Please note that we do not sell any devices, this is not a web store. We are not related to XCell Technologies, nor a subsidiary. If you want to buy any Stealth Phones, please contact manufacturer.
XCell Technologies has launched on 1st January 2019 their new flagship product: XStealth, an epic Android based Stealth Phone. Announced as a game changer, XStealth is one of a kind Stealth Phone. No other "secure" mobile phones have the same special functions and capabilities as XStealth have. Now, you can stop hiding. Be invisible and fight back with XStealth Phone.
Mobile technology has never played a more important role in personal security and basic rights than it does right now. XCell Technologies is uniquely poised to address the dangers of mobile interception used illegally or abusively by state towards its citizens, following shortsighted policies.
The next big thing is here. There was no perfect Stealth Phone, until now. The upcoming generation of Super Stealth Phones has been successfully rolled out.
Based on XStealth military version released back in 2014 and stuffed with new and unprecedentely special functions, XStealth is now available for public use.
What do you want from a Super Stealth Phone? Everything, probably. After all, it's about your security. Well, with new rolled out XStealth Phone, you've got everything. And the best is yet to come.
Android Super Stealth Phone comes now in two flavors. Since XStealth Lite has been built for personal use, XStealth devices are aiming professionals ranging from govt to law enforcement and homeland security agencies. XStealth Pro is also coming as top notch product.
Get the most out of your Super Stealth Phone, with our breakdown of specs:
First, about XStealth hardware security.
There is a kill switch to self-destruct on command even if the phone is turned off. As no other secure phones, XStealth USB port is protected by our well known volatile security filters: any attempt to connect the device to any other external device (no matter if PC, service box or forensic grade equipment), other than its own paired charger, will trigger a self-nuke mechanism that literally fry the whole motherboard in the same way as USB Kill work.
Anti-tamper JTAG protection is also implemented: serial communications interface for low-overhead access without requiring direct external access to the system address and data buses are disabled by default at serial interface level.
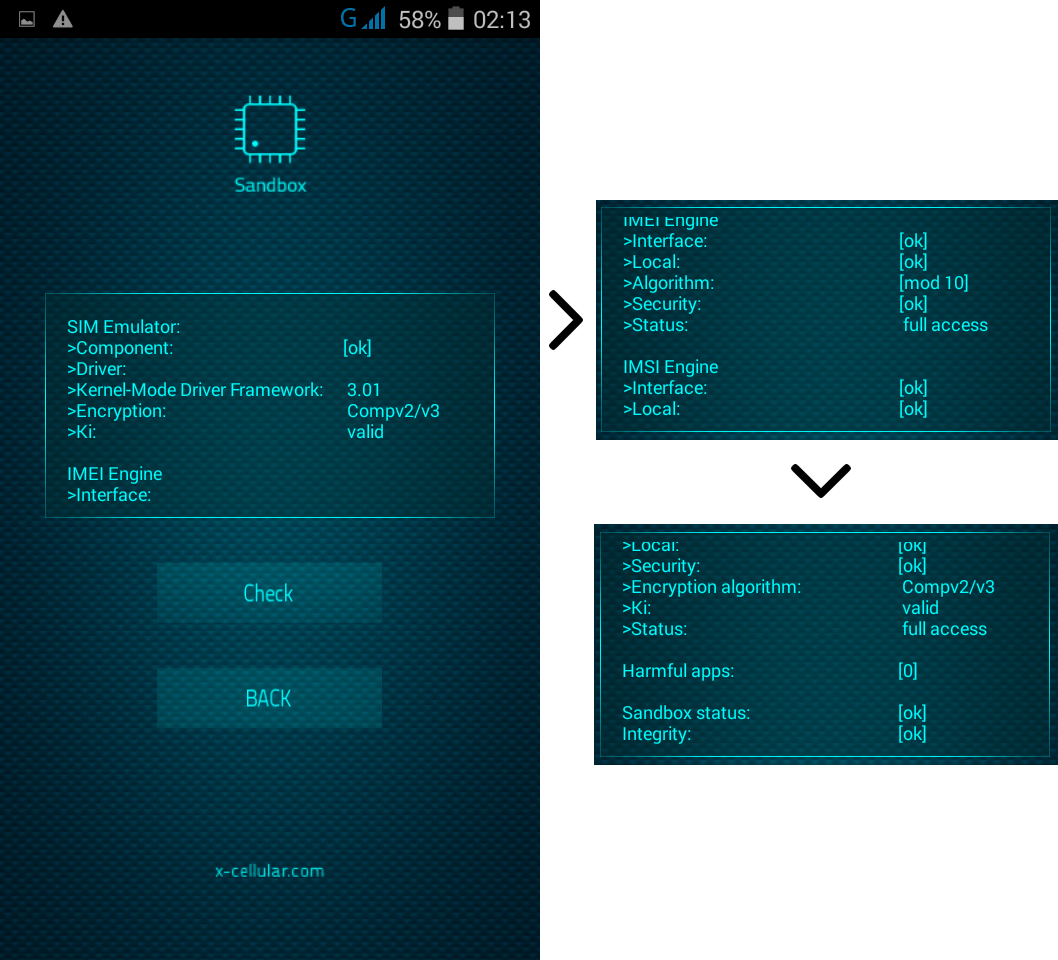
XStealth Phones use a Tamper-Resistant Platform: any unauthorized attempts to connect the phone to any external device will delete the keys that encrypt all sensitive data. A remote wipe function is also available.
Authentication to login to the phone uses multi-factor (MFA) technology, voice biometrics being one of them. Due to security risks involved by face and fingerprint recognition login, these options has been removed.
Trusted Execution Environment (TEE) uses encrypted memory and includes a hardware random number generator. Communication between the Secure Environment and the application processor is isolated to an interrupt-driven mailbox and shared memory data buffers.
There is also installed a Data Execution Prevention (DEP) technology to mitigate memory-based attacks. This defensive technology dramatically narrows the attack surface area for memory related exploits by preventing code from being executable in sections of memory that have specifically allocated for read only data. DEP support is a critically important defense when used in conjunction with Address Space Layout Randomization (ASLR). These core improvements make it more difficult for spyware to perform buffer overflow, heap spraying, and other low-level attacks. Therefore, even if an attacker succeeds in loading the spyware code into memory, the spyware code will not execute.
XStealth Phones are not susceptible to side channel attacks, including various forms of power analysis attacks to ensure the protection of cryptographic keys.
XStealth Phones has the ability to execute a secure boot based on using a hardware root of trust for checking and storing hashes or signatures of firmware and other software loaded starting with the initial BIOS.
XStealth Phones have separates CPU from Cellular Baseband, preventing this way external manipulation by baseband attacks.
Now about XStealth software security.
Today too many apps are engineered to collect and disseminate enormous amounts of user data—such as location, Web browsing histories, device-unique IDs, search terms, and contact lists – data they often simply don’t need. Some app providers also try to obfuscate their data collection functions to get around restrictions by marketplaces such as Apple’s that are intended to prevent abuse of APIs and ensure better privacy for users. For example, researchers have recently discovered hundreds of apps in the App Store that extract personally identifiable user information via private APIs that Apple has forbidden them from calling. The abuser that was singled out – a Chinese mobile advertising developer called Youmi – used simple obfuscation techniques and dynamic linking to get around the application vetting checks performed by Apple. Same for Android platform, on weaker Google Play Store.
XStealth Phones runs a special version of the Android operating system—XROM—that blocks many of the ways phones leak data about your activities. XROM is an Android fork developed by XCell Technologies; it uses Google’s code for the underlying platform, but skips Google Services in the same way Amazon’s FireOS does.
The connection between XROM and software applications is filtered by Secure X-OS bridge, keeping both firmware and software applications away from exploits. Obfuscated code is adding an extra protection layer.
XStealth Phones does have Android trackers disabled by default, leaving no traces on Internet.
XStealth Phones comes with preinstalled generic applications which we have modified certain features (like removing back doors used by law enforcement and some security flaws), adding a plus of security and privacy (especially for Yahoo and Hotmail clients). This is why we have blocked any OTA software update which can restore security issues. Software updates usually refer to compatibility with new Android versions, which is not our case and will not impact application workflow.
Regarding anti-virus application and software updates:
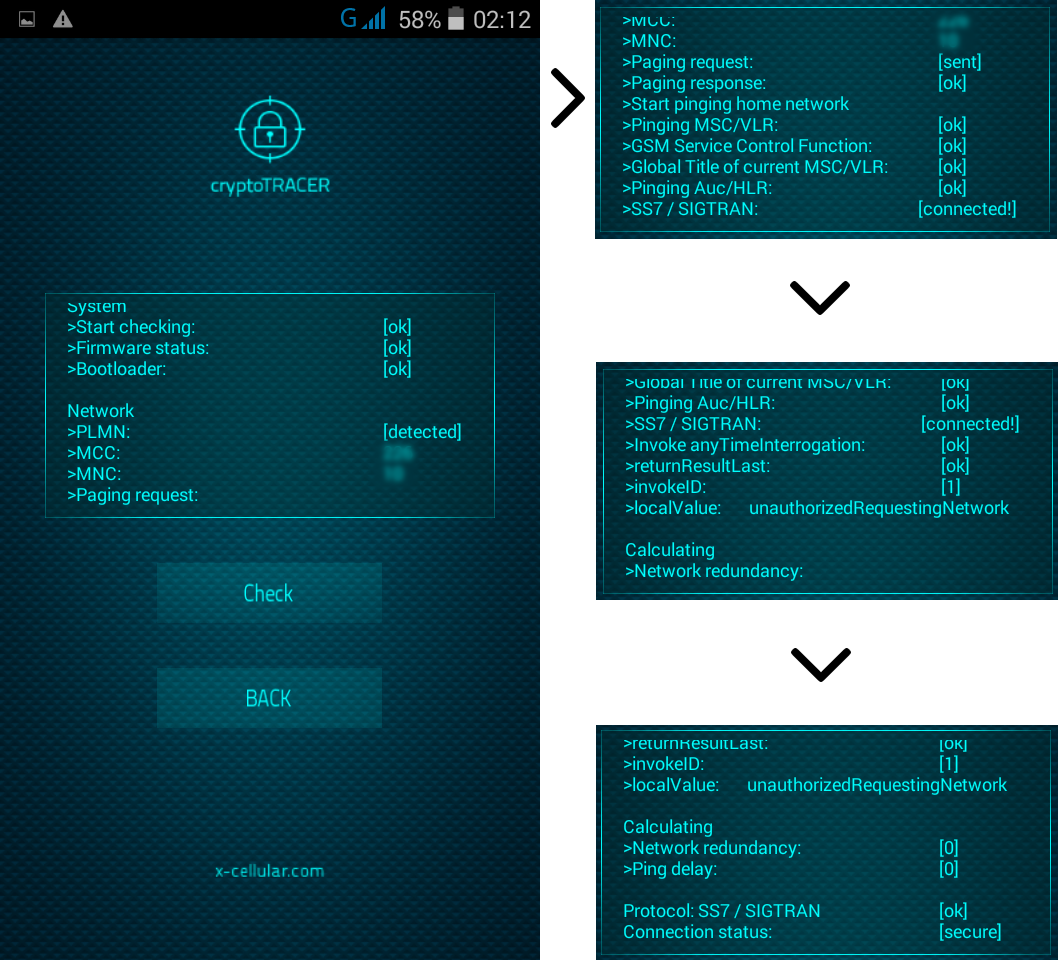
XROM firmware is secure by default: no other software applications can be installed by the phone user (which have the phone on its hands) nor remotely, by obscure third parties or abusive law enforcement. Hence, no anti-virus software is needed. Also, XStealth Phone will not perform any OTA firmware/software update, which may lead to remote exploits. You have to understand our point of view and hopefully reconsider your approach when it comes to mobile security: XStealth Phones are not aiming average users. All our Stealth Phones has been developed for professional use: intelligence agencies, law enforcement and homeland security. All above entities does not relay on encryption when it comes to secure communications because of a simple fact: all mentioned agencies have legal access and gain information they need by using back doors provided right by the software developers. If there is no cooperation from developer, then they will use another effective methods to gain access to relevant info, other than the ones used by hackers. There are plenty of companies that provide a wide variety of methods to penetrate any system such as computers and mobile phones. FinFisher is one of them: "Our Deployment Methods & Exploitation Solutions cover the latest PCs, smartphones, tablets and most common operating systems." "FinFisher can be covertly installed on targets' phones by exploiting security lapses in the update procedures of non-suspect software." "The software suite, which the company calls "Remote Monitoring and Deployment Solutions", has the ability to take control of target phones and to capture even encrypted data and communications. Using "enhanced remote deployment methods" it can install software on target phones." FinFisher malware is installed in various ways, including fake software updates and security flaws in popular software. Sometimes the surveillance suite is installed after the target accepts installation of a fake update to commonly used software. The software, which is designed to evade detection by antivirus software, has versions which work on mobile phones of all major brands.
FinSpy is a field-proven Remote Monitoring Solution that enables Governments to face the current challenges of monitoring Mobile and Security-Aware Targets that regularly change location, use encrypted and anonymous communication channels and reside in foreign countries. FinSpy is bypassing 40 regularly tested Antivirus Systems. Hence, no point to install an anti-virus as you have mentioned. XCell Technologies have opted for another effective solution to circumvent malware and harmful software install.
Please see also this short movie regarding remote mobile surveillance by "updating" a BlackBerry cell phone application: https://www.youtube.com/watch?v=n5ZJUXweayo
Even worst, also a not so skilled hacker can easily remotely install a spy application on a mobile phone which will not be detected by any antivirus, by the same "software update" procedure: https://www.youtube.com/watch?v=LicdrZwmHQo
There is a FinSpy detection algorithm installed deep on XROM firmware that will not only detect any intrusion attempt, but will block any code execution.
Encrypted bootloaders comes as standard option.
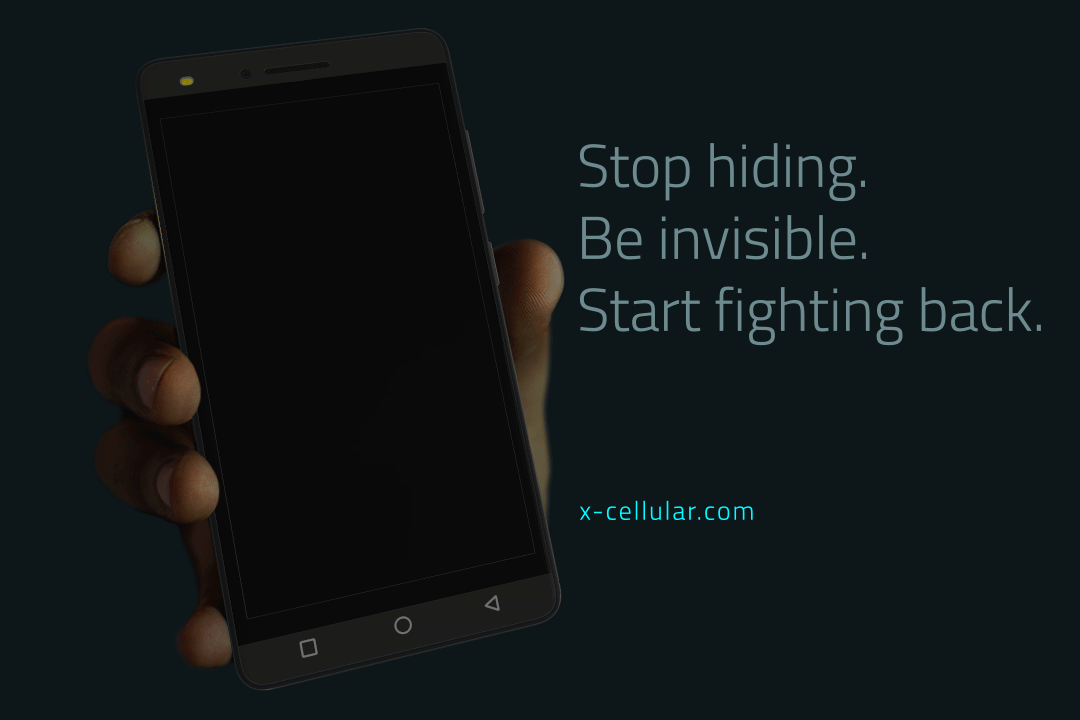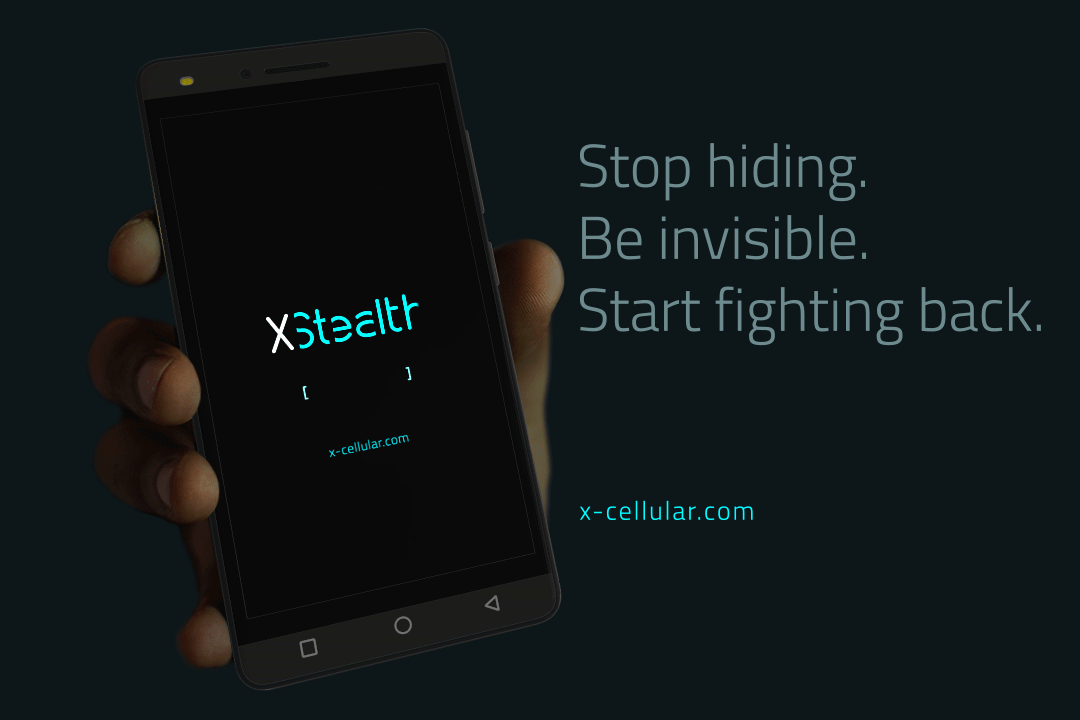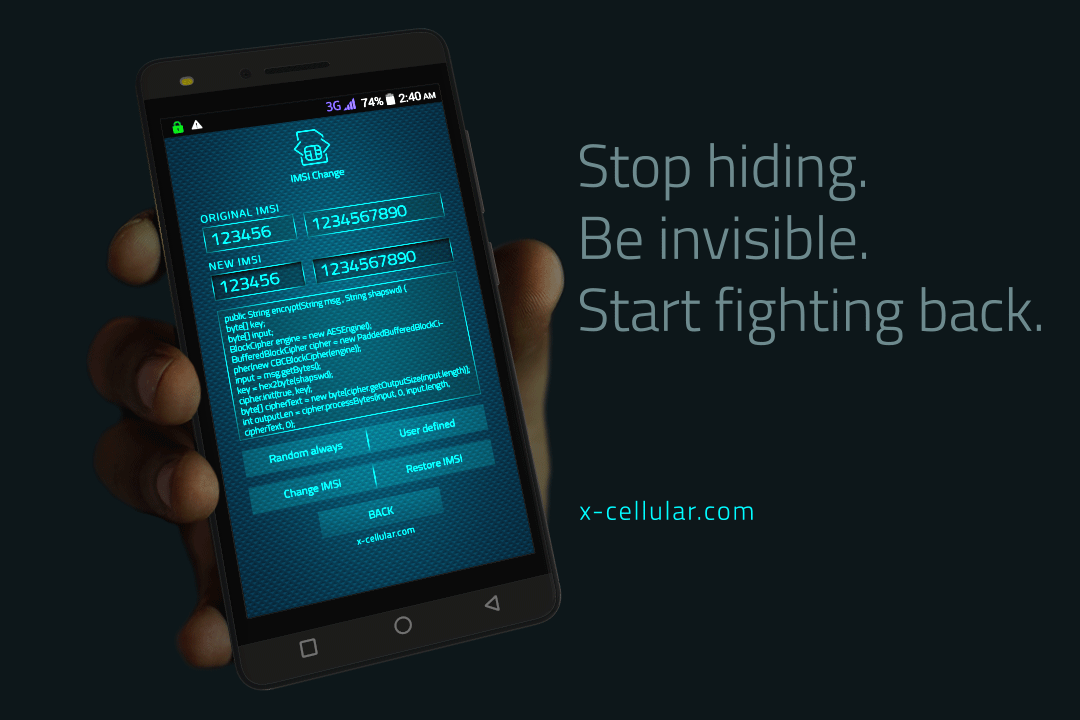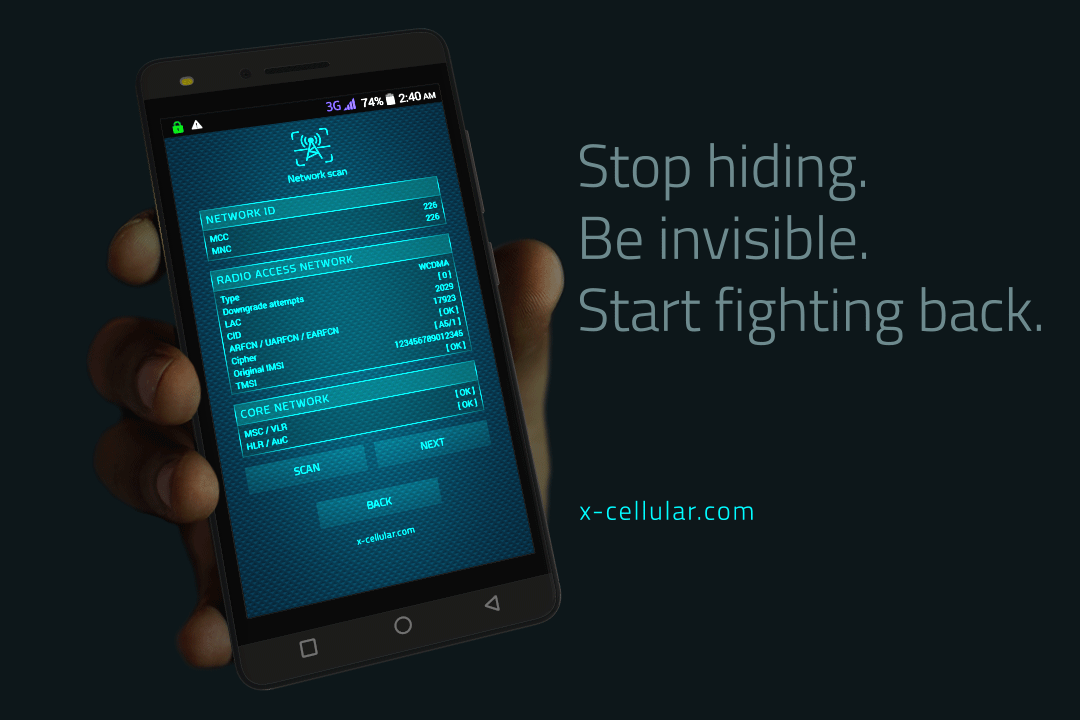
XStealth Phones are also using SIM Toolkit inhibitor, a blocker for remote code execution via SIM Toolkit (used usually by both network operator and law enforcement).
XStealth Phones use adaptive security defenses, being ultra-secure and adaptive [personal] smartphones: we will install before shipping any software application desired by the buyer, but only after running a comprehensive security audit. We will refuse to pre-install applications that can affect user privacy and security, and phone functions. No file explorers will be installed, as well as forensic clients or modded applications.
There are also things that we will not make them public available, as encryption algorithms used and firmware source code, simply because for any cryptanalyst will be more easy to break encryption when used encryption algorithms are known.
Also, a user controlled source code is not an option for XStealth Phones: that might be a huge opportunity for hackers and state controlled entities to find exploits, remote install/RAT or spyware which in the end of the day will lead to no security.
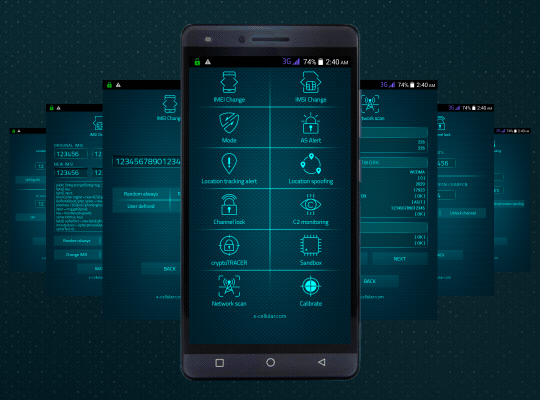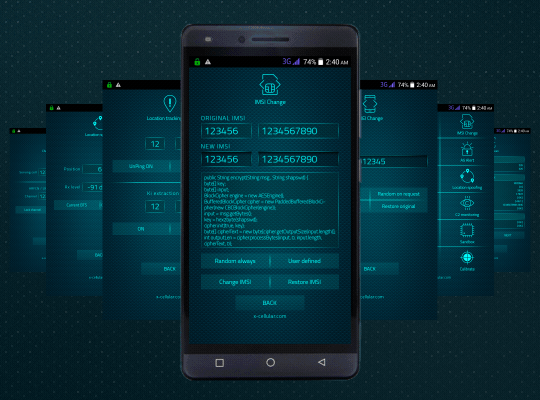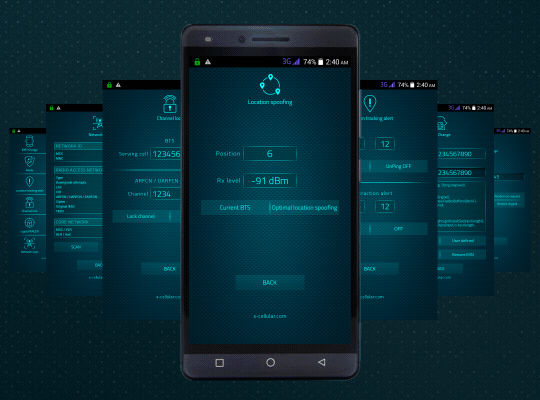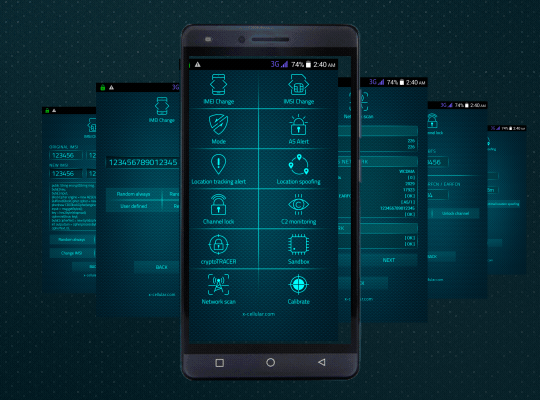
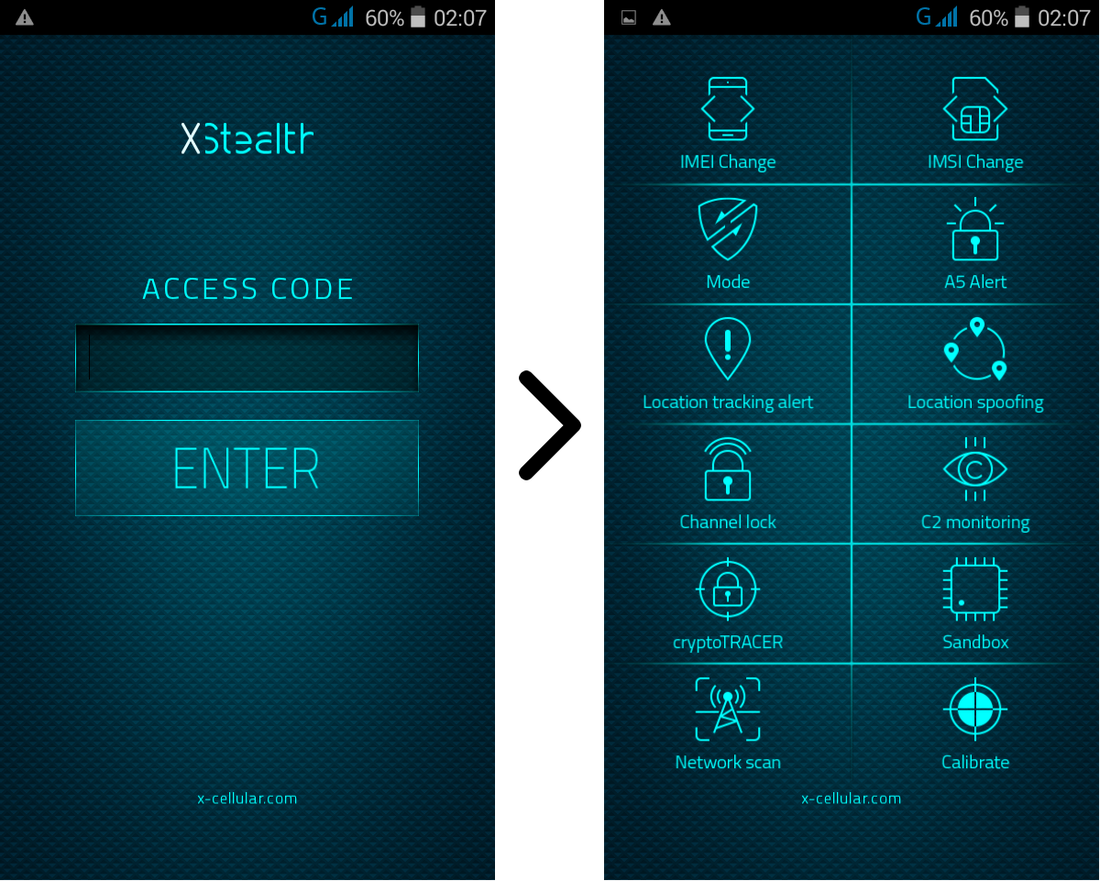
Please see below a list of special functions and default software applications.
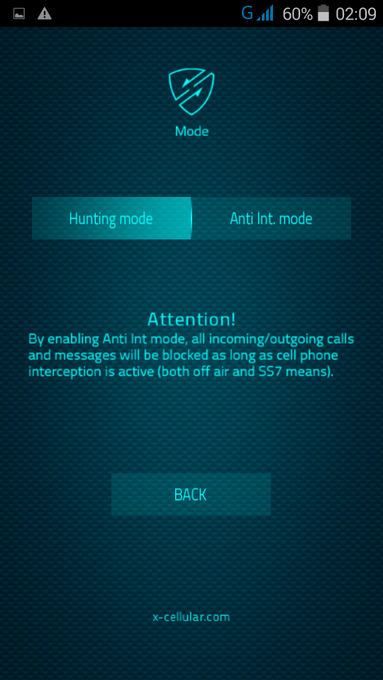
Special functions command panel is password protected, accessible only by dialing a secret code.
NOTE: This function is not available for XStealth Lite
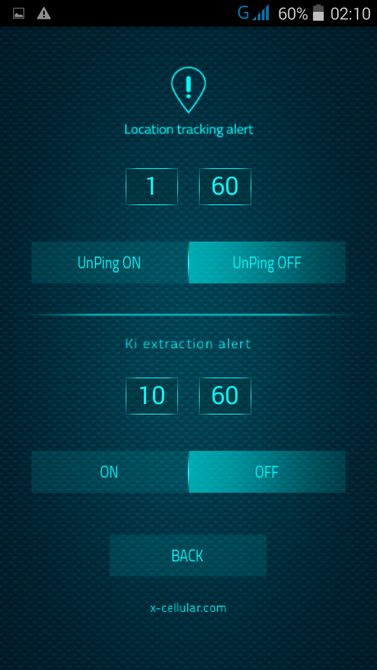
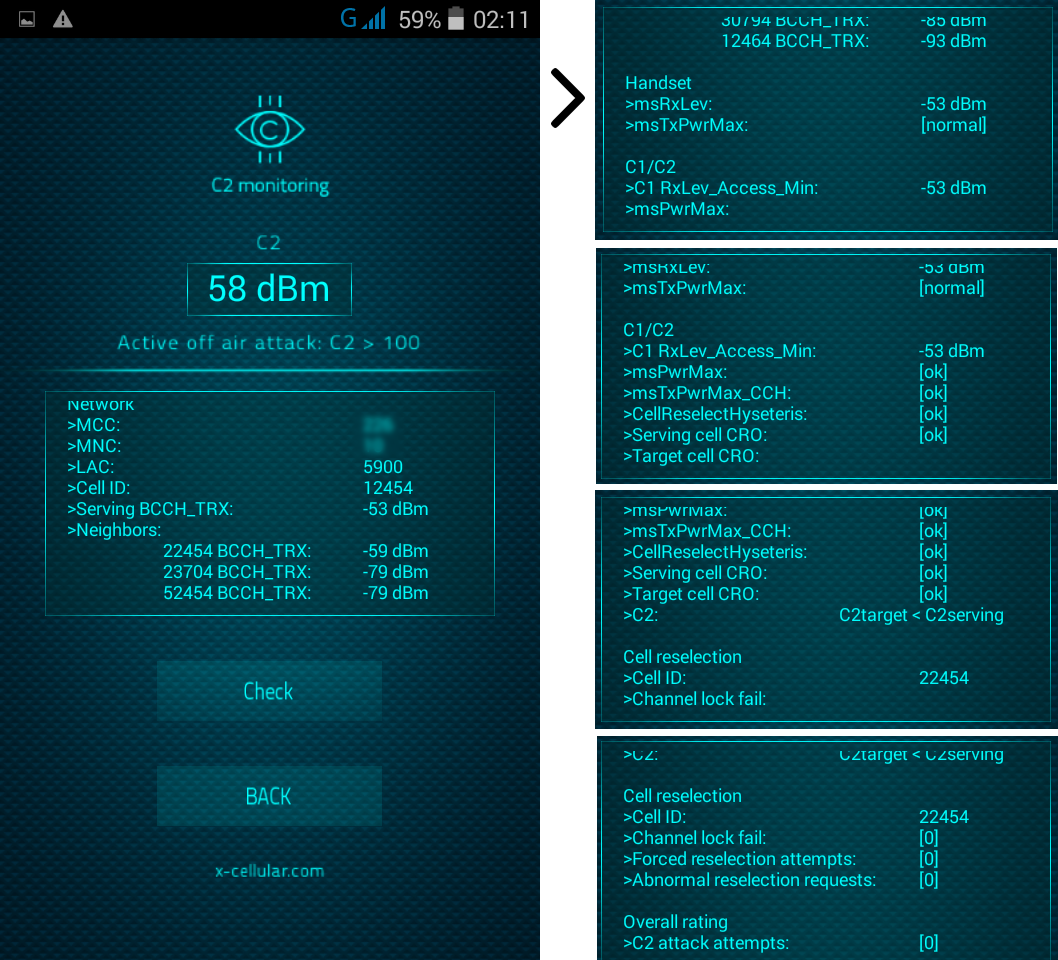
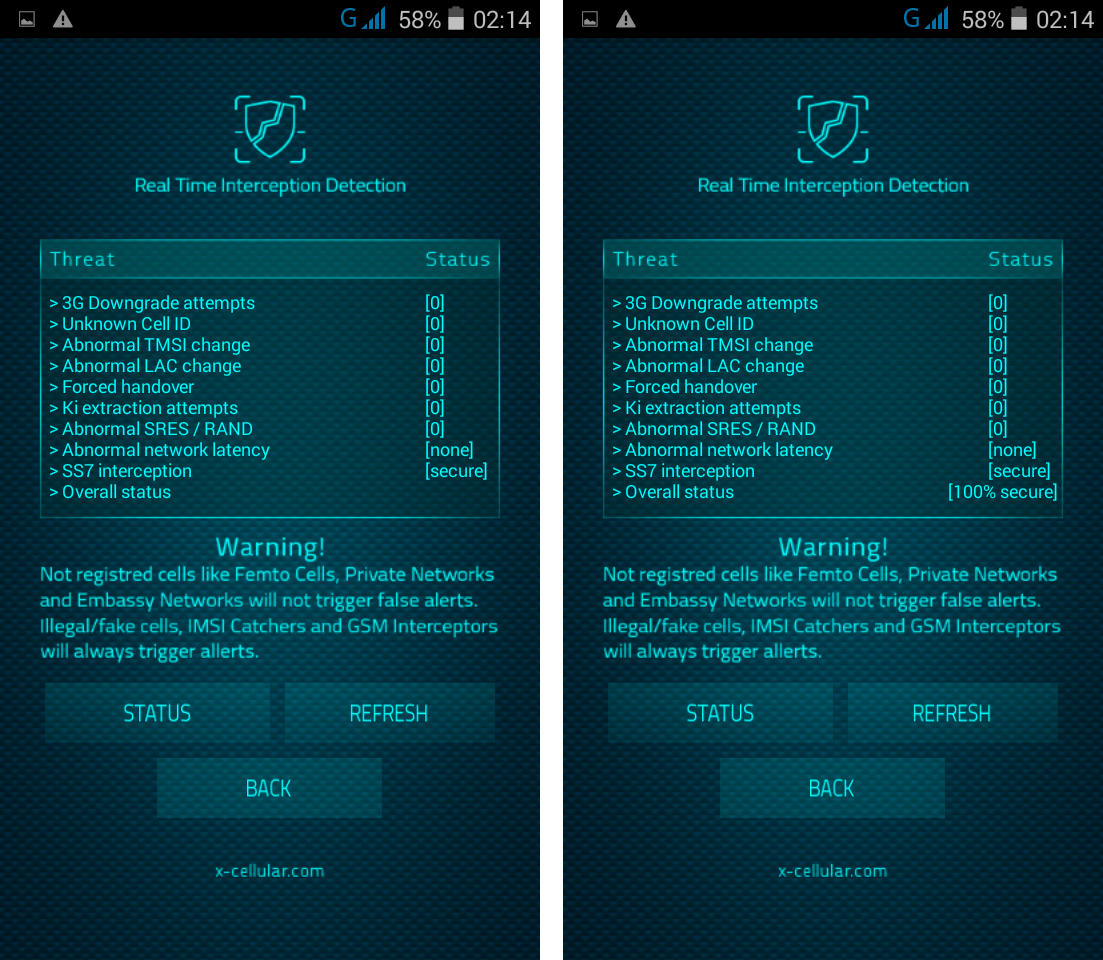
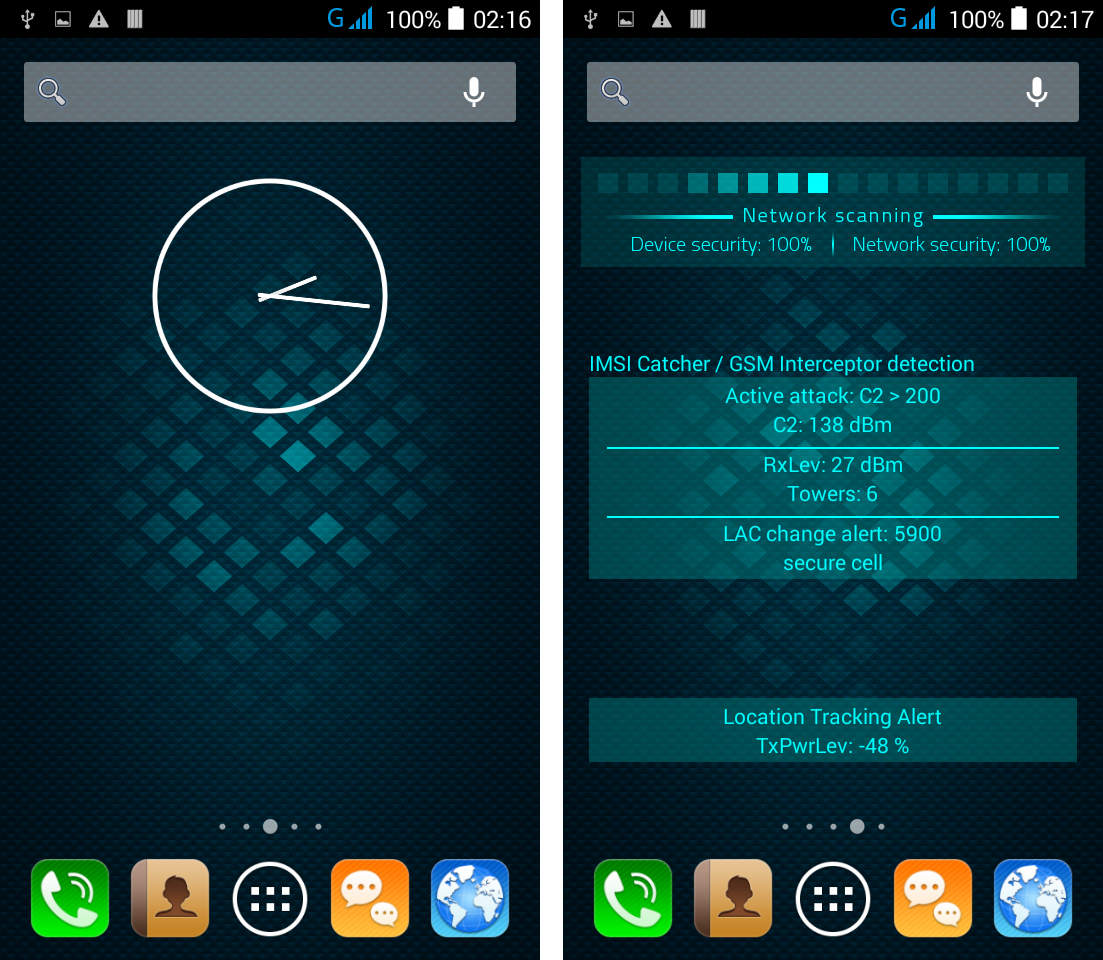
Ki extraction alert: every time when a GSM Interceptor is trying to get Ki (encryption key stored on SIM card) by sending so called "challenges" waiting for SIM replies with parts of encryption key, for later Ki calculation.
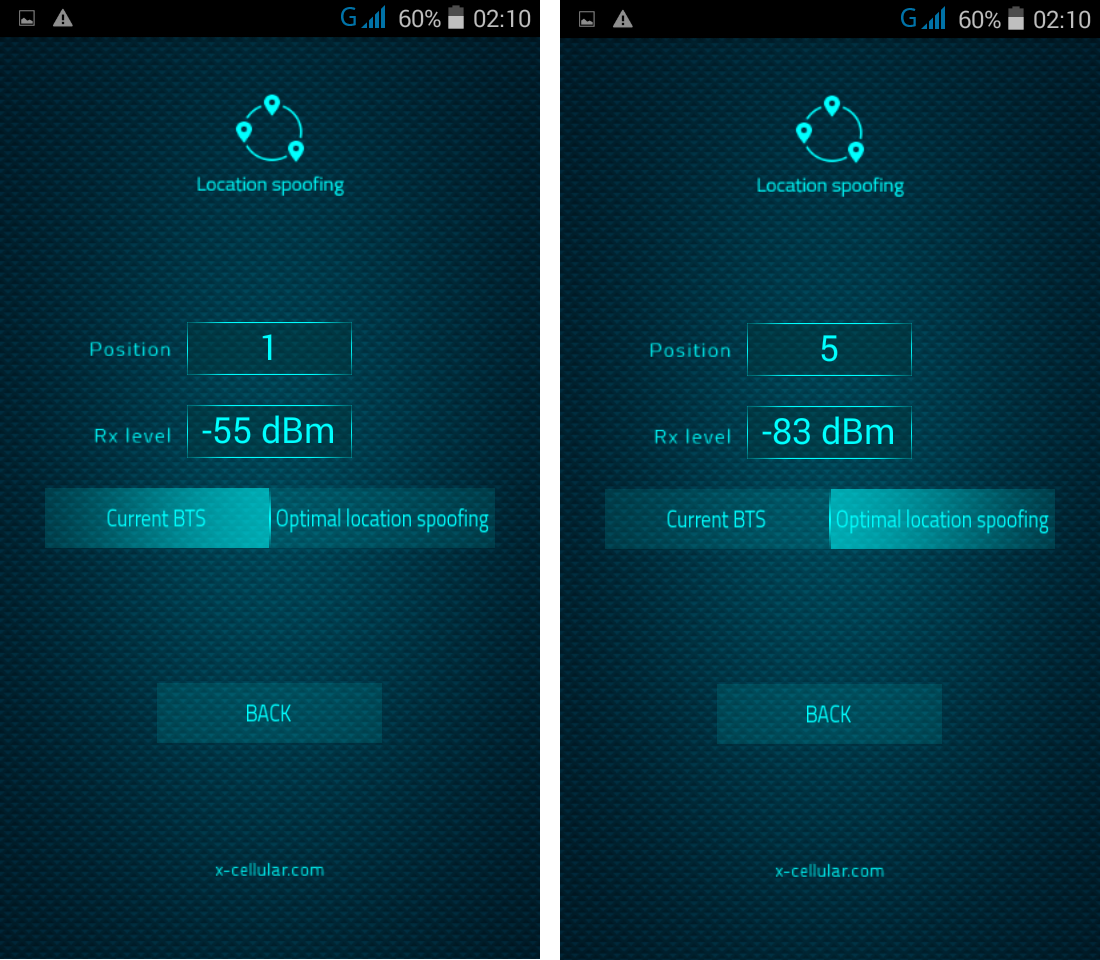
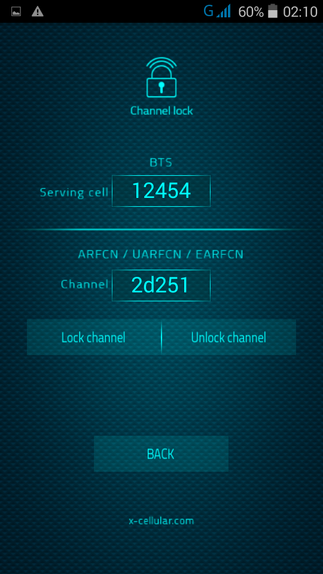
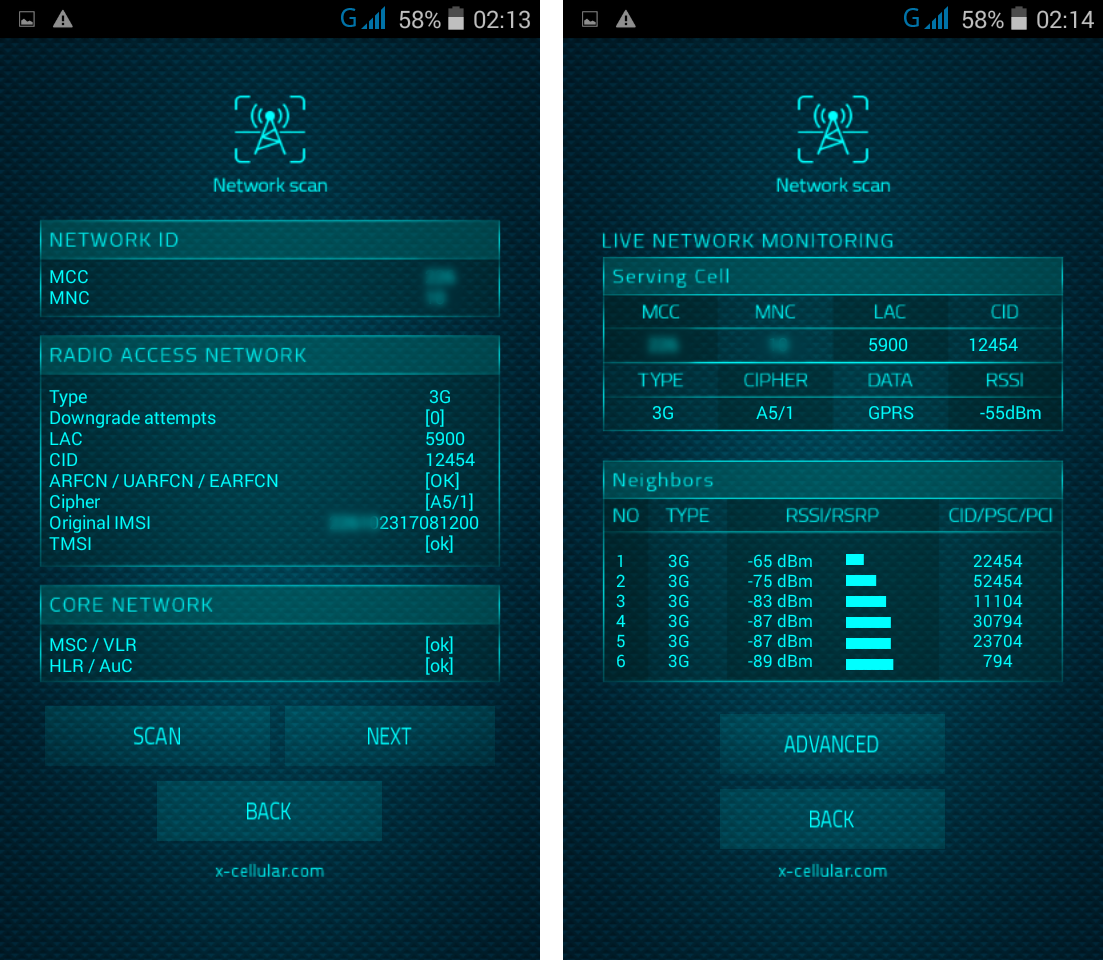
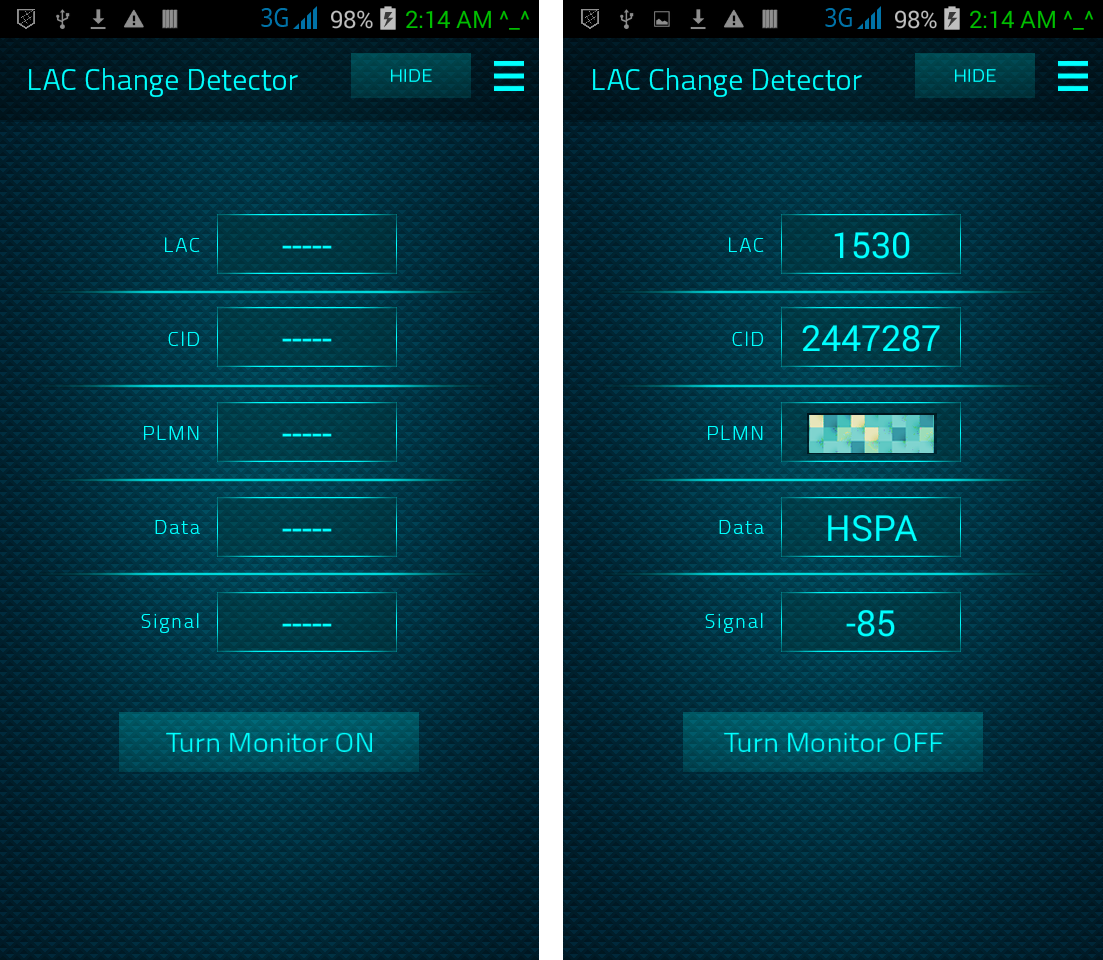
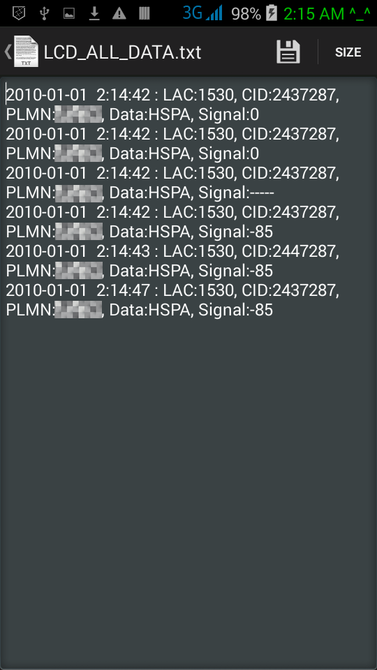
13. LAC Change Detector. This is the Proximity Alert Function. The phone will detect any abnormal LAC (Location Area Code) when stationary, changes made only by IMSI Catchers/GSM Interceptors in order to force connection
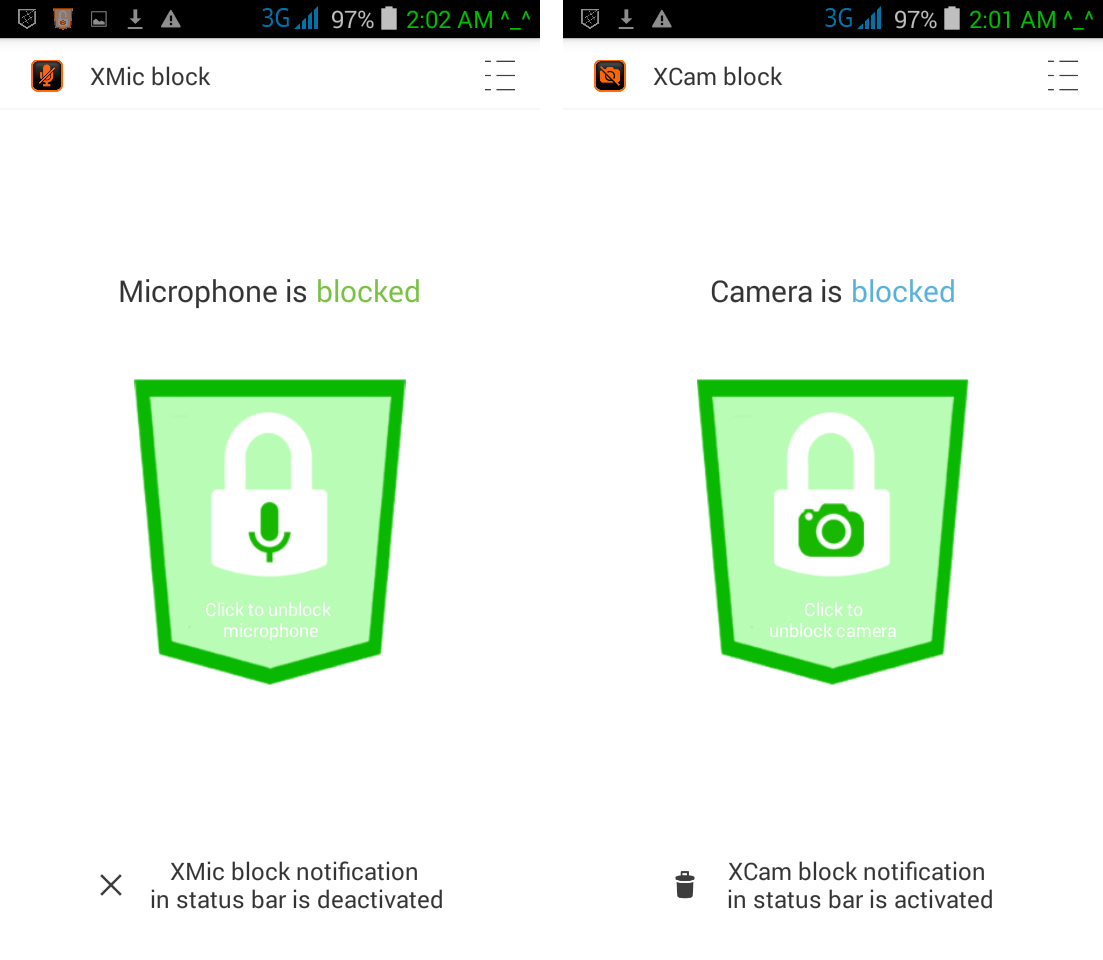
15. Camera Lock. User can lock the camera at any time, preventing remote activation for spy pictures/movies
For easy of use, main monitoring and warning functions are displayed also on the home screen. Since main home screen looks anonymous and like any other smartphone, by a simple screen swipe all monitoring functions will pop up on the screen.
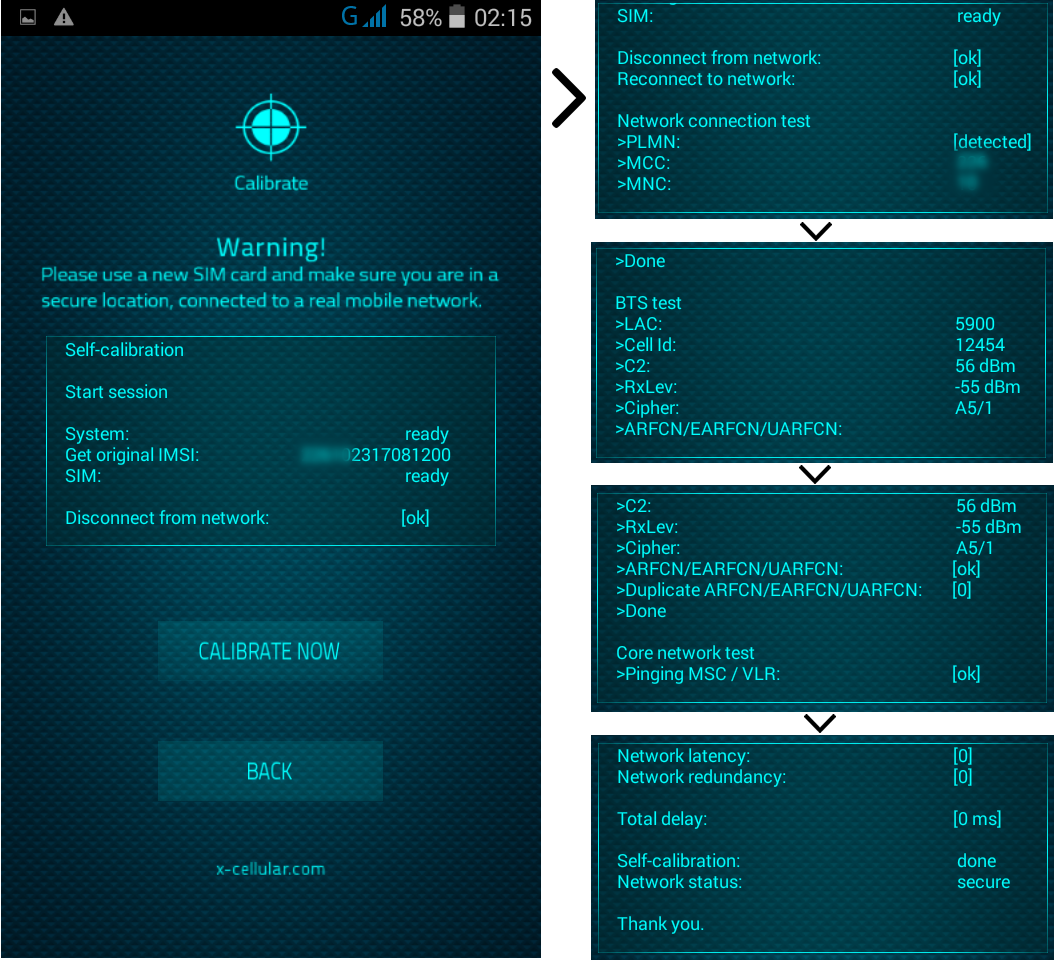
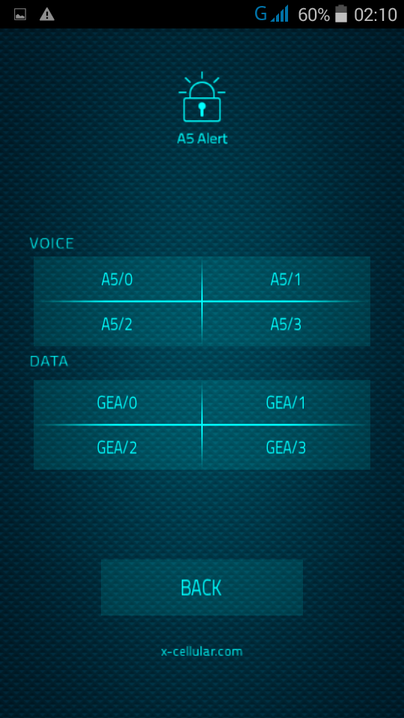
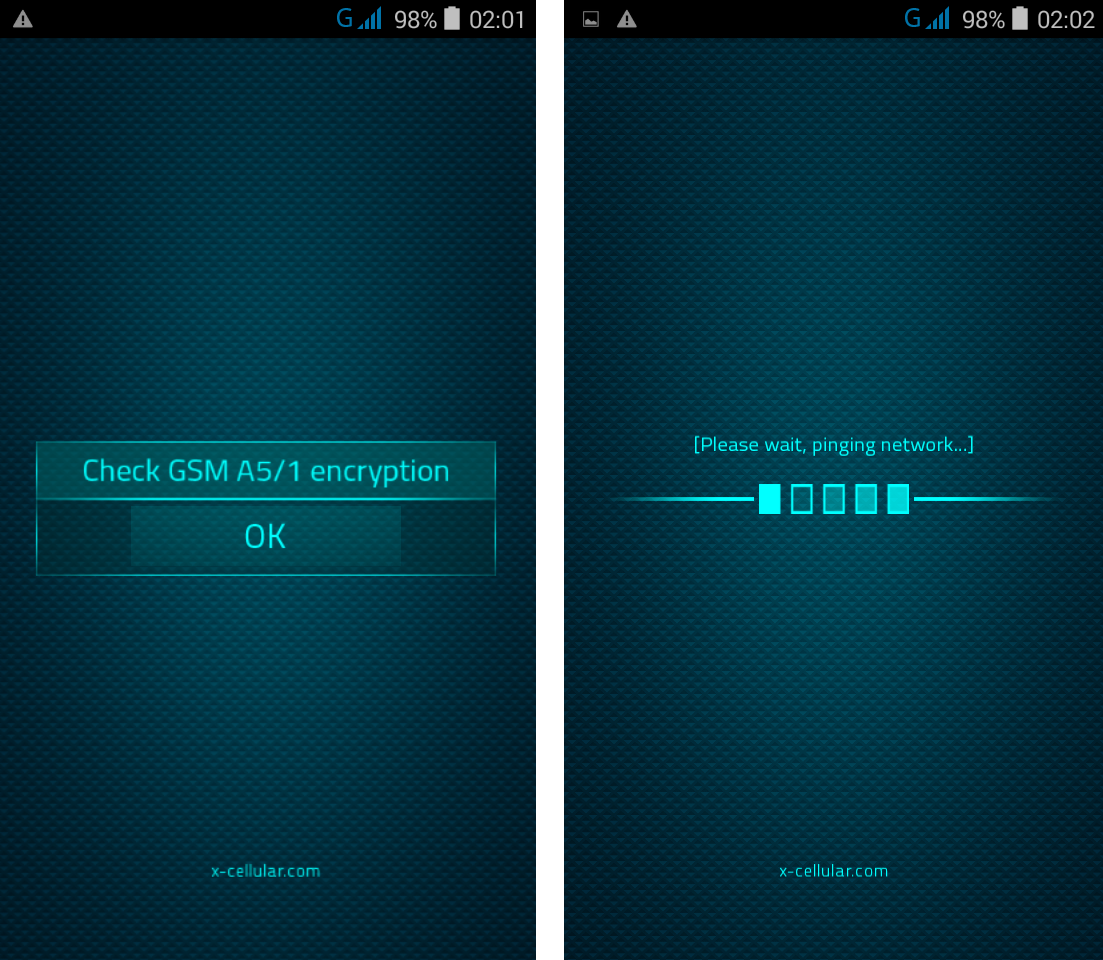
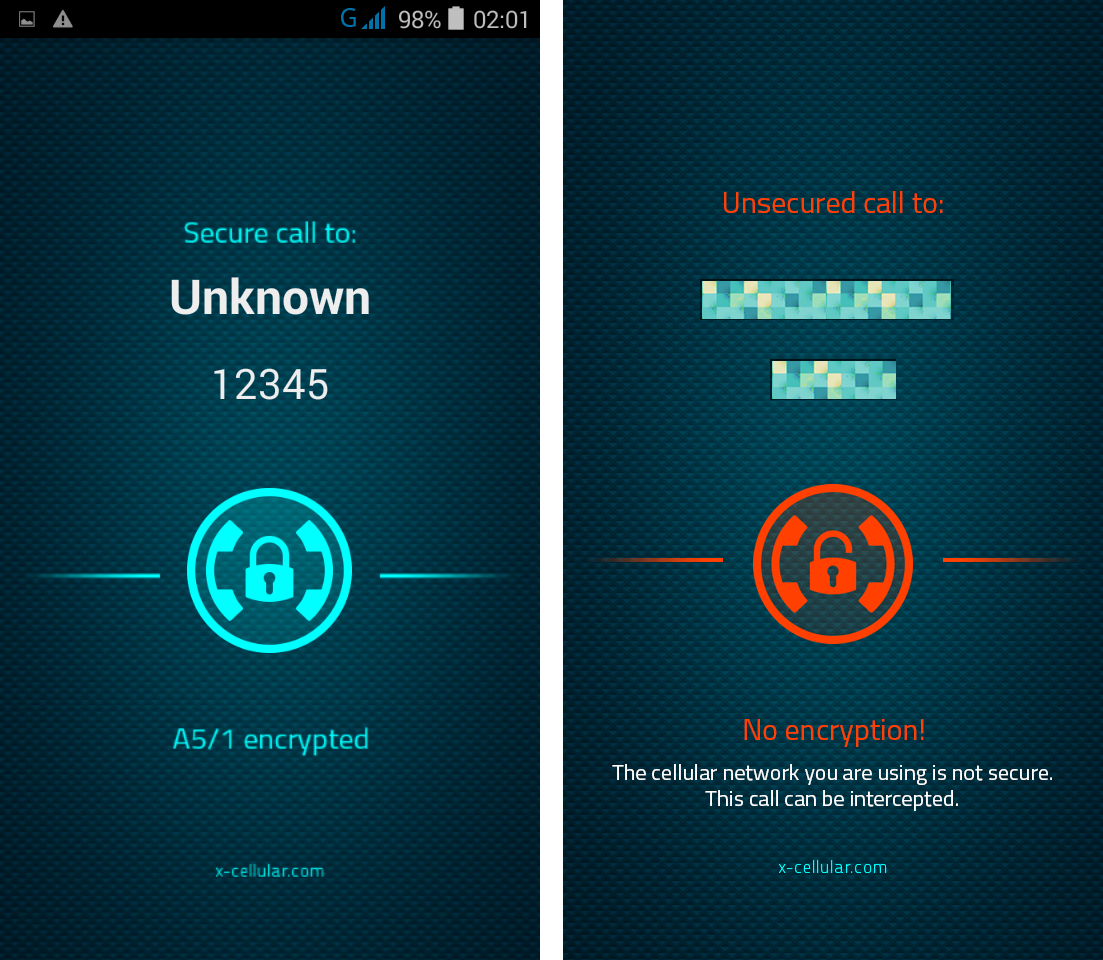
Every time when user is making a call, the phone will check for standard GSM network encryption (A5/1) detecting if the call is intercepted off air (by a GSM Interceptor) or at network switch level (SS7), by pinging the network core. In case of call interception, the phone will display a visual alert.
- Proton Mail
- Proton VPN
- Tutanota client
- Telegram X
- Hotmail client
- Yahoo client
- Microsoft Outlook client
- PayPal client
- Facebook lite client
- Messenger client
- Fire Onion
- Orbot
- Tor
- Orfox
- Anti-theft security & alarm
- Security Lock
- Secret Photo Video Locker
- Open Signal - a comprehensive cell tower locator
- Burner: temporary disposable phone numbers

 RSS Feed
RSS Feed