Advanced Nokia 3310 Stealth Phone have the following functions:
1 - Call/SMS interception alert (active, passive and SS7 interception);
2 - IMSI Change which is transforming the phone in a real sophisticated counterintelligence weapon. IMSI Change function does not require any Internet connection, third party servers or monthly subscription. This special function runs locally on the phone (Sandbox partition), being a unique function which no other phones offer at this time.
IMSI Change function allow user to change IMSI value (SIM registration number stored on the SIM card), by keeping the same phone number (MSISDN).
The phone will clone any SIM card inserted (please use only MNO SIM Cards) by using a Sandbox located app: IMSI Virtual Engine. Once cloned, the real SIM will be quarantined, being used instead a virtual SIM card which can change its IMSI by by generating valid IMSI’s. Please note that abusing this function can generate SIM network rejection (network dependent). Use it carefully.
IMSI Change does not work automatically, as IMEI change works. The user should launch IMSI Change every time when a new IMSI is needed, generating a new virtual IMSI and then exiting the application. The new generated IMSI will be used only for the next outgoing or incoming call. After that, the phone will return to original IMSI. If a new IMSI will be needed, the whole process should be repeated.
Please note that MSISDN (the phone number) will not change when using IMSI change function.
IMSI change function will transform your Nokia 3310 Stealth Phone in one of most powerful communications weapon: you will literally have a new SIM (IMSI) for every single phone call. Use it with precautions.
3 - cryptoTRACERⓇ, which is a function that can detect lawful interception performed by SS7 Boxes (aka Network Switch Based Interception);
4 - Sandbox
IMEI engine and other software components has been moved in a separate partition (Sandbox) in order to make them working faster and smoother. System restarting has been suppressed in case of any abnormal network characteristics (i.e. generated by IMSI Catchers/GSM Interceptors).
5 - Interception Instant Check
Once launched, the function will start checking both Active and Passive interception, step by step. Regarding interception performed with Active/Semi Active GSM Interceptors, the phone will check:
1. BTS parameters
2. RSSI
3. Cell ID
4. LAC
5. ARFCN
6. Ki retrieving attempts (ciphering key stored on the SIM card).
7. Baseband attack attempts.
Regarding interception performed by Passive GSM Interceptors, the phone will check:
1. Uplink.
2. Downlink.
3. Will ping HLR/VLR core network, computing network redundancy and abnormal ping delays.
4. In the end, will generate a Network Security Rating.
6 - C1/C2 monitoring
By forcing cell reselection (C2 parameter), Active and Semi Active GSM Interceptors will force any cell phones to disconnect from home network and connect to the rogue BTS impersonated by the equipment. This is called also BCCH manipulation, being used by all modern GSM Interceptors. When launching this function, the phone will:
1. Extract C1 value, from serving cell.
Will compute C2 value by using a special algorithm, the same used by any GSM network
2. Will look for at least other 6 neighboring cell towers, ordered by RSSI value.
Will compare C1 to C2.
3. Will trigger alert if no neighboring cells are found (a clear indication that a GSM Interceptor is active within area).
Will look for CPICH, RSCP and BCCH.
4. Will display forced handover attempts (if any).
5. Will display Channel lock fails (if any).
7 - Military grade SMS encryption. Please note that you need at least 2 units in order to use SMS encryption feature.
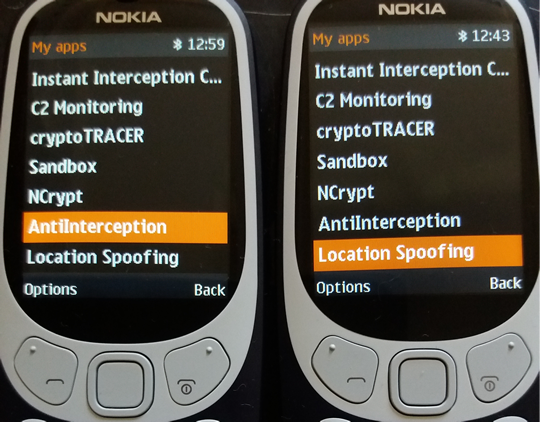
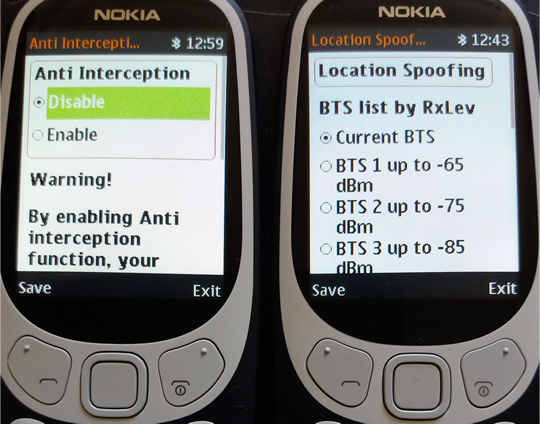
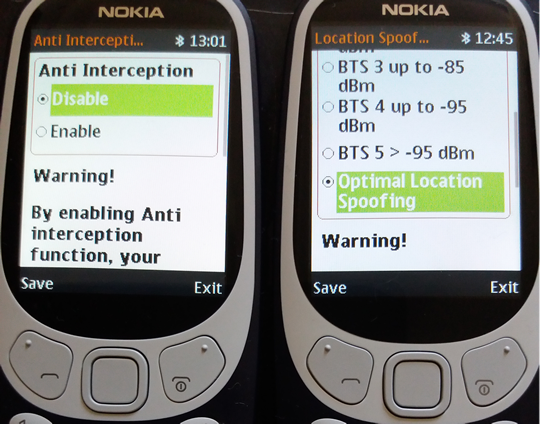
8 - Anti Interception: as long as phone is under surveillance by any means (no matter if IMSI Catcher, GSM Interceptor or SS7), voice calls and SMS will be blocked (both incoming and outgoing).
9 - Real Location Spoofing: user can hide GSM location by selecting the farthest BTS which phone is connected to, avoiding this way triangulation procedures widely used by law enforcement for location tracking purposes. Will work both when stationary and on the move.
You see below actual pictures of special functions added to XCell Basic v3 Advanced Stealth Phone.
Taking advantage on GSM network architecture and SMS Transport Protocol, our SMS encryption technology is capable to send/receive encrypted and non-interceptable messages.
Please note that for exchanging encrypted messages you need at least 2 phones: sender phone will encrypt the message and receiver phone will decrypt the message.
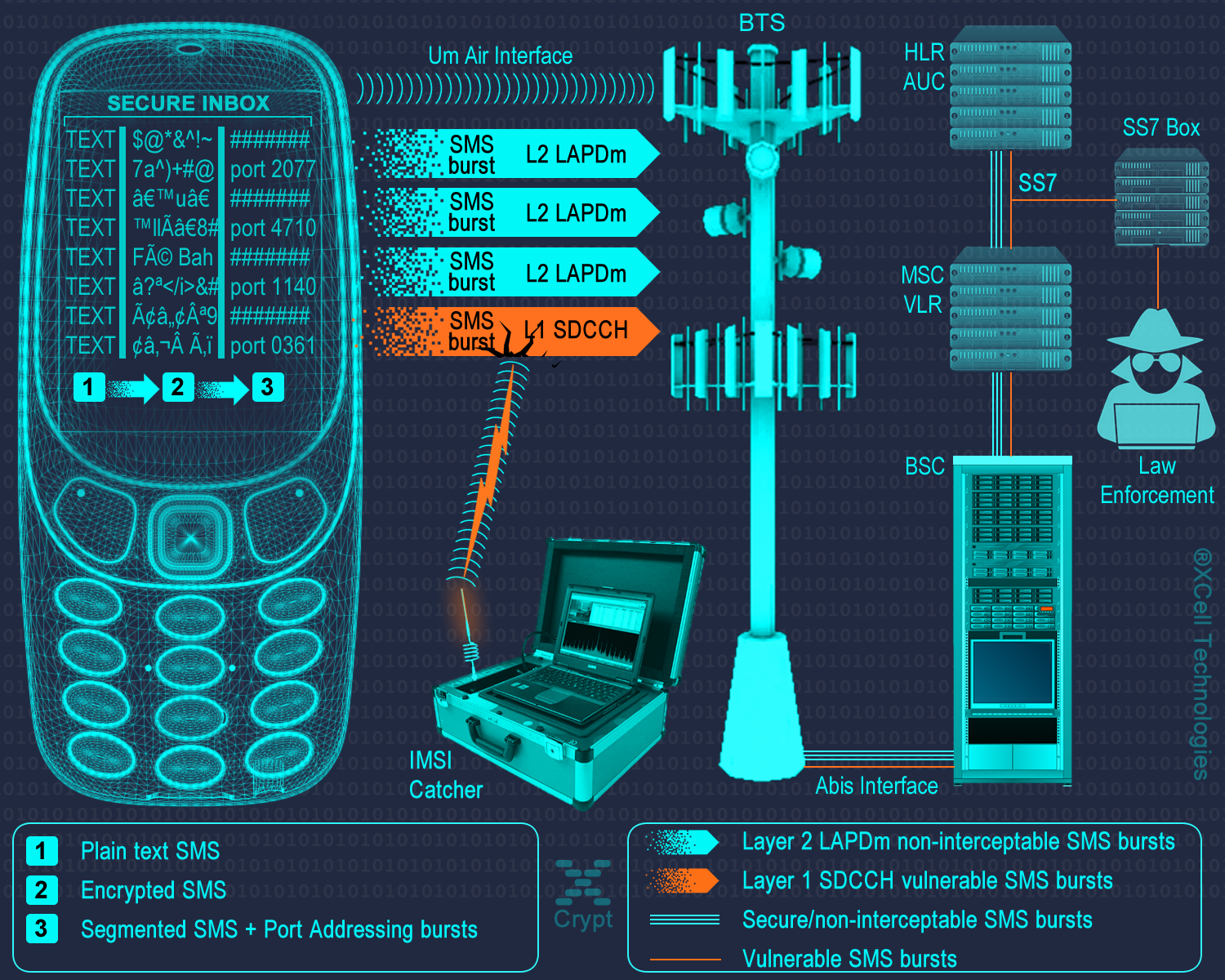
1. Physical layer: encrypted text message.
The phone will encrypt text messages by using following protocols:
• RSA
• AES 256
• Elliptic Curve (ECIES) 256
• SHA256
• Protected by ITSEC Evaluation level 3
2. Multi-layer routing and transport protocol. Encrypted SMS data is randomly segmentated and distributed in bursts by Application Port Addressing Technology, via discrete GSM channels which usually are not "listened" by mobile interception systems (IMSI Catchers, GSM Interceptors or StingRays), both in air interface (UM Interface in terms of GSM networks) and Abis, A and C-G mobile network interfaces. This way, SMS data which is usually sent over GSM Layer 1 (and widely intercepted on Layer 1) will be sent by using a combination of GSM Layer 1 and GSM Layer 2 (LAPDm). By consequence, no mobile interception systems (as GSM Interceptors) and lawful interception systems (SS7 interception also known as network switch based interception or interception by the help of network operator) will be able to intercept the whole message but only a few bursts which are encrypted anyway.
3. Metadata protection. Regular SMS metadata is not saved in a separate file (called a metadata file). XCrypt separate metadata and the data it describes (SMS encrypted text), sending metadata file in bursts over the network, by the same Port Addressing technology. Metadata is of little value without the data file (SMS) it relates too. At the same time, metadata makes the data more usable and therefore, more valuable. An encrypted text message with separate metadata file will reveal nothing about SMS sender and receiver.
You can download the whole PDF document regarding MLSP@ technology and XCrypt applications, by clicking on image below:



 RSS Feed
RSS Feed