XCrypt and XCell Pro. XCell Technologies claim that "new XCell Stealth Phone versions are not available on the website for public use, due to NDA agreements with certain law enforcement and intelligence agencies". However, private persons can buy small quantities by direct email orders. - XCrypt, a military grade SMS encryption Stealth Phone which combine active security measures (dynamic IMEI) and passive measures (SMS encryption). The phone can send/receive standard/unencrypted SMSs to/from any other cell phone. - XCell Dynamic IMEI v4 Stealth Phone: will come with newly added Security Suite (cryptoTRACER v2.0, Interception Instant Check, Sandbox v2 and C2 Monitoring). - XCell Pro: same as XCell Dynamic IMEI v4 Stealth Phone, but with a revolutionary and absolutely unique function: IMSI Change. This will be our next flagship product. A real weapon when used in a smart way. Also, cryptoTracer v3.0 will run on this device. Please see below a few specs: New launched XCell Stealth Phones are using a few patented and proprietary methods in order to detect call and SMS interception performed by any means, methods which have been developed close to our main clients - law enforcement and intelligence agencies. We have to admit that all new special functions has been not only suggested by them, but intensively tested by our main clients (the above ones) on various interception systems before public release. Moreover, XCell Stealth Phone has positively passed security audits from 3 different third party security audit companies. We are proud to say that our programmers and engineers, former or active IMSI Catcher and GSM Interceptor developers has done their best, releasing not only the most secure cell phones, but an unique piece of technology in the field of anti-interception devices, condensed in a innocent look like cell phone. Used in a smart way, XCell Stealth Phones can be a real weapon in tactical field. About Interception Systems 1. Active and semi active interception is easily detected due to the method by which this interception is done. The handset will detect any lack of standard GSM encryption (A5/1) generated by any active and semi active interceptors. 2. Newest GSM Interceptors, instead of "no ciphering" (A5/0), will lower encryption level from standard A5/1 to weaker A5/2 encryption algorithm (which can be decrypted in real time) managing this way to trick most of "secure" devices that claim to detect interception. XCell Stealth Phones will trigger Interception alert whenever will detect such low encryption, by displaying a yellow icon lock on top of the screen (instead of green lock icon): No other secure phones are capable to detect and display this kind of critical information.
However, most used interception systems nowadays are active and semi active (most of them are mobile systems), due to the high rate of success when it comes to call interception and also because interception warrants are not really required. 3. Lawful interception (also known as network switch based interception, SS7 interception or interception based on operator help) is made by using a special hardware installed on operator side at HLR/VLR level or most common at SS7 level (network switch), by law enforcement agencies. When a phone call or SMS is diverted by such hardware, will generate a specific delay due to hardware latency. Our proprietary algorithm called cryptoTRACER® is detecting this latency, alerting user when a phone call is monitored by SS7 means. Special phone functions, explained
When enabled, Anti Interception function will simply block any outgoing and incoming calls and SMSs, as long as interception is detected by the phone. The phone will remain silent during interception attempts. 5. UnPing (available only for XCell Pro and XCell Dynamic IMEI v4) In order to locate the phone, law enforcement are sending to the phone so called Location Tracking Pings (LTP), which basically are malformed SMSs (invisible on ordinary cell phones, no matter the brand, price or technology used), usually by using GSM network. In response to received ping, an ordinary phone will send back his GSM location data (not to be confounded with GPS tracking) consisting in tower Cell ID data, which actually means the tower GPS position on which the phone is connected to. When UnPing function is enabled, XCell Stealth Phone will: a. trigger alerts whenever a Location Tracking Ping is received b. block responses to received LTP, hiding this way the phone location. Certain special settings are involved. Location tracking alerts are displayed on phone home screen, being also stored on a text file. 6. Kc (ciphering key) extraction alert (available only for XCell Pro and XCell Dynamic IMEI v4) GSM Interceptors (semi active ones), in order to decrypt intercepted phone calls, need to know ciphering key (Kc) which is stored on the SIM card. In order to get Kc off the SIM, a GSM Interceptor will send to the phone so called challenges (special pings, other than LTP), to which the phone will reply with parts of ciphering key. Depending on GSM Interceptor type and brand, 5 to 20 pings needs to be sent to get a complete ciphering key. XCell Stealth Phones will alert the user whenever such a ping is received, displaying alerts on phone home screen. Alerts history is saved on a text file. 7. Channel lock (available only for XCell Pro and XCell Dynamic IMEI v4) A cell tower and a mobile phone are communicating by using a pair of radio channels (uplink and downlink), called ARFCN. Every cell tower is using different ARFCN, because of the GSM network requirements. When a cell phone moves from a cell tower on another, will change ARFCN (which is called handover). An IMSI Catcher or GSM Interceptors which basically are fake cell towers, will add a new ARFCN to local GSM network, in order to force the phones within area to connect to the “new cell tower”, performing this way call interception. When enabling Channel lock function, XCell Stealth Phones will lock on a certain real cell tower, preventing this way a connection to any other cell tower, including fake ones (IMSI Catchers, GSM Interceptors). More info on User Manual. Phone handover will be blocked, so the phone will remain connected on the real GSM network. 8. Location spoofing (available only for XCell Pro and XCell Dynamic IMEI v4) Mobile phone location tracking is based on the cell towers on which the phone is connected to. A cell phone can “see” 6 neighboring cell towers at a time (or less, depending on the area), and law enforcement is using this info in order to calculate accurately the cell phone location (+/- 5 meters) by using so called GSM triangulation procedures. XCell Stealth Phone users can effectively hide (spoof) the real phone location, by using this special function. The phone will spoof location whenever is static or on the move, by randomly connecting on cell towers. This way, the phone will appear to be 1 to 10 Km away from its real location (depending on the network cell towers density). For location spoofing, XCell Stealth Phones does not need to use Internet connection and/or third party servers, being a built-in feature. More info on User Manual. Also, XCell Stealth Phones have no GPS modules, adding this way an extra security layer. 9. TMSI monitoring (available only for XCell Pro and XCell Dynamic IMEI v4) Because IMSI (SIM card unique identifier) sending out to the network should be prevented for security reasons, the network will allocate instead IMSI, a temporary IMSI called TMSI. Based on GSM regulations, TMSI have to change on every phone restart, and when the phone is changing LAC (Location Area Code). Once connected to a GSM Interceptor, the phone will display the same TMSI after restarting, due to low computing capabilities of the GSM Interceptor, compared with a GSM network. If there are any doubts, the user can restart the phone and checking if a new TMSI pops up on the home screen. If not, that means the phone is connected to a fake cell tower, being at risk. This way, the user can instantly check out of the phone is connected to the real network or to a GSM Interceptor. 10. Clear call log (available only for XCell Pro and XCell Dynamic IMEI v4) The phone will automatically clear call log, so no call history will be available in case of forensic analysis. 11. Auto call recording (available only for XCell Pro and XCell Dynamic IMEI v4) The phone will automatically record every single phone call, saving audio files on phone internal memory or SD card. There is no notification recording at the beginning of the call, or an audible beep-tone for secret recording. Own call recordings are useful when audio editing is used on actual recordings, changing the meaning of the conversation (law suits). 12. SMS military grade encryption (available only for XCrypt) XCrypt it’s a special software application used to send/receive two kind of messages: standard and encrypted SMSs. Since standard SMSs can be sent/received to/from any other cell phone, encrypted messages can be exchanged only between two or more XCrypt Stealth Phones. Because XCrypt it’s a part of Operating System and does not run as a stand alone application, it is not possible to decompile or reverse engineering the obfuscated code, in order to find out which encryption algorithm is used, in order to attempt SMS decryption. XCrypt does not use for encryption Internet connection and third party servers, but a special partition (Sandbox) that run on the phone. 13. Forensic bulletproof (available for XCell Pro, XCell Dynamic IMEI v4 and XCrypt) The phones are protected against forensic analysis by volatile USB filters. No forensic device can extract any data or files off the phone. Once connected to a forensic device, PC or service box, volatile USB filters will trigger motherboard self-nuke, and the phone will get in protected mode (permanent boot loop) due to bootloaders auto-delete. If the phone is accidentally connected to a PC for charging purposes, the self-nuke mechanism will be triggered. Only provided wall chargers should be used for charging, being paired with the phones. Security Suite On new launched XCell Stealth Phones we have added a new section: Security Suite. Along with other special functions, all other functions contained by Security Suite run in a separate partition (Sandbox) for a faster operation. 1 - IMSI Change which along with IMEI change function is transforming the phone in a real sophisticated counterintelligence weapon. IMSI Change function does not require any Internet connection, third party servers or monthly subscription. This special function runs locally on the phone (Sandbox partition), being a unique function which no other phones offer at this time. IMSI Change function allow user to change IMSI value (SIM registration number stored on the SIM card), by keeping the same phone number (MSISDN). How does it work? The phone will clone any SIM card inserted (please use only MNO SIM Cards) by using a Sandbox located app: IMSI Virtual Engine. Once cloned, the real SIM will be quarantined, being used instead a virtual SIM card which can change its IMSI by by generating valid IMSI’s. Please note that abusing this function can generate SIM network rejection (network dependent). Use it carefully. IMSI Change does not work automatically, as IMEI change works. The user should launch IMSI Change every time when a new IMSI is needed, generating a new virtual IMSI and then exiting the application. The new generated IMSI will be used only for the next outgoing or incoming call. After that, the phone will return to original IMSI. If a new IMSI will be needed, the whole process should be repeated. Please note that MSISDN (the phone number) will not change when using IMSI change function. Used in conjunction with IMEI change, IMSI change function will transform your XCell Stealth Phone Pro in one of most powerful communications weapon: you will literally have a new phone (IMEI) and a new SIM (IMSI) for every single phone call. Use it with precautions. 2 - cryptoTRACERⓇ, which is a function that can detect lawful interception performed by SS7 Boxes (aka Network Switch Based Interception); 3 - Sandbox IMEI engine and other software components has been moved in a separate partition (Sandbox) in order to make them working faster and smoother. System restarting has been suppressed in case of any abnormal network characteristics (i.e. generated by IMSI Catchers/GSM Interceptors). 4 - Interception Instant Check Once launched, the function will start checking both Active and Passive interception, step by step. Regarding interception performed with Active/Semi Active GSM Interceptors, the phone will check: 1. BTS parameters 2. RSSI 3. Cell ID 4. LAC 5. ARFCN 6. Ki retrieving attempts (ciphering key stored on the SIM card). 7. Baseband attack attempts. Regarding interception performed by Passive GSM Interceptors, the phone will check: 1. Uplink. 2. Downlink. 3. Will ping HLR/VLR core network, computing network redundancy and abnormal ping delays. 4. In the end, will generate a Network Security Rating. 5 - C1/C2 monitoring By forcing cell reselection (C2 parameter), Active and Semi Active GSM Interceptors will force any cell phones to disconnect from home network and connect to the rogue BTS impersonated by the equipment. This is called also BCCH manipulation, being used by all modern GSM Interceptors. When launching this function, the phone will: 1. Extract C1 value, from serving cell. Will compute C2 value by using a special algorithm, the same used by any GSM network 2. Will look for at least other 6 neighboring cell towers, ordered by RSSI value. Will compare C1 to C2. 3. Will trigger alert if no neighboring cells are found (a clear indication that a GSM Interceptor is active within area). Will look for CPICH, RSCP and BCCH. 4. Will display forced handover attempts (if any). 5. Will display Channel lock fails (if any). XCell Pro, XCell Dynamic IMEI v4 and XCrypt comes in 3 flavors:
On demand, XCell Technologies provide the following: - unbranded or customized user manual (no reference to XCell); - unbranded cell phones (hardware and software) and boxes (no XCell logo). - customized cell phones (hardware and software) with reseller logo. Full phone customization (special branding) involve an extra payment of 2500 euro. This include: - welcome screen (with your company logo and URL) - welcome animation (your company logo animation) - shutdown animation (your company logo animation) - phone home screen with your company logo. On customer request, Stealth Phones can be delivered without any brand name, in generic boxes and without any reference to the XCell Technologies. We can print on the phone and box any brand name you want (brand name of your business for example, or a trade name chosen by you). Started few years ago, our website and blog has been visited by many people. Some of them sent us messages saying that the info contained by the website has been quite helpful when choosing a stealth phone to buy. Also, existing users of fake stealth phones has abandoned their fake phones, avoiding this way many troubles generated by the lack of security which those phone have. We've got a lot of messages coming from this poor people, most of them telling us about how difficult was to get a money refund from the sellers that sell fake stealth phones, no matter if they sell the phones on eBay, online classifieds or dedicated websites. Also, they told us about lack of customer service, replacement of faulty phones and non professional explanations about how the phone work and how to use it on a daily basis You can see below only few examples:. There is just a single conclusion: avoid buying and using stealth phones that have doubtful or shady origin, and buy only form certified manufacturers or official distributors.
On 16th January 2016 XCell Technologies has announced two new releases for the well known Basic version. First of them, XCell Basic v2 that comes now with with a new added SMS Encryption function.  XCell Basic v2 XCell Basic v2 Changes and improvements: - improved SS7 (lawful interception) call interception detection, based on our cryptoTRACERⓇ proprietary algorithm. - improved call interception detection performed with the newest GSM Interception Systems. The phone has been successfully tested against all major interception products like Rohde&Schwarz, Septier, IBIS, EL/K-7066, PGIS, Harris Corp., GSS ProA, HCI-101, VME Dominator. - has been added SMS Encryption option (AES based), allowing users to send/receive encrypted messages between two XCell Basic v2 Stealth Phones. - improved GSM Interceptor Proximity Alert. Please note that the phone will not detect Fully Passive GSM Interception Systems. - the phone has been intensively tested, positively passing three different security audits from third party companies, before official release. Has been successfully tested by our major law enforcement clients. Firmware update: 12.01.2016. Special features: - GSM Interceptor Proximity Alert . On stand by mode the phone displays a warning icon (open lock) in case of monitoring by GSM Interceptor - Call Interception Alert. During the call, the phone will display an icon (open lock) in case of active interception. No sound or vibration alert. - Forensic Bullet-Proof The XCell Basic phone cannot be accessed and investigated by forensic software and hardware. Firmware cannot be read/wright or cloned by unlocking boxes. The phone cannot be accessed, read or analysed by any mobile forensic eqipment. Physical extraction and file system extraction is blocked by security filter. The phone does not need any extra settings. It work as it is.  The first Dual SIM Basic v2 Stealth Phone has been now launched by XCell Technologies. Comes with the same features as XCell Basic v2 Stealth Phone, but without encrypted SMS.The phone use has been even more simplified compared to predecessor v1: alert icon will show up only when phone calls are being intercepted, or when the phone will detect an active IMSI Catcher/GSM Interceptor within area. Also, has been removed from the home screen any graphics or signs that can indicate any network monitoring process, for even a more discrete use. Please note that Special Functions are only available when using SIM1, being unavailable for SIM2. However, SIM2 is fully operational and can be used as usual. Firmware update: 12.01.2016. Special Features: - GSM Interceptor Proximity Alert . On stand by mode the phone displays a warning icon (open lock) in case of monitoring by GSM Interceptor - Call Interception Alert. During the call, the phone will display an icon (open lock) in case of active interception. No sound or vibration alert. - Forensic Bullet-Proof The XCell Basic Dual SIM v2 Stealth Phone cannot be accessed and investigated by forensic software and hardware. Firmware cannot be read/wright or cloned by unlocking boxes. The phone cannot be accessed, read or analysed by any mobile forensic equipment. Physical extraction and file system extraction is blocked by security filter. The phone does not need any extra settings. It work as it is. Photos courtesy of XCell Technologies.
Recently discovered new stealth phones scam on blackstone-security.jimdo.com have some pretty funny "pluses" than other competitor scammers. They claim that the stealth phone they sell have no more that 10 (yes, ten!) "clandestine operational functions", as you can see on the picture above. There is the same old scam: a cracked and non working firmware installed on wrong cell phones (Samsung G600) that will give you only a cell phone that looks like a stealth phone but with no working functions. Sounds familiar? Sure it does: we have revealed this scam since last year. This sneaky scammer is trying to mislead buyers by selling the same 7 functions stealth phone firmware installed on Samsung G600 cell phones, by simply inventing some additional functions. The firmware used to make his counterfeit stealth phones is absolutely the same as the one you can download for free from our website, for testing purposes: click here to download 7 functions Samsung G600 firmware. Lame: copy/paste scammer What else the lame scammer did? Well, proving that he is a lazy ass, an ignorant when it comes to websites or just a little theft (we think that he is a bit of all), he stole the text and pictures from the x-cellular.com website. Looks familiar? Sure it does: there was another scammer who stole text and pictures from the original manufacturer website, called Sohail Hussain aka Steven Adams (Jd Mobile Unlocking Service, private held company). Click here for more info. Selling fake stealth phones is something, but stealing from others is something else. But when you put all together this facts, the only conclusion you can get is that the scammer have no idea about how things are done on cellphone interception field and have no idea on how stealth phone works. Buying from this scammer is like buying medicine from a quack and not from a pharmacy. We had a bit of fun with this copy/paste scammer: seeing that he copied also the "About Us" text from x-cellular.com (including pics) and pretending to have a "background in signal intelligence and direct experience of working with GSM, Security phones developers had a significant head start", we have sent him a mail asking simple programming questions, just to make sure he knows at least Java programming language which is also the language used to build the stealth phone firmware. No reply whatsoever, and we'll not expect one by obvious reasons. There are no developers related to this scam. In fact there is no team at all, but only a scammer trying to fool people. And sure, they claim (actually a text copied from x-cellular.com website) that "the development staff consists of individuals spanning different languages, regions, industries, and nationalities. We are experts in offensive GSM security , cybercrime and security intelligence." Experts... The scammer is selling also his counterfeit stealth phones on eBay, under the nickname www-kpex-de And yes, the scammer call all this scams as "Advanced Solutions". No doubt, those are solutions to get some money from ignorant people. What other scam he sell? Remember the Anonymous SIM card scam that we have revealed last year? Well, based on the principle "monkey see, monkey do", this scammer is selling sell so called anonymous SIM cards, as the other scammers do. No doubt, there is one thing that scammer knows: how to copy others. And he think that is the business key to success. Or at least to have some pocket money that comes from uninformed or ignorant buyers. You can have the complete picture of the scam developed on blackstone-security.jimdo.com when you realize that the webstore has been built on a free platform. (jimdo.com). Why that? Someone who sell security solutions (and not any solutions but "advanced solutions" as he claim) cannot afford a domain name and a decent website when (probably) selling products worth hundreds of euro? Or does he hide his ass under the anonymity offered by a free platform website? Whatever the reasons are, you have to avoid buying from this scammer. A clear thing, you can not buy security from someone who steal the others hard work, selling cracked/unlicensed firmware and having no idea about how cell phone interception works, pretending to be "a team of skilled programmers". Update (22nd November 2015): Realizing that his scam has been revealed, the scammer did the same as the one who ran imeichanger.com, antitap.com and secretgsm.com: has closed down the website located at http://blackstone-security.jimdo.com/ Following our marketing advice, the scammer has bought from jimdo.com his own domain name (antispymob.com), and now he is redirecting the visitors to his new website, called http://www.antispymob.com/ Apparently the scammer will continue to run his scams on this new website. We will keep you informed about future scam development. On the scammer eBay account (User ID www-kpex-de) he uses a stolen picture from x-cellular.com website, trying to mislead buyers that the fake phones he sell are enabled with "New updated GUI interface". Despite the fact that he have no idea what GUI means, he is fool enough to use the Xcell logotype on the phone homescreen when selling his fake stealth phones. This is why anyone should ask him before buying about XCell security seals on the phone backside. Just ask him to send you a photo with the phone backside, along with phone IMEI number. Then you can simply ask XCell guys is that details are genuine or not. Simple as that. Just to make sure that we're not wrong, we have contacted XCell Technologies, asking if they have any reseller within Germany and The Netherlands. The answer was negative, there is no XCell reseller for these counties. You can do the same, asking about Germany and The Netherlands XCell reseller: you will get the same response. However, the scammer is trying to hide behind a company called Ennetcom (http://www.detectnu.nl/?page=http%3A//detectnu.home.xs4all.nl/opdrachtform.htm) pretending that the fake stealth phones he sell are manufactured by detectnu.nl. And here comes the ridiculous lie: how can a company like Ennetcom that sell only BlackBerry secure solutions (and not even the phones itself), a company that is not talking nor offer any dynamic IMEI phones, manufacturing dynamic IMEI phones and sell them only on a eBay account and (until few days ago) on an obscure and dubious web page?! You cannot see any references about dynamic IMEI phones on the Ennetcom (detectnu.nl) web page. Lets be honest: Ennetcom (detectnu.nl) are not at all manufacturers but only a BlackBerry solutions resellers, and nothing else. No doubt, there is a logical fracture in the scammer thoughts: there is no manufacturer that is not selling his products on his own website, but only other companies products. Make sense to you? And yes, there is another stupid thing that the scammer is trying to promote: a stealth phone which have the XCell Technologies logotype (the famous X), manufactured by detectnu.nl, a company that in a strange mode, does not say anything about dynamic IMEI stealth phones and actually does not produce anything but only reselling Blackberry secure services. Does it make any sense for you? As a "very serious" and professional business that "produce" sell a lot of "secure" cell phones, guess what else this scammer is selling to make some pocket money: paintball masks and USB cables. A veritable businessman that is doing businesses on a large scale. Expect a professional customer service and explanations from someone that is selling this king of products? We hope not. One last thing: a website will never be a manufacturer, as the scammer claim. But only a manufacturing company can produce something. A website is only a marketing platform, a web store.
Trying to dismantle the scam behind antitap.com, imeichanger.com and secretgsm.com, we found out the following facts:
More blog entries about the scams on antitap.com, imeichanger.com and gsmsecret.com: How all this started: previous scams Please note that most of the screenshots below has been taken from gsmhosting.com forum and few other websites where the scammer is pretty active. The amateur scammer behind antitap.com, imeichanger.com and secretgsm.com websites is an italian guy that lives in Monaco, sometimes reported in Swiss. He uses the nickname "cryptone" on most forums since 2008, and sometimes "Luca" only on italian forums. Early years In his early years he has started his scams as spy-phone software dealer, on the black market. Back in 2008 he deals the illegal software only on italian forums and websites, taking advantages on italian people that - as you probably know from your trips or interactions - are pretty ignorant when it comes to english language. So, they had to pay a price for that ignorance, buying spy-phone software at high rates. As you know, selling and using spy-phone software is considered to be illegal in most of the countries, even when it comes to spy your own wife or child. Then in 2008 he has discovered gsmhosting.com forum, starting to post offers for spy-phone software. Like now, the scammer has used in the past multiple sites for selling illegal software: nokia-spy.com/index.html bberryspy.com spyphonegenerator.weebly.com Nokia 1100 scam, a short story for the scammer Bank fraud and selling fake phones - this scammer gets in  In case you weren't already convinced of a certain model of Nokia 1100's can be used for bank fraud by reprogramming the phone in a way that allow the attacker to extract your mobile transaction authentication number -- provided you live in a country like Germany or Holland that use mTANs -- and use it to get into your bank account and transfer funds. So, this opportunity sounds good enough to the scammer to get involved in it, making some money by fooling people. When he first hear of this scam, posted on gsmgosting.com forum that he want to know more about this scam: In a short time the scammer realize that he can exploit the market demand for Nokia 1100 by buying cheap Nokia 1100 which are not RH 16-18 series, and counterfeit the software or even the backside IMEI label: Because he didn't succeed to counterfeit Nokia 1100 RH by software means, he has simply counterfeit the backside IMEI label: And then he just start selling counterfeit Nokia 1100 on forums, web shops and eBay: Preparations for change IMEI phones scam You probably know that the scammer behind antitap.com, imeichanger.com and secretgsm.com is posing now in a security professional, running a bunch of websites and selling high grade security related products pretending that he knows how that products work and how cell phone interception work. Just to have fun on his approach, vision and knowledge regarding cell phone interception, please have a look below, on how he name an IMSI Catcher or GSM interceptor: "IMEI phishing machine". We think this is self explanatory and need no more proofs about his "professionalism". Do you expect professional customer support when buying and using a stealth phone from this illiterate when it comes to cell phone interception? We hope not. Then suddenly he have heard somehow about dynamic IMEI phones made by XCell Technologies. He couldn't probably afford to buy one to start replicate it, presuming that he know how to do it (which we doubt). So, he started to ask round for similar but cheaper ones: Decided to make money from nothing by fooling people, the italian scammer wants to sell even phones that apparently change IMEI (only on phone screen) and not in a real mode. This is yet another proof of the scammer intentions to fool people: The real story of antitap.com, imeichnger.com and secretgsm.com: At this stage, from our records comes out that he contacted a Bulgarian hacker and together they put money and bought an XCell dynamic IMEI phone, whose firmware was hacked and extracted by the Bulgarian hacker. The hacker name is Zlatin Penchev from Stara Zagora, and we have his complete story about how he cracked and extracted the XCell firmware and how starting to sell the cracked (and non working) firmware together with the italian scammer. In fact even the italian scammer admits he worked with a Bulgarian hacker: Obviously, he didn't lose the Bulgarian hacker contact: the hacker has dumped the scammer just because the scammer has no idea about how stealth phones should be replicated and sold to make some pocket money. So, the scammer has started to figure out by himself how to flash the cracked XCell firmware on a phone, in order to clone a real XCell stealth phone. But seems like his attempts to counterfeit XCell stealth phones were unsuccessful at first, because the scammer does not have the necessary knowledge nor quite right tools. Fake it to make it: please note that the same scammer has been caught in the past using fake G608 IMEI stickers on his fake G600 stealth phones, just to create the appearance of a genuine XCell stealth phone. More about that fake IMEI stickers, here. Because of using a cracked and non working firmware installed on the wrong platform (Samsung G600 instead of G608), there are a lot of malfunctions and bugs that starts from the moment of flashing (installing) the firmware on the phone: After his own statements, the italian scammer use the same empirical tool (Onenand downloader) to flash the cracked firmware on the phones, as the other scammer sells on eBay along with the cracked firmware (click here for details). So, no wonder that he got burned out his phones: Stealth phone scam in progress Despite the fact that the italian scammer sell counterfeit non working stealth phones, he start advertising on forums about his scam: He also sell counterfeit stealth phones on his main web shops: antitap.com, imeichanger.com and secretgsm.com. An interesting fact that demonstrates on antitap.com, imeichanger.com and secretgsm.com are being sold counterfeit non working stealth phones: please have a look on the thread dates: since 2013 the scammer sell stealth phones, but in 2014 he still ask for help in flashing stealth firmware on his counterfeit stealth phones. No need for more proofs, scammer own declarations are more than enough to demonstrate the scam. What other scams can you find on antitap.com, imeichanger.com and secretgsm.com? Buy cheap, sell high. This seems to be the the guideline followed by the italian scammer. Nothing bad up here, the wrong things and the scam starts when he consider himself nothing but a "legit producer", making confusions between producer and seller. We will not analyze his marketing strategies nor price policy since is not our business. But we will have a look on the products he sell. Anonymous SIM card scam We have posted already our conclusions on so called anonymous SIM card, on a previous blog entry. Click here for more details. Other so called "stealth phones" that he sell Before talking about other scams, you should know that all Android cell phones that he sell as "stealth phones" are not at all stealth, as scammer claims. The scammer is taking again advantages on unskilled and unknowledgeable people that have no clue about how cell phone works, how and what a software application can do, selling simple Android phones that the scammer has pre installed several free software applications that can be easily found in abundance on Play Store, by anyone.  Stealth Samsung S4 scam Stealth Samsung S4 scam Stealth Samsung S4 Duos scam. What the scammer did? Well, he simply installed on a standard Samsung S4 phone, a free app called Private Text Messaging & Calls. This app can be downloaded and used for free, from Play Store. Click here. Why paying more to a scammer since you can have all this for free, on your Android phone? What else he did? By using copy/paste, he added some text to his website, copied off the Play Store app page. This is how he launched his product called "Samsung S4 stealth Phone". Pretty easy, right? But not smart enough. We really wonder how many naive people he managed to fool until now. Please note that the phone does not have ANY anti tapping capabilities nor detection of call interception.  Stealth Samsung S5 scam Stealth Samsung S5 scam Stealth Samsung S5 scam. The same scam as above. The scammer has installed the same app (Private Text Messaging & Calls) on a standard Samsung S5. And nothing more. Download for free the app: click here. Please note that the phone does not have ANY anti tapping capabilities nor detection of call interception.  Encrypted stealth phone scam Encrypted stealth phone scam Encrypted smart phone scam This is actually a very cheap China made cell phone called DOOGEE TITANS DG150 3.5" (can be bought from here with only 75$) which is not encrypted at all, by default. The phone can be encrypted by the user, as any other Android device, for free. On this device, the italian scammer has installed the same free app called Private Text Messaging & Calls which can be downloaded from Google Play. Click here. The scammer is selling this device with 450€, making a good profit on ignorant people. Please note that the phone does not have ANY anti tapping capabilities nor detection of call interception.  Dual SIM stealth phone scam Dual SIM stealth phone scam Entry level dual sim burner phone: a scam. This is actually a cheap NGM feature phone called Stealth, that can be bought with only £91.00 from here. The italian scammer is selling the device with 250€. Please note that the device will not alert you when your calls and messages are being intercepted. The scammer just sell lies to you. Please note that the phone does not have ANY anti tapping capabilities nor detection of call interception.  Stealth iPhone 5 scam Italian scammer is selling ordinary iPhone 5 phones which he installed a free application called CoverMe Private Texting Messenger, which is similar to Private Text Messaging & Calls, available for Android devices, being released by the same developer - CoverMe Inc. You can download and install for free CoverMe Private Texting Messenger for iPhone: click here - iTunes link. No need to pay 650€ for an ordinary iPhone 5. Please note that the phone does not have ANY anti tapping capabilities nor detection of call interception.  Ultra Tough Anti Tapping Phone: scam Ultra Tough Anti Tapping Phone: scam Ultra Tough Anti Tapping Phone: scam The so called Anti Tapping phone sold by the italian scammer on his websites (antitap.com, imeichanger.com and secretgsm.com) is actually a cheap Android device made in China by OINOM, which can be purchased with only 299$ from Aliexpress.com: click here. Scammer price: 550€. The scammer has installed on this phones the same free app called Private Text Messaging & Calls which can be downloaded from Google Play. Click here. Please note that the phone does not have ANY anti tapping capabilities nor detection of call interception.  VHF Stealth Dual SIM Anti Tapping Phone: scam VHF Stealth Dual SIM Anti Tapping Phone: scam VHF Stealth Dual SIM Anti Tapping Phone: scam This so called Anti Tapping phone is actually a China made Android phone called Snopow M8 which can be bought from Aliexpress.com with only 199$: click here. Scammer price: 390€. The scammer has installed on this phones the same free app called Private Text Messaging & Calls which can be downloaded from Google Play. Click here. Please note that the phone does not have ANY anti tapping capabilities nor detection of call interception.  ZOPO anti interception phone ZP1000 Android: scam ZOPO anti interception phone ZP1000 Android: scam ZOPO anti interception phone ZP1000 Android: scam This so called "anti interception" phone can be bought for only 172$ from Zopo store: click here. Scammer price: 399€. The scammer has installed on this phones the same free app called Private Text Messaging & Calls which can be downloaded from Google Play. Click here. Please note that the phone does not have ANY anti tapping capabilities nor detection of call interception. ConclusionsAll three examined websites are selling counterfeit and/or non working phones (claimed to be stealth phones), along with free software applications for which the scammer asks for money.
We strongly advise you to keep away from all three websites: antitap.com, imeichanger.com and secretgsm.com. There is nothing that you can buy for your privacy and call security, but only scams and lies. in case that you been a scam victim on these sites, you might contact us for further assistance. Our advice: always buy the original. As we did, in the end of the day. Last update: 5th July 2015 A counterfeit stealth phone is a ticking bomb in your pocket. Unfortunately you find out that you have been fulled by the scammer when usually is way too late: you "stealth" phone has been wiretapped and you got busted. Following our investigations carried out in recent months, we have discovered several vendors that sell fake stealth phones. They sell counterfeit stealth phones both on eBay (using multiple accounts and nick-names) and on independent websites. We present our investigation results, hoping that the following info will be helpful when you decide to buy a stealth phone. So, we have identified the following scammers: 1 (location: Cork, Ireland) Name: Dave H., private individual Current Status: eBay scammer, online classifieds scammer Fraud: selling fake stealth phones Assigned Location: Cork, Ireland Address Information: temporarily unavailable Additional Info: temporarily unavailable 2 (location: Dublin, Saggart, Ireland) Name: Spystore Ireland Current Status: physical store Fraud: selling fake stealth phones Assigned Location: Dublin, Ireland Address Information: Mc Greggor House, The Fairways, Citywest Complex, Saggart, Co. Dublin Additional Info: temporarily unavailable 3 (location: Naas, Ireland) Name: lightning lofts (nick name used on classifieds), private individual Current Status: online classifieds scammer Fraud: selling fake stealth phones Assigned Location: Naas, Co. Kildare, Ireland Address Information: temporarily unavailable Additional Info: temporarily unavailable 4 (location: Newtownabbey, Northern Ireland, UK) Name: Sohail Hussain aka Steven Adams (Jd Mobile Unlocking Service, private held company) Current Status: eBay scammer, online classifieds scammer, online store scammer Fraud: selling fake stealth phones Assigned Location: Newtownabbey, County Antrim, Northern Ireland, UK Address Information: 3 Dillons Grange, Dillons Avenue, Newtownabbey, County Antrim, BT370HU Additional Info: A simple repair shop guy, that watched way too many 007 movies. fix.mobile.to.work, fixmob_fydy4156obf@members.ebay.co.uk, jdmobileunlockservice, http://gsminterceptor.co.uk/, hello@gsminterceptor.co.uk SPECIAL NOTE: A "fake it to make it" type of guy. This particular scammer is the actual seller of Siemens S65 stealth phone, on gsminterceptor.co.uk, eBay and other classifieds. Has sold in the past years fake Samsung G600 stealth phones, and now pretends that those phones are good for nothing, totally disregarding his former clients, who have been cheated anyway by buying fake Samsung G600 stealth phones. This is his newest scam: http://gsminterceptor.co.uk/product/siemens-s65sl75-untraceable-covert-updated-gsm-mobile-stealth-phone/ A funny fact: there is an Youtube movie ( https://www.youtube.com/watch?x-yt-cl=85114404&x-yt-ts=1422579428&v=jddDwzA2pq0 ) where he is trying to tell us that Siemens S65 phones are the best ones and Samsung G600 (and not G608, as genuine XStealth) are not good at all. But in the same time he contiune to sell Samsung G600 stealth phones on his website (http://gsminterceptor.co.uk/product/imei-phone/). It seems to be the most unimaginative, the most tricky and the most ridiculous of all scammers. Not confined only to deceive buyers, he steal from original stealth phones manufacturer (XCell Technologies) all that he find to fit his needs: text content, technical explanations, photos. Everything for deceiving his customers. Here's what we have discovered, to his shame: he stole the soundtrack from one of the XCell Youtube clips (https://www.youtube.com/watch?v=Rtnc-5PdJ7I). Please notice the specific sound of XCell original intro clip, on the video below: And here is the video that use the soundtrack stolen by Sohail Hussain: Based on his habits, we expect from him to steal even the soundtracks from our Youtube clips. But by far, the worst thing is that he steals money by cheating his customers, selling fake products. The question is: can you trust someone and buy security from him (stealth phones, etc.), can you put your calls confidentiality in the hands of somebody that lends itself to such petty theft? Of course not. Our advice: avoid shopping from gsminterceptor.co.uk, and anything that is relate to fix.mobile.to.work and jdmobileunlockservice. If you are in doubt, please contact us. Seems like his customers start to complain about product that he sell: http://forum.gsmhosting.com/vbb/f88/siemens-s65-imei-change-331494/ 5 (location: Birmingham UK) Name: Chow Current Status: online shop scam (anti-interceptor.com), online classifieds scammer Fraud: selling fake stealth phones Assigned Location: Birmingham, UK Address Information: Birmingham City Centre, West Midlands, UK Additional Info: anti-interceptor.com, big-boyz-toyz, gadgetboy1979@gmail.com Looks like some anti-interceptor.com buyers has finally figured out that the fake phones sold by this scammer does not work: Complaint against anti-interceptor.com fake stealth phones Click here for more info. 6 (location: Thetford, Norfolk, UK) Name: jaaamm1976 (nickname) Current Status: eBay scammer, online classifieds scammer Fraud: selling fake stealth phones Assigned Location: Thetford, Norfolk, United Kingdom Address Information: temporarily unavailable Additional Info: temporarily unavailable 7 (location: Wirral, Merseyside, UK) Name: mobile.phones.2u (nickname) Current Status: eBay scammer, online classifieds scammer Fraud: selling fake stealth phones Assigned Location: Wirral, Merseyside, UK Address Information: temporarily unavailable Additional Info: temporarily unavailable 8 (location: Manchester, UK) Name: auction2home (eBay nickname) Current Status: eBay scammer, online classifieds scammer Fraud: selling fake stealth phones Assigned Location: Manchester, UK Address Information: temporarily unavailable Additional Info: temporarily unavailable 9 (location: Monaco, Monaco) Name: Vittorio Ossola aka Luca (on italian forums) or Cryptone (on forum.gsmhosting.com) Current Status: eBay scammer, online classifieds scammer, online shop scam Fraud: selling fake stealth phones Assigned Location: Monaco, Monaco Address Information: temporarily unavailable Additional Info: www.secretgsm.com, antitap.com, imeichanger.com, Bergamo, Lodi, Swiss. More blog entries about the scams on antitap.com, imeichanger.com and gsmsecret.com: 10 (location: Ural, Krasnoyarskiy Kray, Russian Federation) Name: Vasili Loginov Current Status: online classifieds scammer Fraud: selling fake stealth phones Assigned Location: Ural, Russian Federation. Address Information: Ural, Krasnoyarskiy Kray, Russian Federation Additional Info: temporarily unavailable 11 (location: Monaco, Italy) Name: Vittorio Ossola aka Luca (on italian forums) or Cryptone (on forum.gsmhosting.com) Current Status: eBay scammer, online classifieds scammer, online shop scam Fraud: selling fake stealth phones Assigned Location: Monaco, Monaco Address Information: temporarily unavailable Additional Info: www.secretgsm.com, antitap.com, imeichanger.com, Bergamo, Lodi, Swiss. He own www.secretgsm.com, antitap.com, imeichanger.com We have found a funny marketing strategy used by this particular scammer. Back in 2013, on a strange promotion on his eBay page, Mr. Ossola Vittorio (aka agte062010 or cryptphone - few of his eBay accounts) has offering a funny bundle: a fake stealth phone, a doggy anonymous SIM card and... a t-shirt. We wonder what was the text on the shirt? "I'm cool because I can not be intercepted?" attracting this way the law enforcement agencies attention? Please notice that we have already warn you about this particular scammer, a while ago. Please read here. This is what we have found on the Internet, by searching data about imeichanger.com: More blog entries about the scams on antitap.com, imeichanger.com and gsmsecret.com: 12 (location: Czech Republic) Name: SHX Trading S.R.O. Current Status: Alibaba.com scammer, online shop scam Fraud: selling counterfeit stealth phones Assigned Location: Czech Republic Address Information: Svatoslavova 17, Praha 4, Czech Republic Additional Info: http://stealthtronic.com, http://www.alibaba.com/product-detail/Stealth-Mobile-untraceable-cell-phone-change_170458198.html Stealthtronic.com: stealth phone scam in progress: As you can already see, this scammers are using a product picture that is not a Samsung device but a Sony Ericsson, misleading or (better case) confusing their buyers. On their website, they pretend to "manufactures variety of security and surveillance products", which in fact are not made or at least assembled in Czech Republic. A brief look at the products list sold on website, will clarify that all products are manufactured by Chinese companies, and not by SHX Trading SRO. When it comes to security products, misleading customers is a practice not only wrong, but also reprehensible. 13 (location: Philippines) Name: AUDIO VIDEO INTELLIGENCE CORPORATION. (AVI) Current Status: Alibaba.com scammer, online shop scam Fraud: selling counterfeit stealth phones Assigned Location: Manila, Philippines Address Information: 61 WEST CAPITOL DR. PASIG METRO MANILA Additional Info: http://bobster.fm.alibaba.com/ 14 (location: Lithuania) Name: danielius2010 (eBay account) Current Status: eBay scammer Fraud: selling fake stealth phone firmware Assigned Location: Lithuania Address Information: temporarily unavailable Additional Info: eBay account 15 (location: United Kingdom) Name: swetroop (eBay account) Current Status: eBay scammer Fraud: selling fake stealth phone firmware Assigned Location: London, UK Address Information: temporarily unavailable Additional Info: eBay account 16 (location: Taiwan ROC) Name: OneTech International Co. LTD (website) Current Status: online scammer Fraud: selling fake stealth phone firmware Assigned Location: Taiwan, ROC Address Information: 15F - 7, No.3, Lane 226, Sec 2 of Round West Road , Chungli City, Taoyuan County Additional Info: selling also illegal software as spy phone generator software Located in Taiwan ROC, the scam company is selling counterfeit stealth phones on www.onetech.com.tw Pretending to be a "Worldwide business experience you can trust", this company is selling fake stealth phones, using on the website stolen text and pictures from the original manufacturer, XCell Technologies. All other products sold on the website are also questionable. Our recommendation: just avoid this website. Update 21.10.2015 17 (location: Germany, UK, The Netherlands) Name: blackstone-security.jimdo.com Current Status: online scammer / eBay scammer Fraud: selling fake stealth phone firmware Assigned Location: Germany, UK, The Netherlands Address Information: 27 Old Gloucester Street, London, WC1N 3AX Additional Info: related to Mainland & Affiliates AG Limited. Selling fake stealth phones on eBay as www-kpex-de What other tricks they use?1. "Updated version" and "v4" trick Trying to sell an outdated, unstable and cracked version of stealth phone, a few sellers are using some ridiculous tricks, thinking that they would fool the buyers. Borrowing random phrases and words from marketing techniques, they try to present their cracked version of stealth phone as an "updated" one. In fact what they sell it is an old cracked and unstable version. Of course, next to the "updated" you will find the current year, to maximize the scam effects. The guy behind antitap.com, imeichanger.com and secretgsm.com has "updated" his scam in May 2015, due to XCell Dynamic IMEI v3 new release. Now he sell no more than "v4" stealth phone version, a nonsense with no factual support. Why this? Well, there is a simple and straight forward explanation: since XCell Technologies has recently released the real v3 Stealth Phone (please see their promo video), the scammer think that by simply claiming that he sell the newest version (v4), he will boost his sales. Since XCell Technologies - the real manufacturer - is clearly showing what the differences are between previous version (v2) an actual version (v3) on their videos (video 1, video 2) and webpage, the scammer is just stating that he sell v4 version. Only words with no facts behind. Not even a few pictures to support false claims. Moreover, he has used the same stolen pictures on phone description (please note that picture shadow used by XCell Technologies). Just to have fun on what he will find appropriate to explain in what exactly consist the changes that his "v4" is having you might challenge him to reply to your questions. Because we did and we had a lot of fun. Read more here. As a conclusion, what you should be sure is that there is no real "v4" version, but only words, a ridiculous and strange marketing strategy to sell something fake and obsolete.Please note that the only software updates are made available to the general public on the original manufacturer's website (XCell Technologies), on News section. Actual version: 3.0. Just to have a little bit fun with the scammers, you can try to ask about previous versions, in what exactly consists the current updates and bugs that have been fixed. Being neither programmers nor engineers, you will definitely have fun on their responses, as we did ourselves. More blog entries about the scams on antitap.com, imeichanger.com and gsmsecret.com:
2. SMS encryption software trick These scammers claim that they sell some kind of bundle, a "stealth phone" having installed a software application that encrypts SMS. This is not a lie. But think about it: what to do with just a single phone that has an encryption application installed ?! SMS software encryption apps only works in tandem: first one encrypts and the other one decrypts the ciphertext sent by the first app. It's that simple.You will need at least two phones that use the same software, so that one phone will send an encrypted SMS, and the other one will receive it, will decrypt and it will display the SMS in plain text format. By buying a single phone with a single software application, SMS encryption is absolutely useless. 3. Fake product reviews Proving a poor knowledge of his own website and confusing the website and blog notions (is having mitigating circumstances, being only a repair shop guy), Mr. Chow (anti-interceptor.com owner) has inserted fake product reviews, as blog entries: many "clients" (no doubt, fake buyers) refers in a funny way to blog and not to the product that they eventually bought, (have fun here). But surprise: on the blog page, instead of a proper blog you will find a product presentation page. So what blog are "clients" talking about? How funny can that be? And how dumb can be? You will appreciate. Obviously it is all a hoax, a scam designed to mislead customers who do not have enough information about stealth phones and especially for those that are looking for cheap prices. By the way, try to post something. Anything. And check up the result. Have fun. 4. Why there are no videos certifying that the phone work? XCell Technologies and their authorized resellers are the only ones who have posted videos demonstrating that the special functions of the phone are working. Why not these vendors do the same? The answer is simple: the fake stealth phones special functions simply does not work as described. It is not hard to find a SIM card that is intercepted and then make a film. Even for us was pretty easy to do that: you can watch the movie made with an authentic XCell Dynamic IMEI v2 Stealth Phone. 5. Siemens S65/SL75/r32 stealth phone legal issue and other problems
Before talking about Siemens legal issues, we have to talk about the phone capabilities. Assuming (pretty unlikely) that the scammer would sell the original version (by the way, the authentic Siemens S65/SL75 version is developed and sold by Endoacustica at 5000 euro) , here are the necessary observations about this phone: Supposing that this phone works as described, IMEI change being not reversible is not at all an advantage, as it strives to explain the scammer in several of his Youtube films. Here's why: From technical point of view, for an GSM Interceptor does not matter whether the phones will change its IMEI temporarily or permanently. Called also IMSI Catcher, for an GSM Interceptor are important only the IMEI and IMSI that are "captured". Depending on captured IMEI and IMSI, the phone calls will be intercepted. An GSM Interceptor does not care whether an IMEI is or is not reversible. Simple as that. Obviously, in this case the explanations about interception and how can this be avoided are being served with "professionalism" by a... repair shop guy. Its ridiculous explanations derives from a very low level of technical understanding of the whole interception phenomenon. The risk of giving ridiculous explanations on the subject of which you have no idea, is a pretty big one. Claiming that irreversible IMEI change is crucial throughout interception equation, the repair shop guy does not know that IMEI and IMSI are captured off the air by any GSM Interceptor, no matter if the IMEI is or is not reversible. He probably imagine that GSM Interceptor will somehow knock on the door and will asks the target to show the phone and the associated IMEI. Only in this case (which is obviously impossible), an irreversible IMEI can save the situation. You can easily recognise the wrong approach of a repair shop guy when it comes about cellular interception. But let's analyze Siemens S65/SL75, the "Untraceable Covert Updated" phone (as the scammer advertise), assuming that it is not a counterfeit one. All this phone can do is to modify its IMEI at every SIM replacement, or after every call or SMS (actually only the scammer claim this, but these functions are not backed by any video whatsoever). Changing IMEI is pretty much what this phone can do. And nothing more. Compared with Siemens S65/SL75, XCell Stealth Phone has several criterias for IMEI change: it can change its IMEI with the one chosen by the user (user defined), or only at the first connection on the network (on reboot), and original IMEI can be restored anytime, which obviously is a major advantage. Of course, XCell Stealth Phone has more useful features, that makes it a true stealth phone: call interception alert, location tracking alerts, channel blocking function (ARFCN) to prevent eavesdropping by silently sliding to a GSM Interceptor, location spoofing function, displaying the TMSI value (a handy test to detect interception), phone calls audio recording and automatically delete calls list. It’s hard to argue with this facts, claiming that a Siemens phone is a better choice than an XCell Stealth Phone, which is having more special features, is more secure and is simply the best in branch. No doubt, the repair shop guy marketing strategy has failed. Our advice for this guy is to limit himself to phone unlocking and repairing (which he does it on a daily basis), and let's interception and phone security related issues on specialists account. And especially to stop selling fake stealth mobile phones. The legal issue It is illegal to use this change IMEI phone in UK and in most of the EU countries. Why? Because there is a law saying that you can not modify phones IMEI. And Siemens S65 is not preserving the genuine IMEI as XCell phone does. You cannot restore the original IMEI (as XCell Stealth Phones does), which will put you straight on the other side of the law. Just have a look what Staffordshire Police says about changing IMEI: this practice is illegal and only the manufacturers are allowed to alter it. We quote from what Police say: " 1(1) A person commits an offence if:
2(5) A thing is used by a person unlawfully for a purpose if in using it for that purpose he commits an offence under section 1." Please note that using XCell Dynamic IMEI Stealth Phones is perfectly legal since this phones does not change IMEI for good, this process being reversible by "Stay original" IMEI function. 6. What other products are being sold by scammers? In addition to stealth phones, these scammers sell so-called "encrypted" phones. What are these? Well, these are simple Android phones having installed various software applications (many of them are even free), and which have been encrypted by the seller by a simple and free operation. Encrypting an Android phone is a simple operation that anyone can do without having to pay anything extra. More information here. You can find plenty of free voice and SMS encryption applications by simply visiting Google Play Store. Some examples here. Why pay thousands of euro if you can do it for yourself, for free? Why buy a Blackberry encrypted smartphone (encrypted by other person) and paying a thousand euro, when you can simply use Blackberry Enterprise Service, directly from BlackBerry website? One more thing: an encrypted cell phone is not at all a stealth phone. Does not have any stealth features, as scammers are trying to convince you, by wrongly using terms as "encrypted stealth phone". We are going to post a separate thread about anonymous (pre-paid) SIM card scam. 7. No customer service, no technical support, no after sales support, no product guarantee, no user manual It's a kind of hit and run business. These scammers have no theoretical or practical knowledge about methods, ways and means of cellular interception, nor the principles of a GSM network. Most of them are simple repair shop guys, they only know about phone unlocking, firmware flashing, minor repairs, parts replacement, and that's pretty much all they know. Try to ask them about how the cellular interception work and how stealth phones that they sell, detects interception. You will be amused by the replies coming from them, if you will be lucky enough to get a reply. You may ask them about how location spoofing work (Channel lock function). Being a sensitive topic, XCell Technologies didn't make public this information which is available only for those who bought an XCell Stealth Phone. For this reason the customer service that scammers should deliver to the buyers, is nonexistent. Also, there is no user manual, nu support for any customer questions. Nothing else but lies or silence. Because of scammers lack of knowledge regarding cellular interception techniques, we have discovered a funny fact: both scammers ( Sohail Hussain - gsminterceptor.co.uk and Vittorio Ossola - antitap.com) has copied one from another the description of the product they sell, or (most likely) both of them has copied the text content from the original manufacturer's website, XCell Technologies. Have a look on pictures below. A new seller on eBay, a new stealth phone scam: this time, seller ID is allbuynew. Unlike other scammers that sell fake Samsung G600 stealth phones, this one pretends to sell the original version of XCell Stealth Phone. How he did that? Very simple: by copying XCell website pictures and text, on his eBay account. A hilarious thing: probably having no skills or basic knowledge regarding photo manipulation, nor money to hire a web designer, he has posted the photos with XCell watermark on them: On the picture below you can have fun about what this scammer has understood from explanations that he has read on x-cellular.com: The most funny thing is that the scammer has invented 10 "special features", selling this way not the "old" version but a new one, "updated Jan. 2014". In his personal understanding, UnPing function is an alert for "network triangulation", which is obviously wrong. No explanations about Channel lock, since XCell Technologies (the manufacturer of real stealth phones) has understood to disclose the use of this function only to users. The scammer has no source to copy these explanations, so he didn't posted them. He is right in just one of his affirmations: "the best and the only one" is the stealth phone that he try to copy: XCell Stealth Phone. Just to have more fun with this scammer, you should ask him for a pic, taken from the phone backside: there is no XCell security label. Also, you should ask him before buying, about how Channel lock function work, UnPing function and how to properly use IMEI changing function. And yes, his explanations about how to use the phone and how call interception work, will be memorable. Have fun! Visiting his eBay store, we have found that the scammer (allbuynew) is selling also another well known scam: That being said, we think that the photo above and the products he sell are self explanatory regarding the trust you shouldn't have. Or you should ask for buy one, get one free: buy one fake stealth phone, get one penis extender, for free. Update 1.07.2015: We have identified another two scammers on eBay, selling counterfeit Samsung G600 stealth phones and fake Samsung G600 stealth firmware (the one that you can download for free, here). danielius2010 Located in Lithuania, selling fake Samsung G600 stealth firmware on eBay: swetroop Located in London UK, selling counterfeit Samsung G600 stealth phones:
|
AuthorStealth-phones-guide.com Archives
April 2022
Categories
All
|




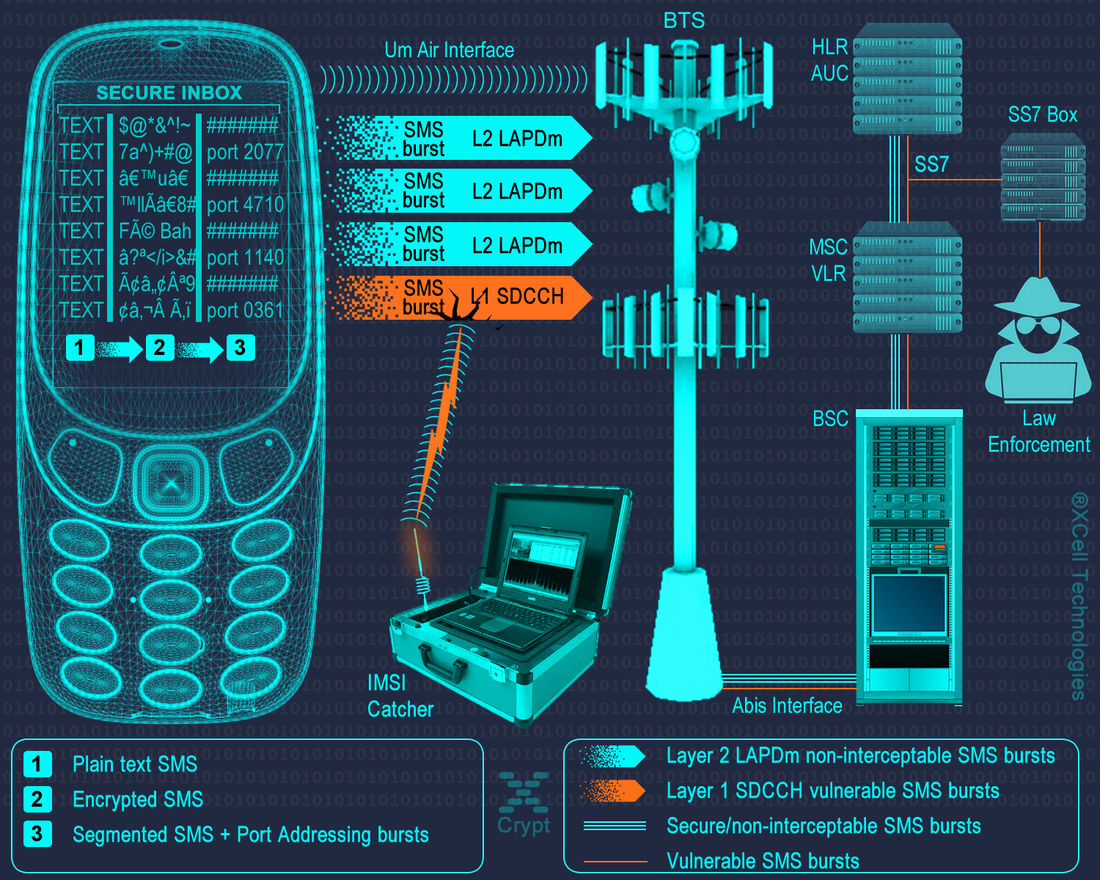

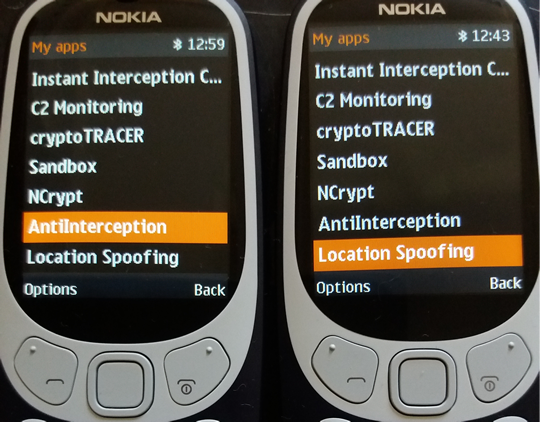
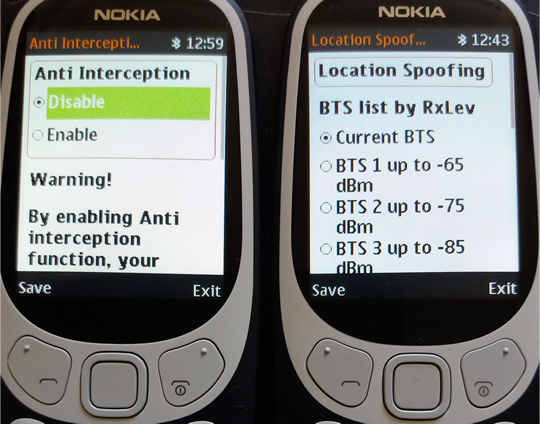
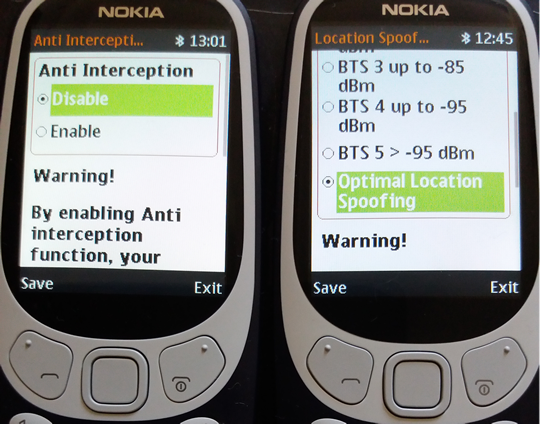

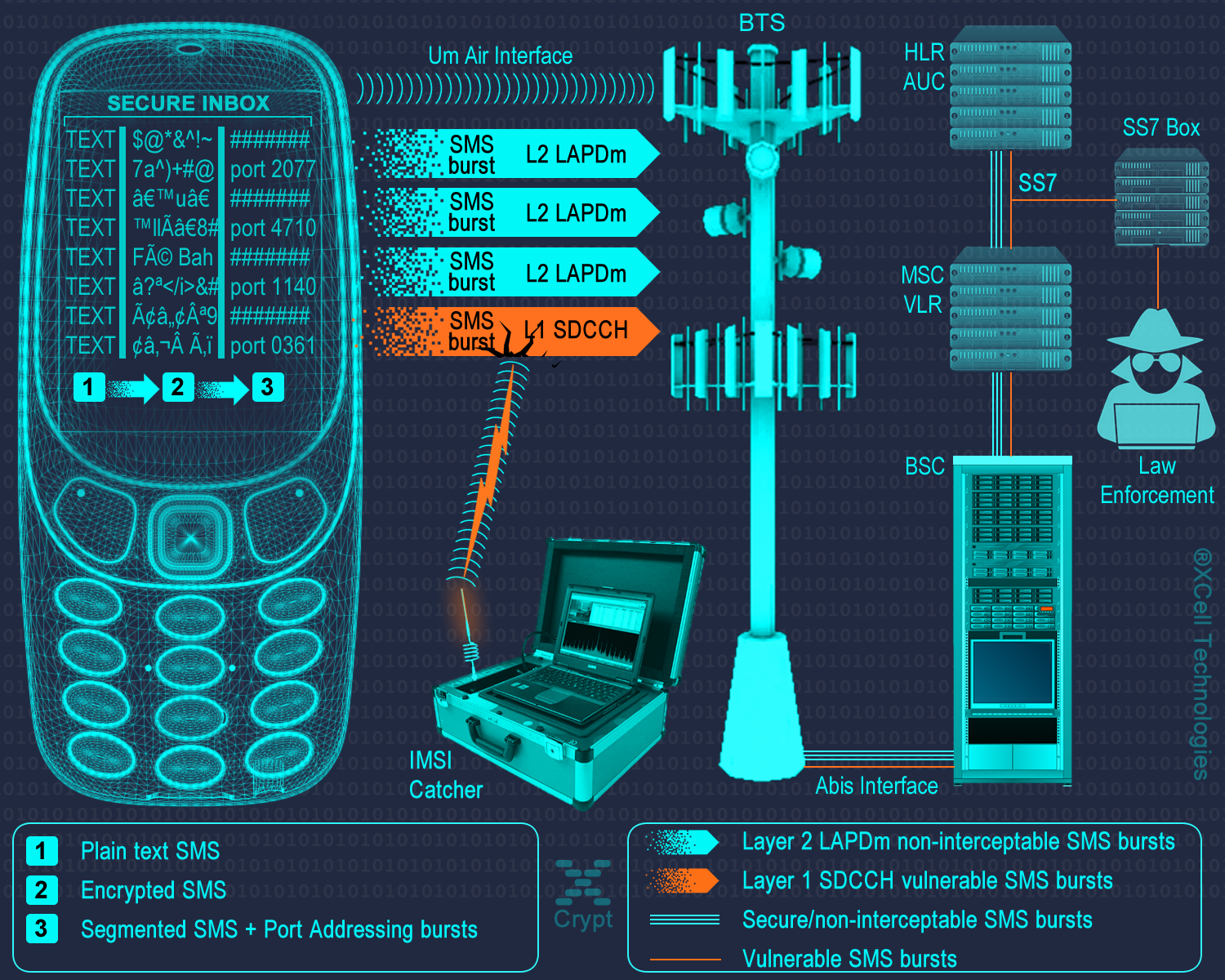


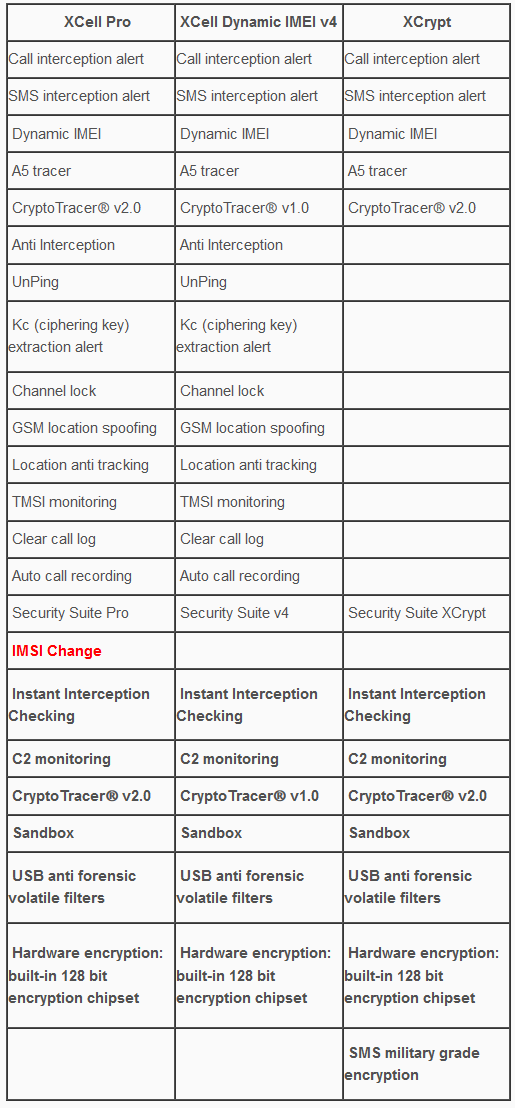

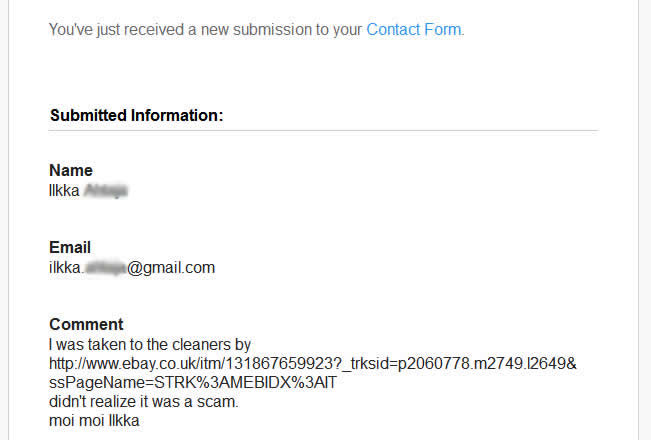
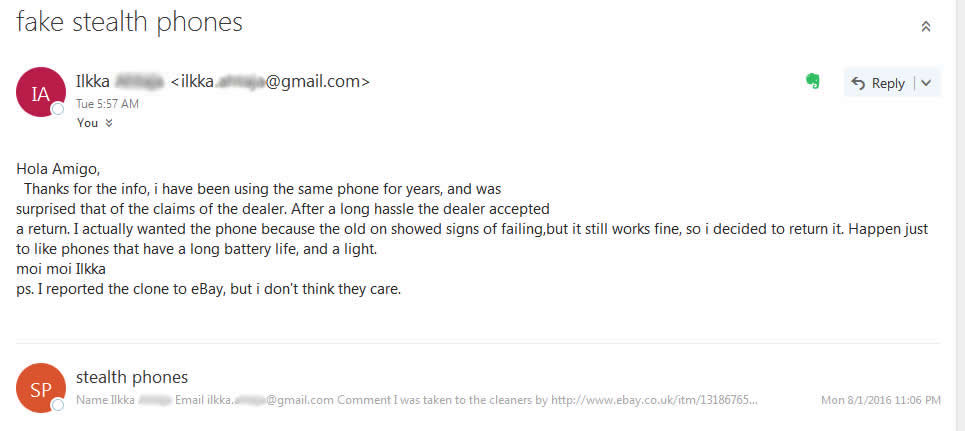



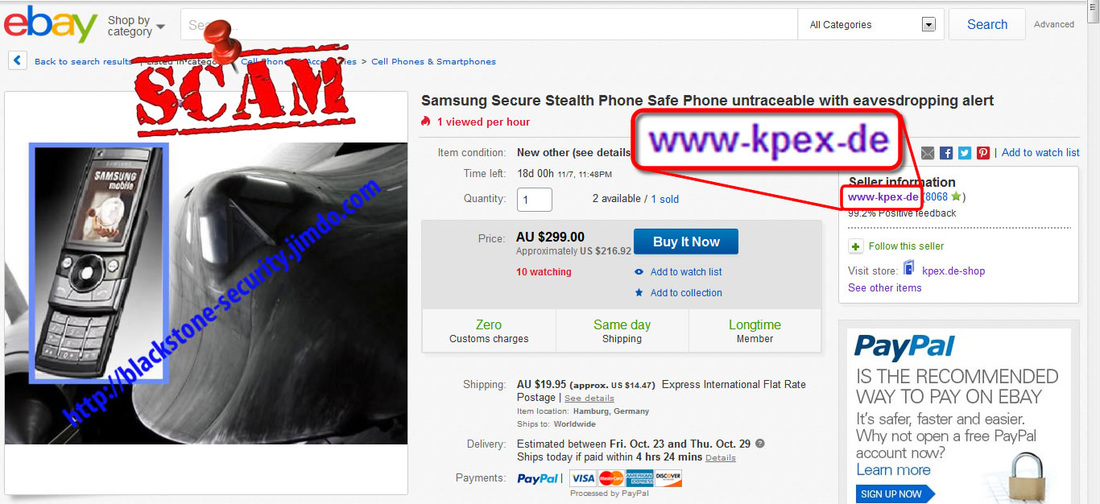
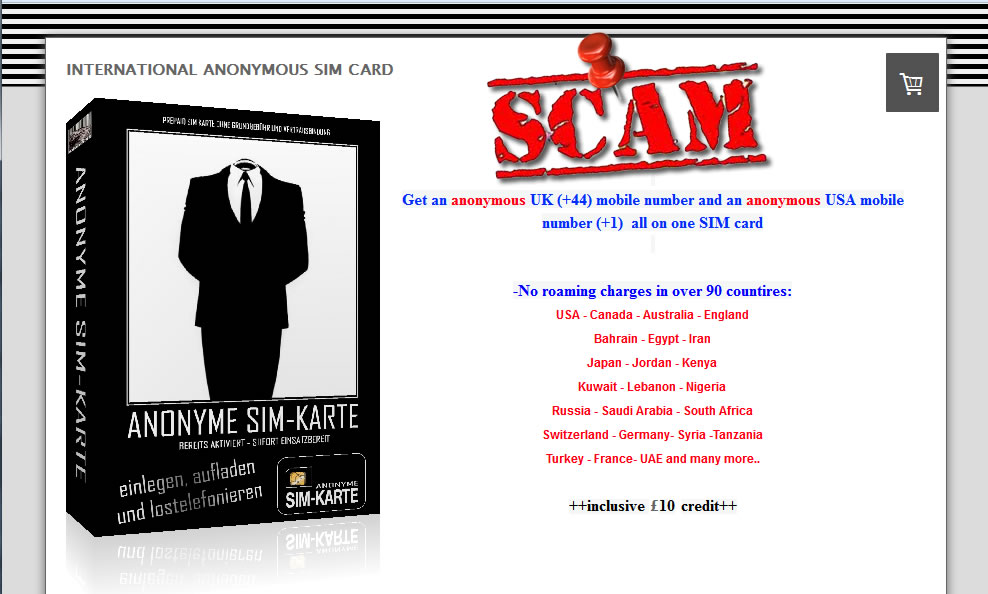
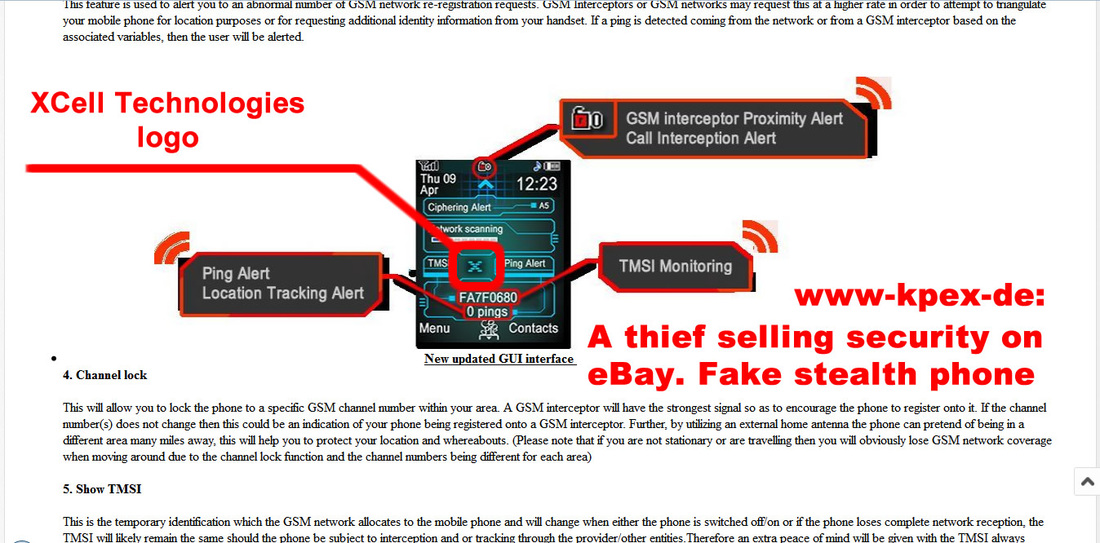
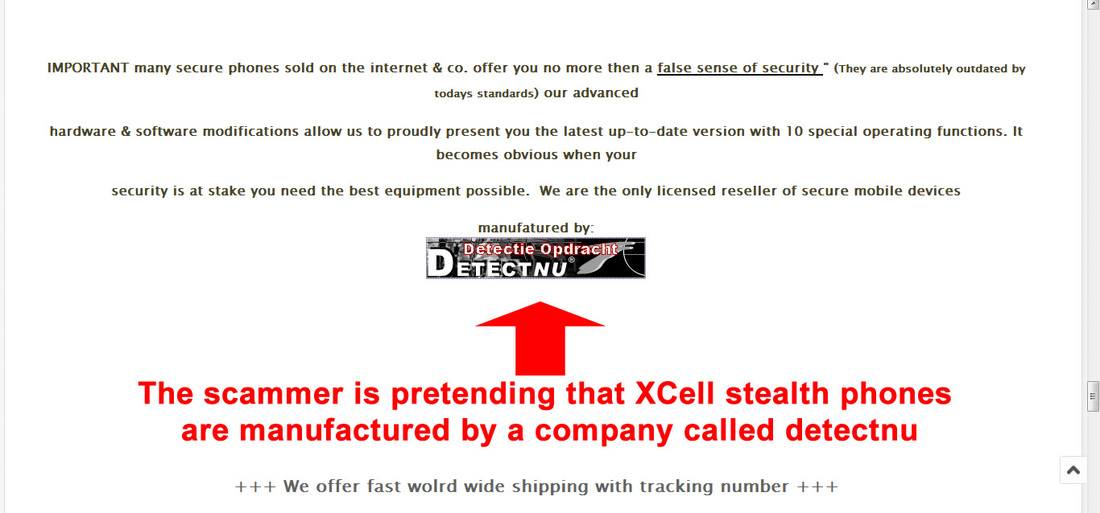
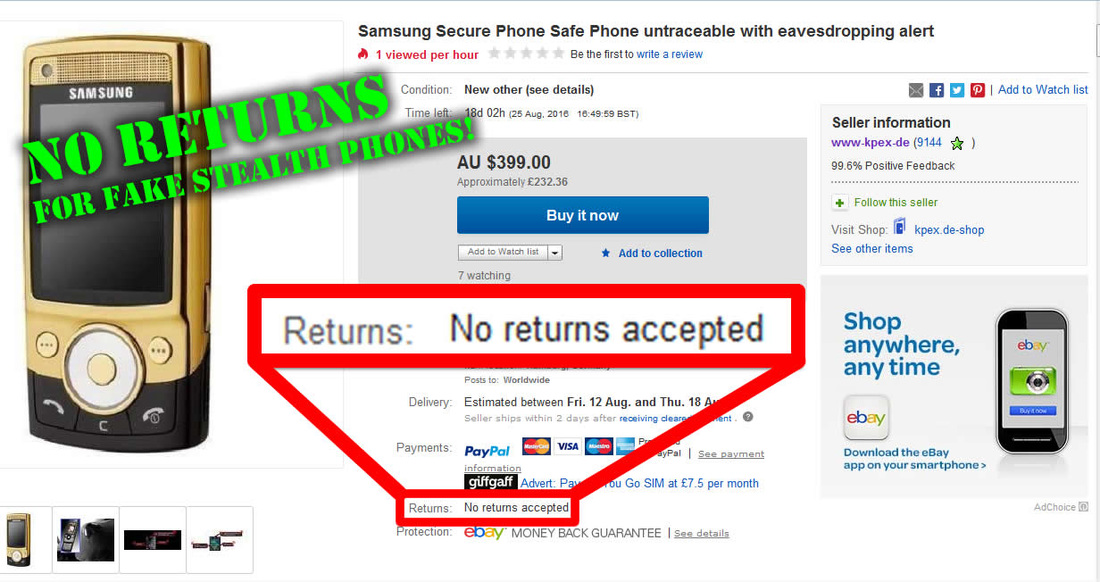
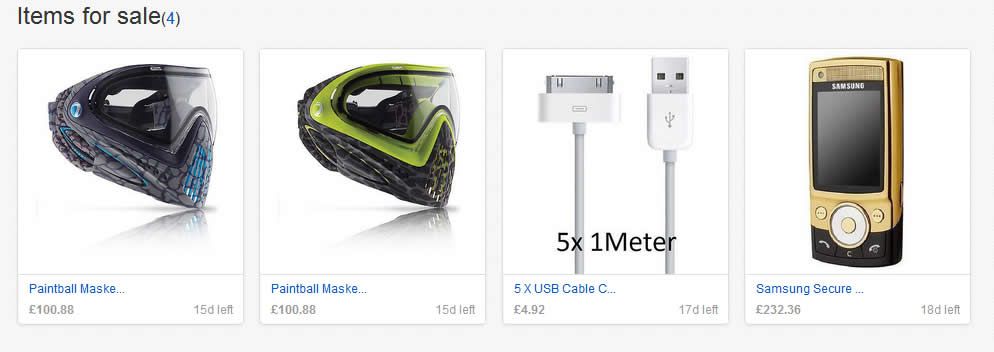

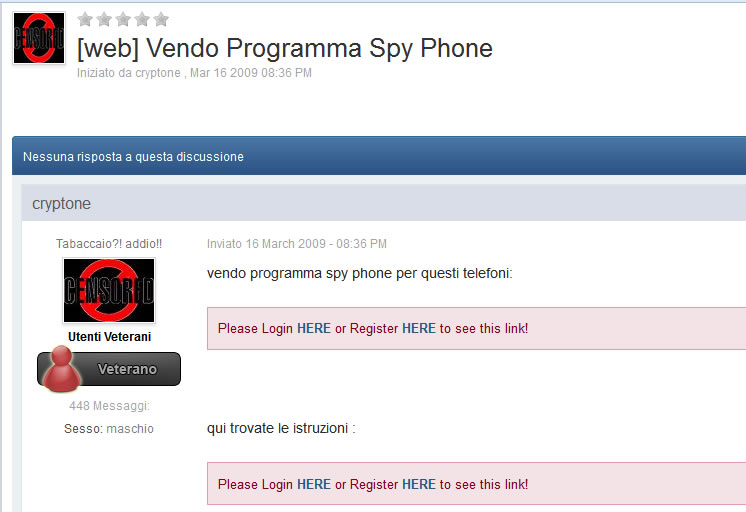
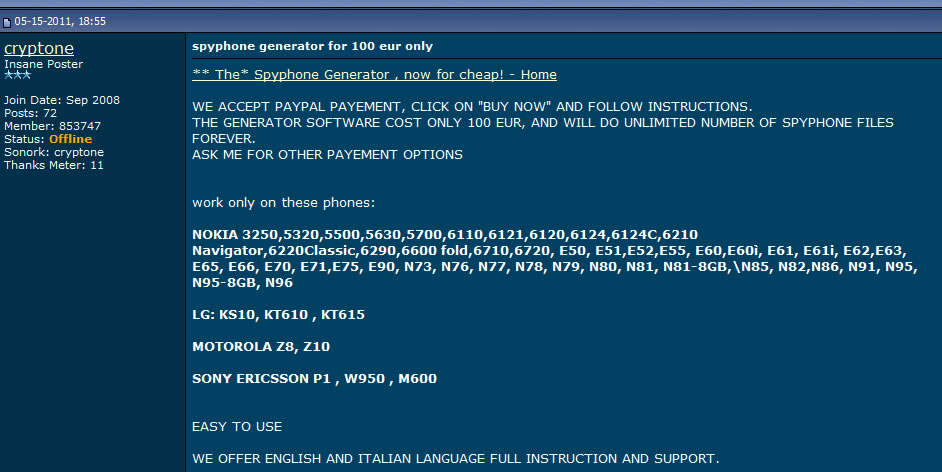
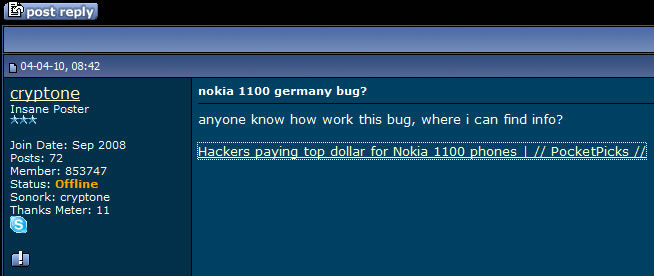
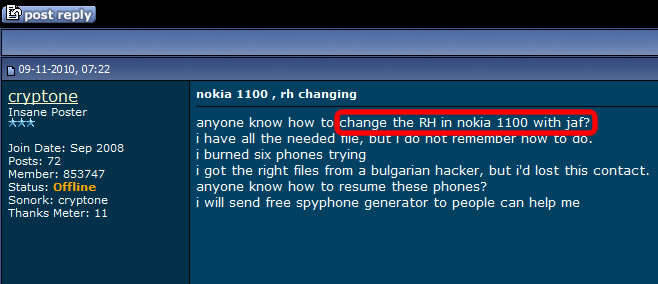
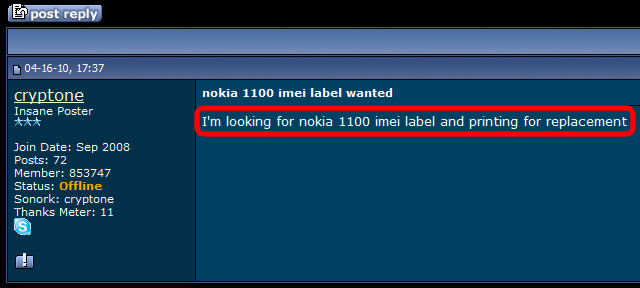
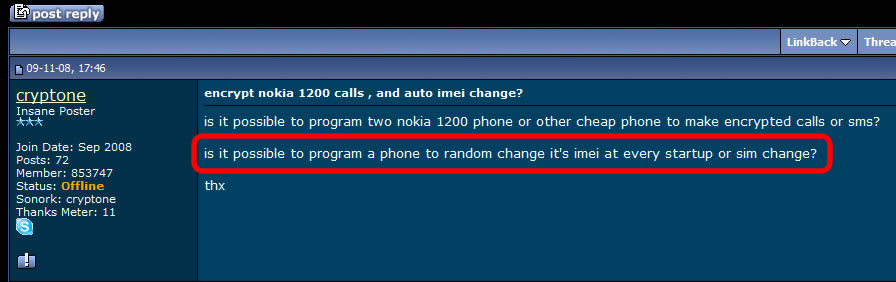
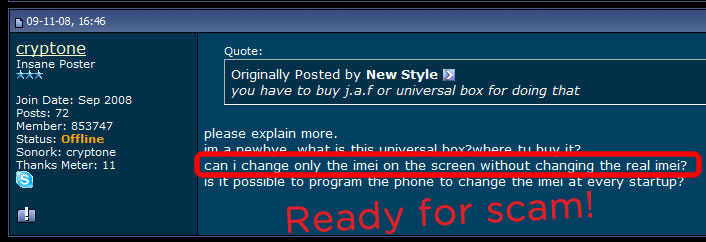
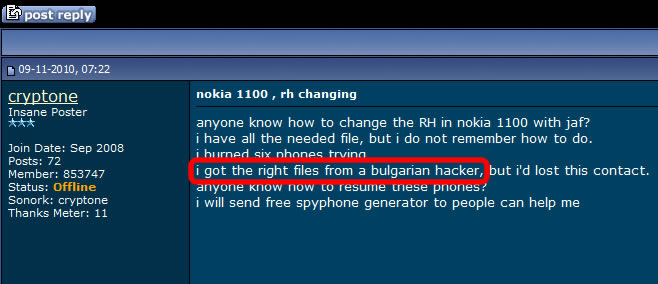
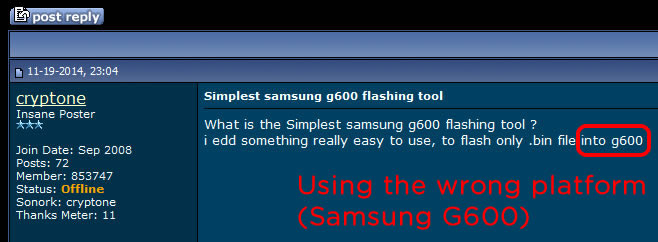


















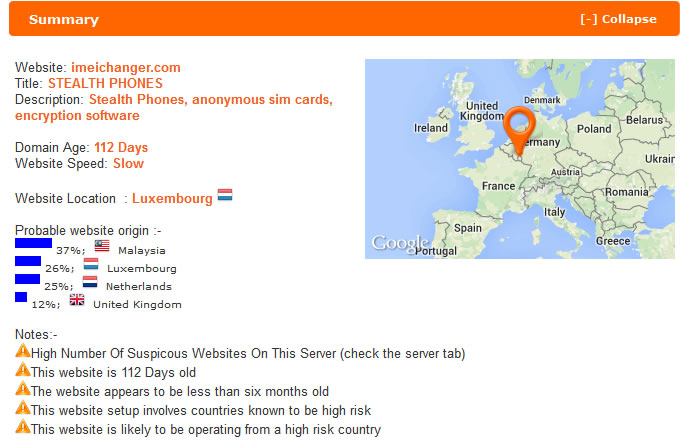


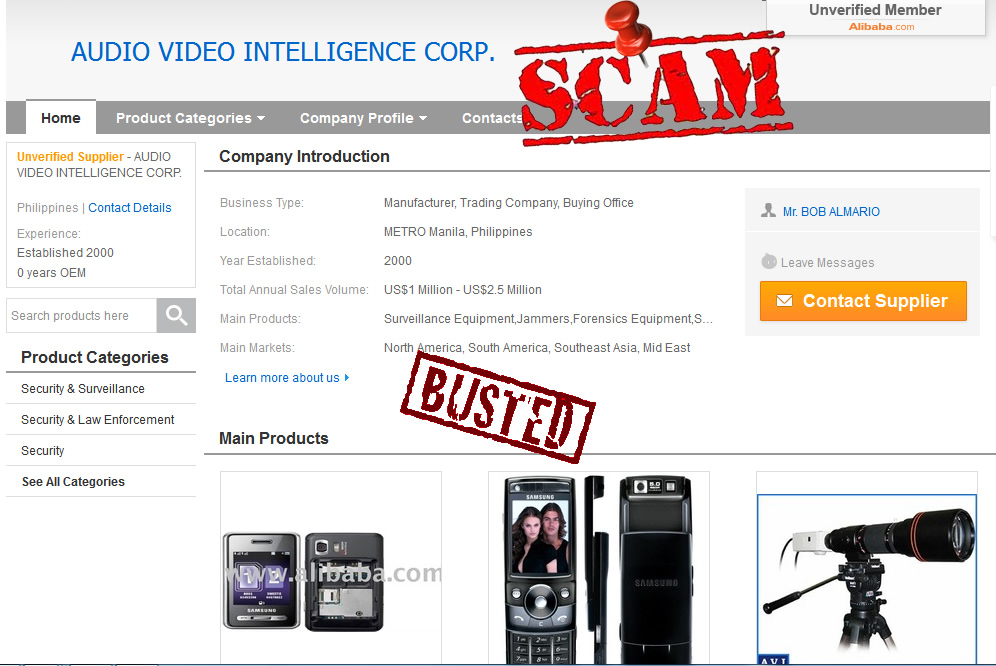

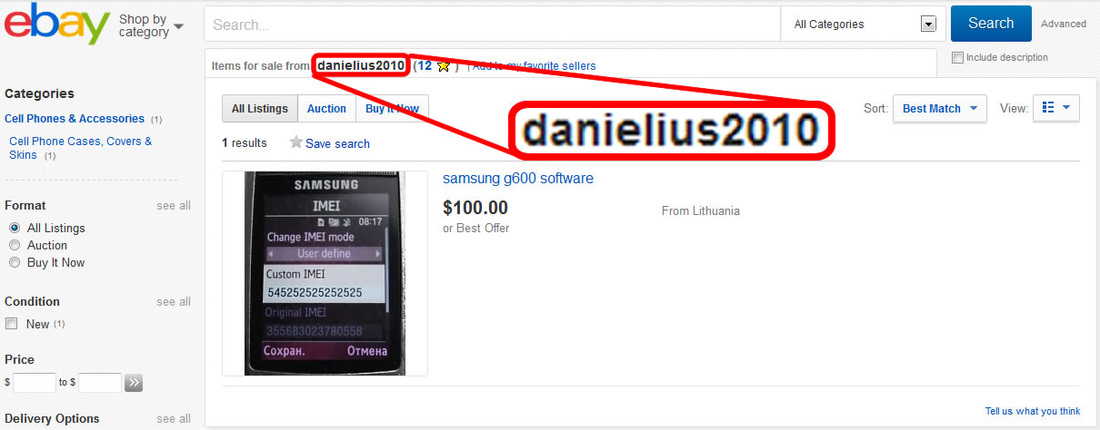

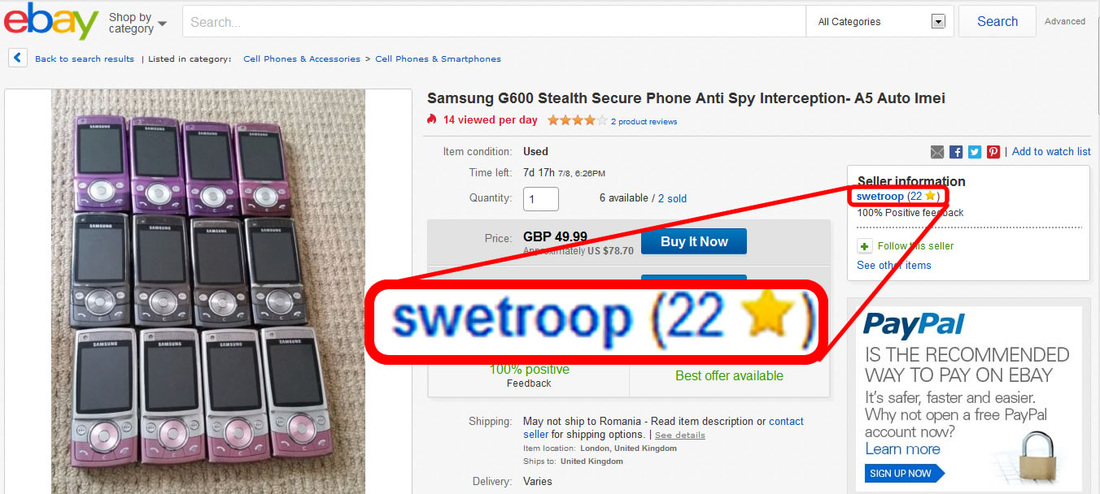

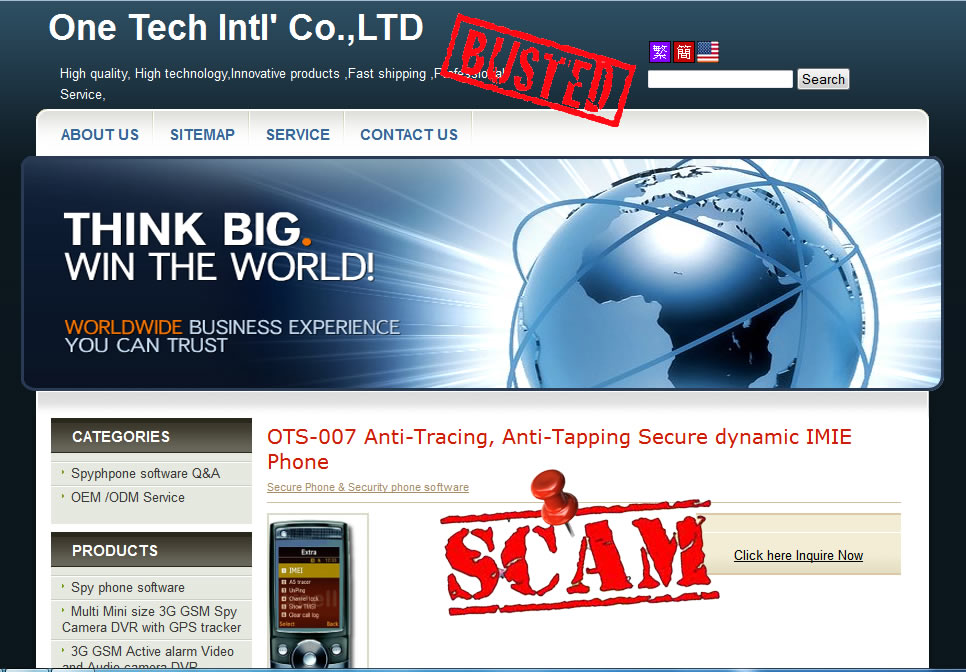
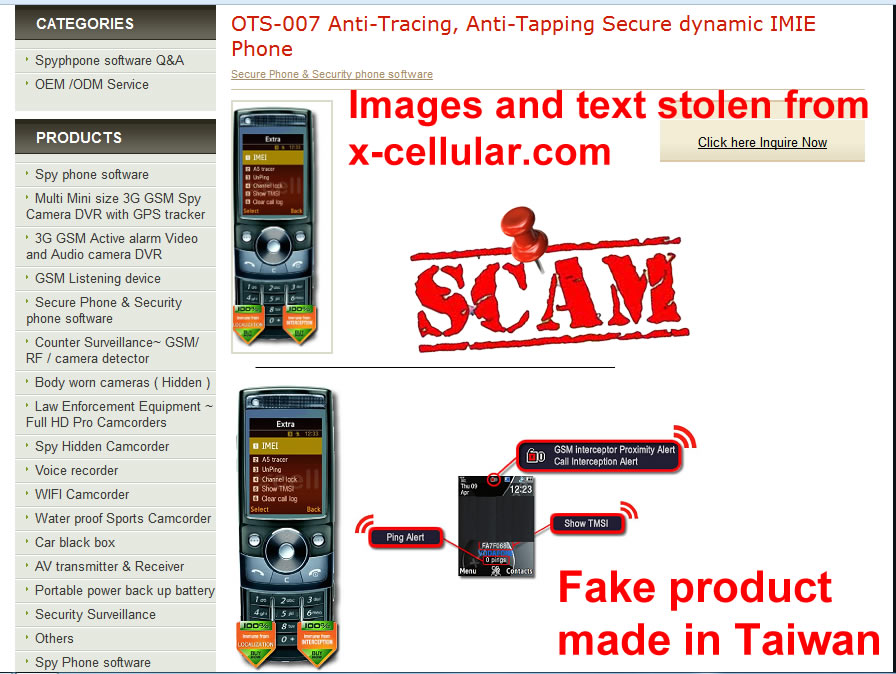



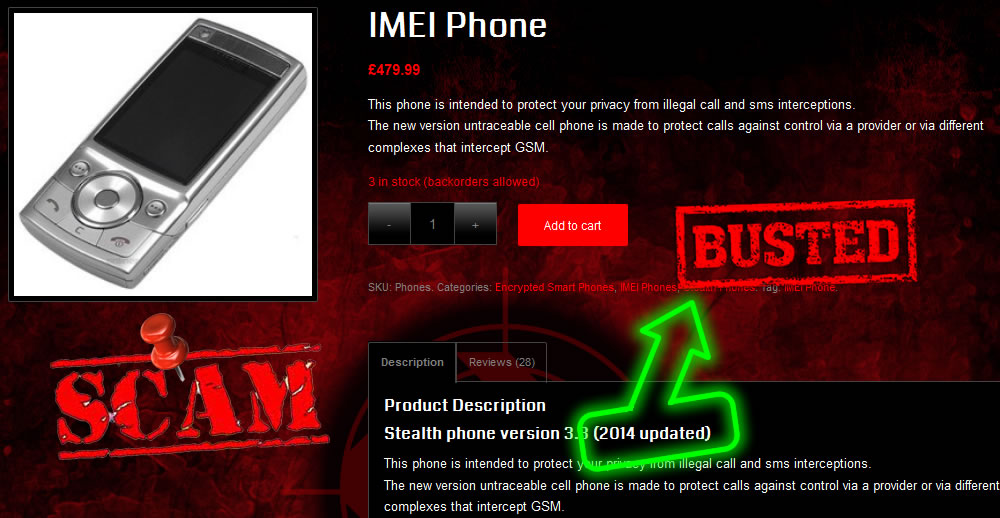
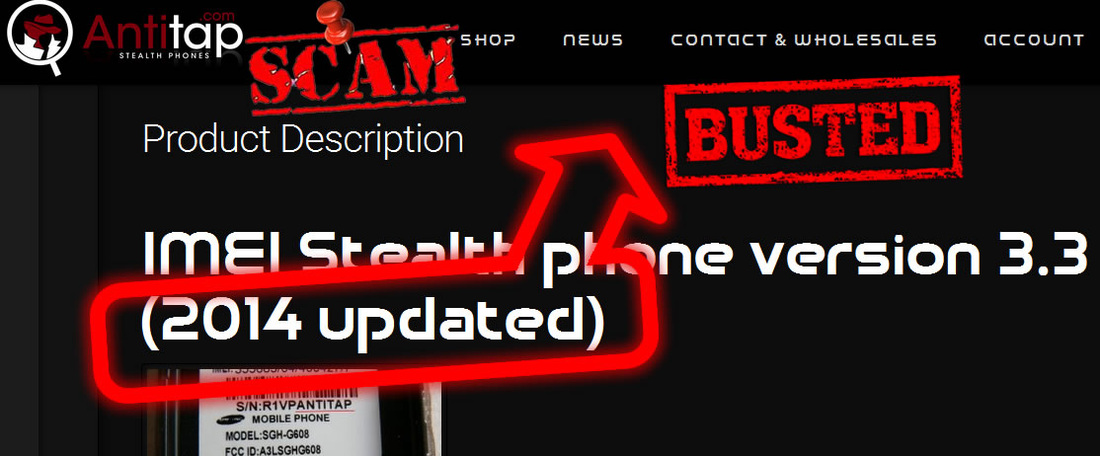
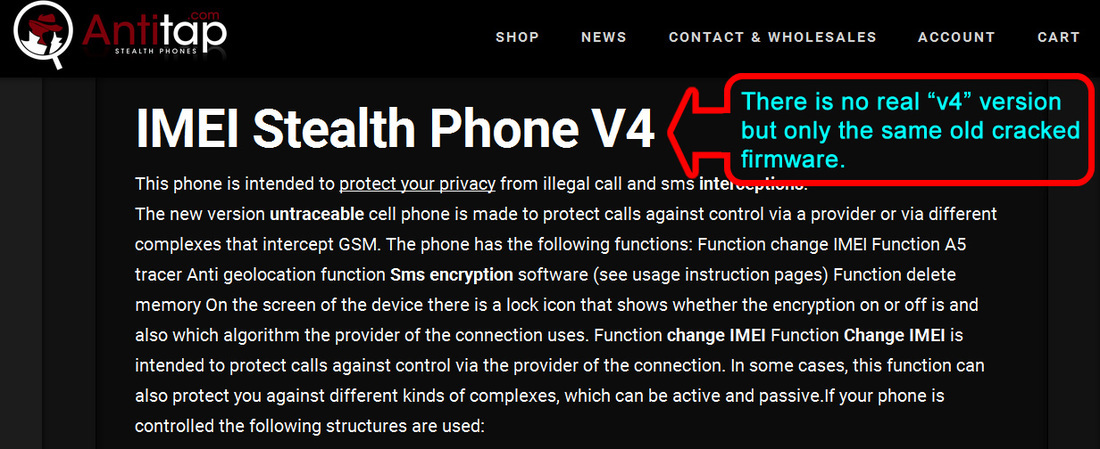
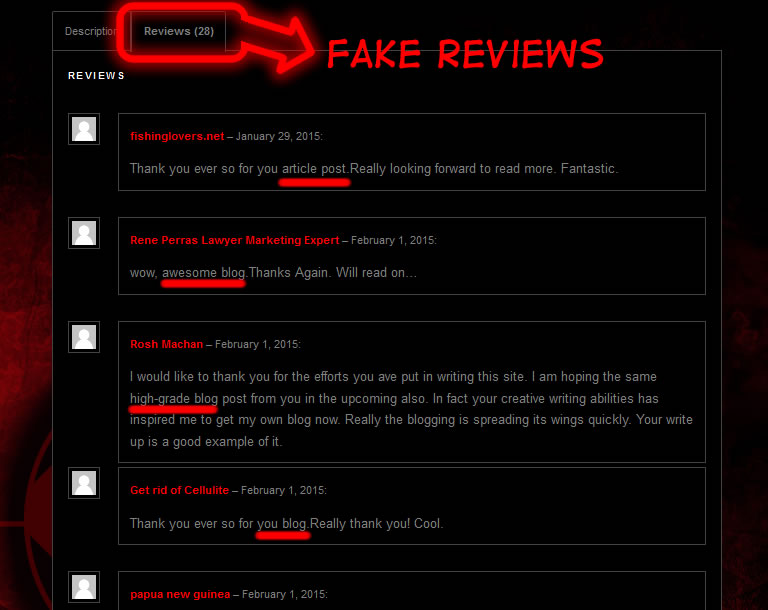
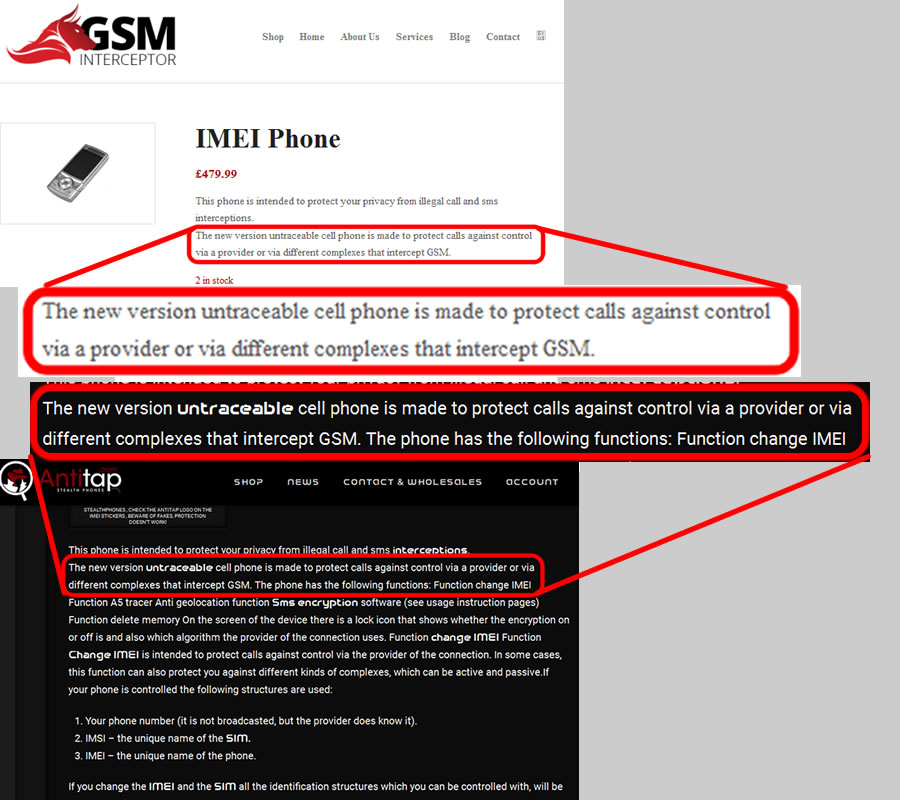

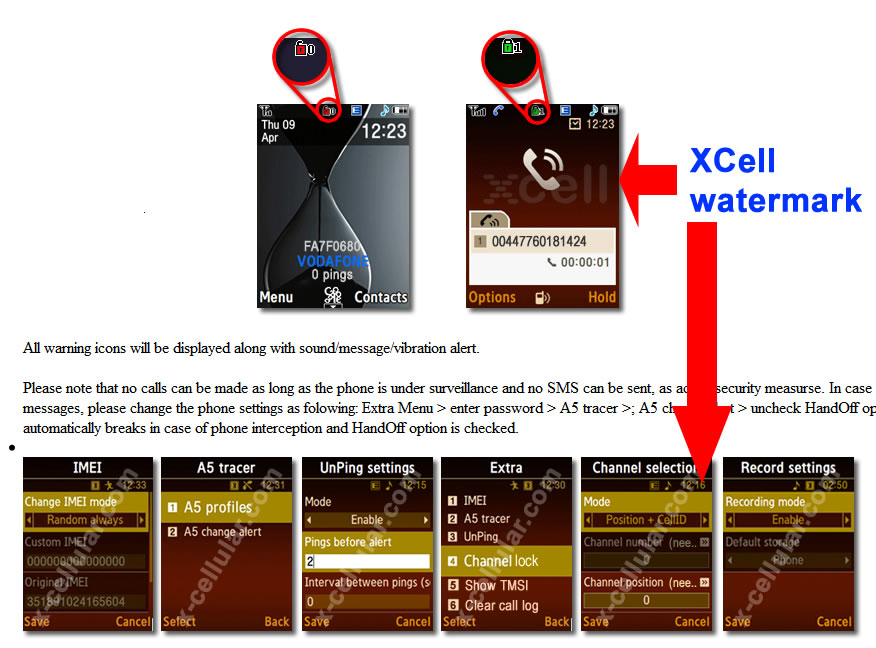
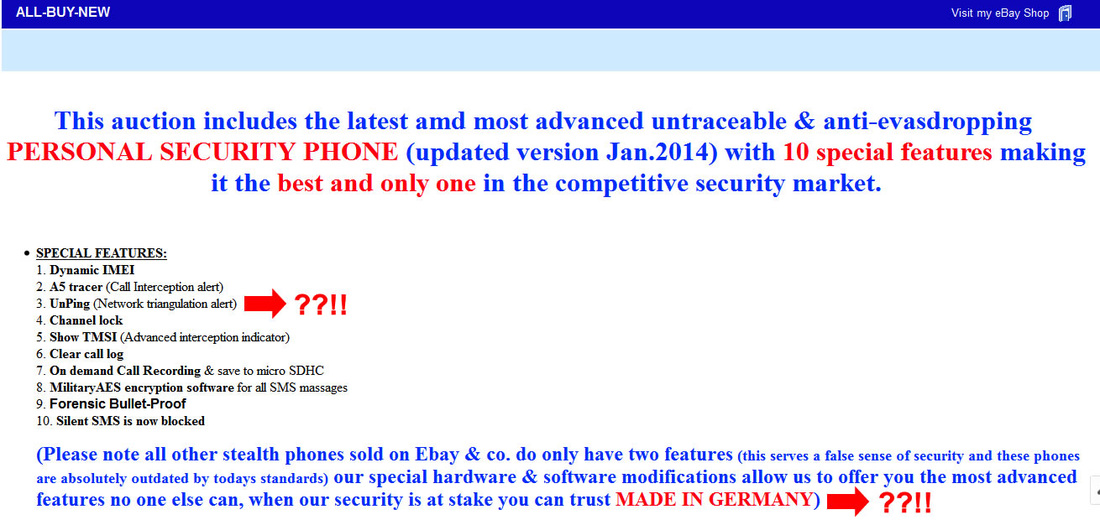
 RSS Feed
RSS Feed