Preliminaries
The test
Most of people have no idea what IMSI is, and also no idea on how to get it from their own SIM card. Moreover, they have no idea what can be done when someone is getting IMSI from your SIM card. So let's start testing. No need for any technical skills, special knowledge or payments.
Test no. 1
Whether you have a classy Android or swanky iPhone, you can test your new bought "anonymous" SIM card, right now. Just go to Google Play or App Store and install any app that shows your SIM card info. Example: Whats My IMSI.
On iPhone is even simple: go to Settings menu and from there you pick "Mobile Data". Choose "SIM Applications" and that's pretty much you have to do.
Got your IMSI now? Good. Now you can throw away your "anonymous" SIM. And have a look on your window: your "protected" calls might actually "call" the police straight in front of your gaff.
The IMSI you can see is being used by your phone when connecting to any cell tower, in order to make/receive calls and messages. There is no other way around. The phone cannot connect directly to any "telephone switchboard", as scammers pretend. Because "telephone switchboard" is not a cell tower. Your phone call is routed first trough local mobile network, then trough SS7 network, to recipient mobile network. In this particular case, your phone call is also routed trough your "anonymous" SIM issuer servers located in Russia, before reaching recipient local network. Hence, instead of "hardened" security you've got less security than you have expected. And sure, with an extra payment which will make you think that is serious yet affordable security.
Test no. 2
The business
The SIMs behind the business
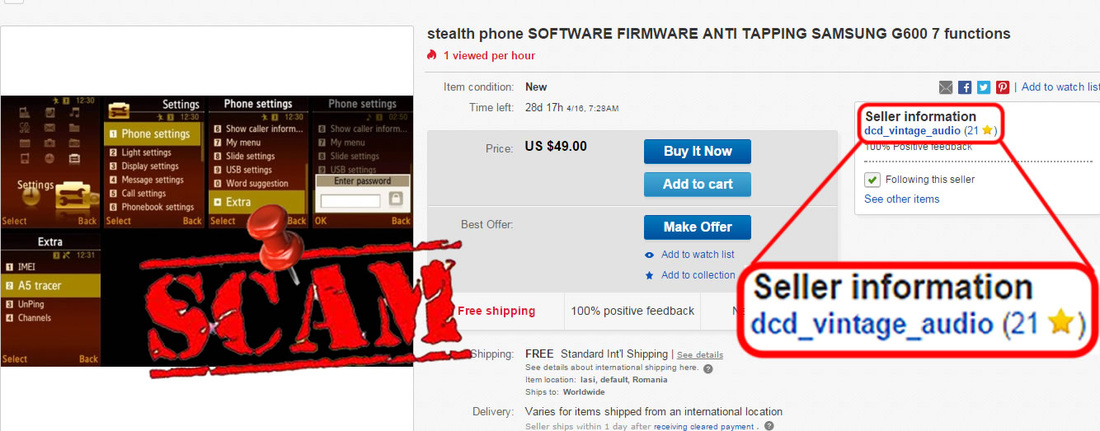
Straight forward: there are no anonymous SIM cards. This is technically impossible. All of them are just a big time scam that take advantage on lack of knowledge from regular people. And nothing more.
Fact: there is no SIM card without an IMSI.
Fact: there is no connection to a cell tower without IMSI being used for connection purposes.
Fact: even data only SIM cards have an IMSI assigned by the manufacturer.
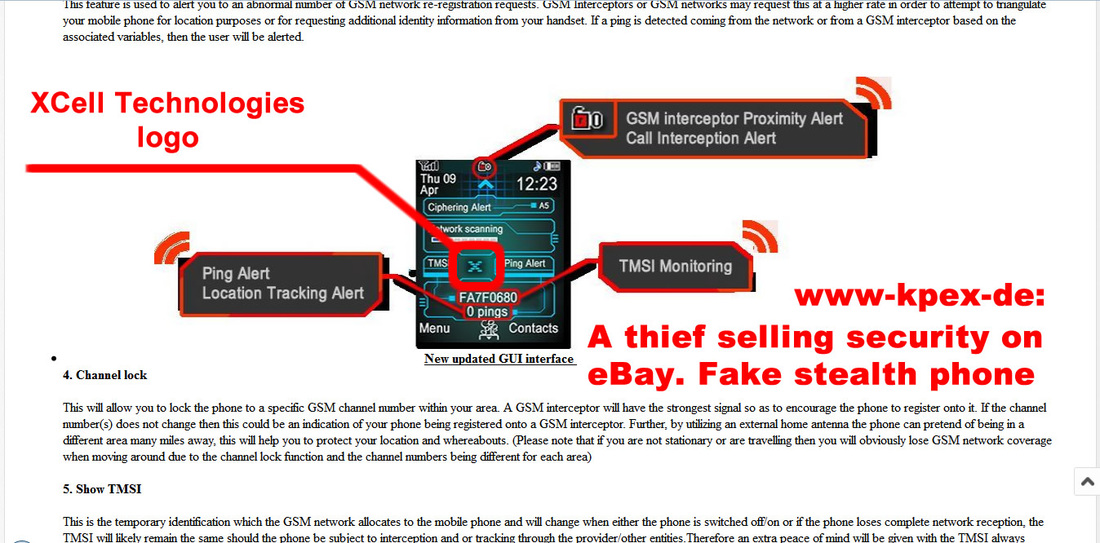
Fact: there are so called IMSI catchers, designed especially for call/SMS interception based - as its name says - on IMSI.
Fact: if you can call whatever number or you can receive calls, that means your phone is connected to a cell tower, by using voice/data channels.
Fact: once connected to a cell tower, almost ANY cell phone location can be (and it is) tracked by various technologies and systems, taking advantage on mobile network weaknesses or mobile network nodes (SS7).
Fact: once connected to a cell tower, any phone call can be (and it is) intercepted, no matter if voice call is routed on standard voice channels (regular voice call) or on data channels (as Skype, IM, WhatsApp, etc.).
Fact: not the SIM card is choosing the cell tower to connect on it, but the phone. This is the way that all mobile networks are designed (no matter if 2G, 3G, 4G, etc.), a SIM card being only used to identify a certain subscriber.
Fact: the phone number is not stored on the SIM card. Phone number is stored on mobile network servers (HLR/VLR) and cannot be altered/changed directly from the phone/SIM. A phone number can be altered/changed ONLY by using data connection and 3rd party servers. Some particular "russian SIM cards" are using standard voice channels that still route the call trough some russian server, where in fact take place voice changing, and only then the call is routed to call recipient.
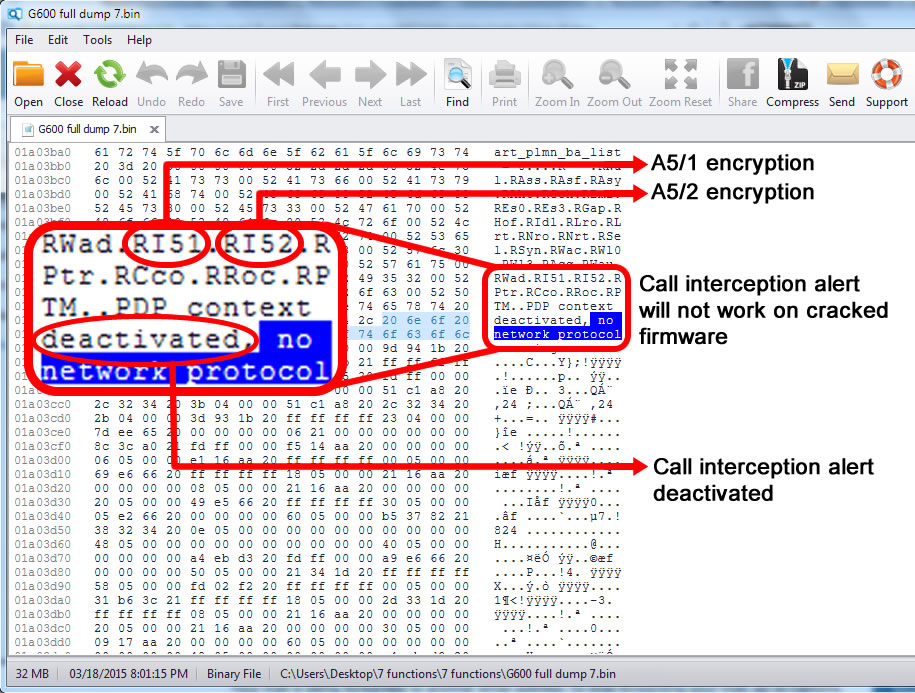
Fact: ANY SIM card is encrypted by default, using comp128 algorithm. There is no other encryption that a SIM card support. This is meant for anti-cloning purposes. Some early comp128 versions has been compromised, old SIM cards (until 2012) being easy to clone.
Fact: ANY regular phone call on ANY mobile network (no matter if 2G, 3G, 4G, etc.) is encrypted by default. Otherwise, anyone with a radio receiver can intercept that call. A SIM card CANNOT ad another layer of encryption on top of existing one, nor additional encryption.
Fact: ANY SIM card is trackable and any phone calls and SMSs done with a SIM card can be intercepted.
Fact: IMSI is not the same with phone number, nor with ICCID. IMSI is stored on SIM, since phone number is stored on carrier servers.
Fact: IMSI is not printed on SIM, but ICCID.
Fact: anyone can figure out its own SIM card IMSI, by using freely available apps (both on Google Play and App Store). If you average Joe can do this, then law enforcement or hackers can do that remotely, over the air.
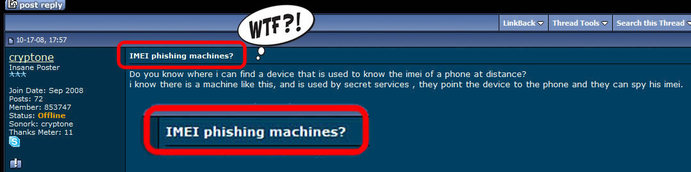
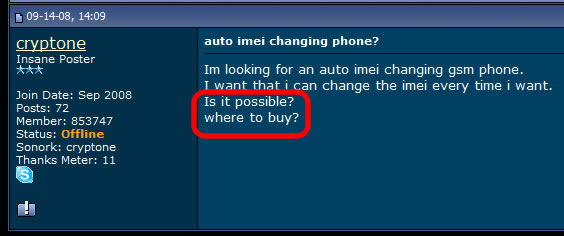
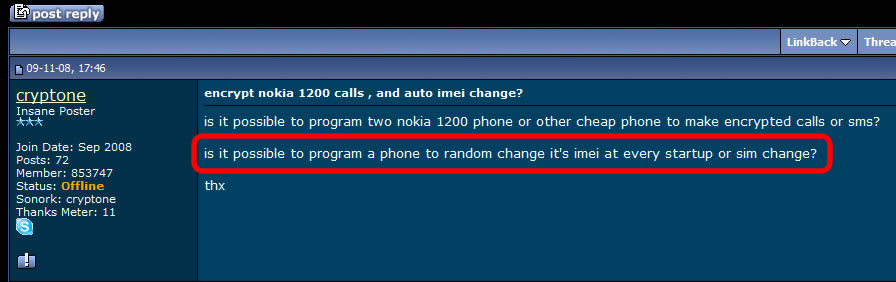
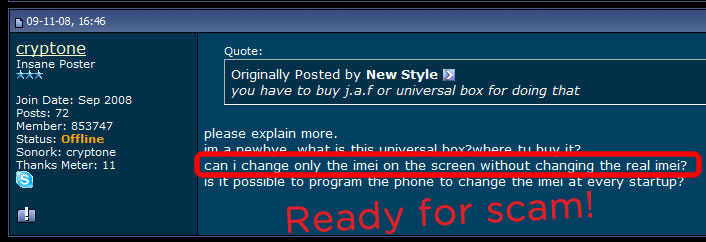
Fact: IMSI change is possible by sending special requests to SIM issuer (the mobile network that issued that particular SIM). The request cannot be sent directly by the SIM user but by other company, in his name (used for example when porting a phone number). Changing IMSI this way is not a standard procedure, despite the fact that IMSI change is mentioned on GSMA and 3GPP procedures. Fraudulent MVNO companies (mostly russian) are taking advantage on this procedure, enforcing the law because the MNO doesn't care, changing SIMs IMSI based on user direct request.
Started back in 2014, anonymous SIM card scam refers to a few types of SIM cards that are being sold to people without a decent knowledge regarding mobile networks:
1. Pay as you go SIM cards (aka prepay SIM)
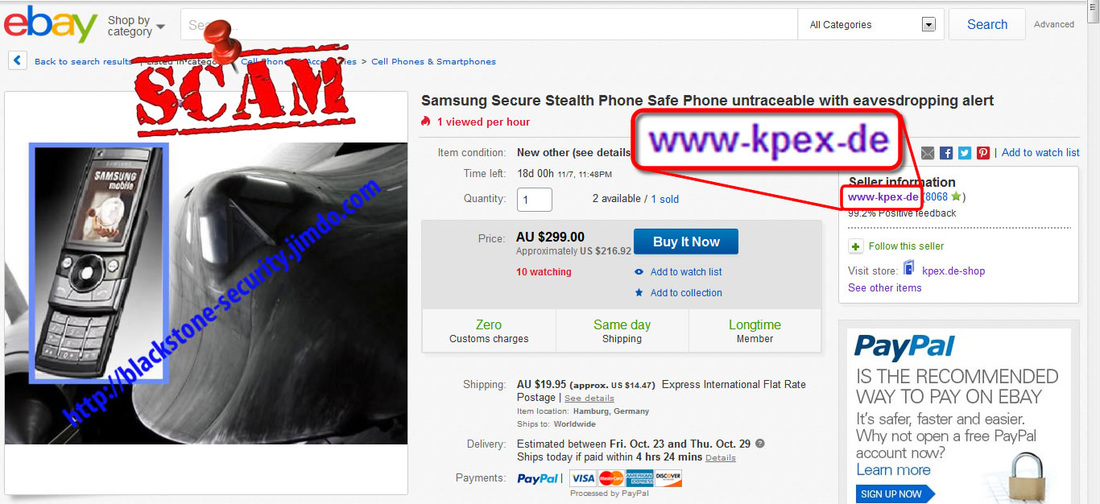
Some European countries as well as non European ones still issue pay as you go SIM cards with no need to show any personal ID and with no prior registration. This type of SIMs are considered "anonymous" just because there is no connection between user name and phone number. There are no other "special" features or "security hardened" things, whatever that means. At first sight, using a pay as you go SIM (eventually issued by a foreign carrier) looks as an advantage for SIM user. But stepping down on real life, this is what is happening: when a suspect is using whatever SIM, law enforcement ground teams are using IMSI Catchers and/or GSM Interceptors that collect both SIM IMSI and phone IMEI, for further tracking and monitoring. Hence, doesn't matter if the suspect is using a pay as you go SIM: IMSI catcher has done the job, matching all together: suspect identity, SIM identity (IMSI) and phone identity (IMEI). Simple and effective. A good article regarding this type of anonymous SIM scam can be found here.
2. SIM cards that have so called "multi IMSI" option.
This is nothing unusual, and are not adding any additional security to phone calls or location tracking. Just google it by yourself. Multi IMSI SIM cards are sold worldwide by various carriers as SIM cards for frequent travelers which can have up to 4 different IMSIs, corresponding to 4 different phone numbers. The user can choose which IMSI (phone number) is used at a time, by local low rates policies. Nothing to do with additional security or dynamic IMSI change. This type of "anonymous" SIM cards create a false security feeling just because user can alternatively choose from 4 phone numbers to use. Any multi IMSI SIM card can be tracked and intercepted as any other SIM card.
3. Russian "anonymous" SIM cards.
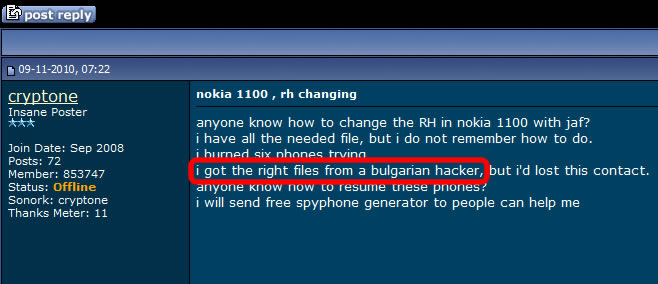
These are SIMs issued by russian MVNOs, which have assigned 1 or multiple IMSIs (up to 4). To place "anonymous" calls, the phone (along with the SIM) will connect to the closest cell tower, by disclosing both IMSI and IMEI. There is no other way around. IMSI and IMEI have to be used in order to connect to the network. Hence, no anonymity: since IMSI and IMEI are disclosed, a wide range of tracking procedures (SS7, GSM Interceptors) are possible, also call interception and SMS interception are just a kids play. Going further, the call is rooted from local mobile network (which is the first weak link that instantly disclose user identity), to russian MVNO servers, where phone number and voice are eventually changed (if user choose to use voice changing and phone number changing), and then the phone call is finally reaching the recipient number. What this clowns are trying to hide from you by taking advantage on your lack of knowledge regarding GSM network standards and specifications is the call route: instead of standard call route (simplified: cell phone > cell tower > core network HLR/VLR > network switch SS7 > russian MNO > russian MVNO servers > russian MNO > SS7 switch > recipient network HLR/VLR > recipient local cell tower > recipient cell phone), they claim that the call originating from your cell phone does not connect to any surrounding cell tower but to some sort of "telephone switchboard", which obviously is not technically possible. Do not forget that even when using data connection to place a IM call (Skype, WhatsApp, etc.), your phone will connect to THE CELL TOWER, by using the same IDs: IMSI and IMEI. In other words, unless you are using WIFI, any call will go trough nearest cell tower, no matter which SIM you are using. With a lot of nonsense blah blah and using apparently a technical vocabulary just to make you think they are professionals and/or skilled hackers, a vocabulary that in the end of the day will probably convince you by confusing you, scammers succeed to sell SIM cards as "anonymous" SIM cards.
We all know that SS7 network is compromised, but it takes more than a few keystrokes to abuse the SS7 network: it takes expertise, money and more important - SS7 access. But from what we have seen, once attackers have all 3 they are making sophisticated use of SS7, because once you have this ability, you want to exploit it fully. The real problem with these unscrupulous russian MVNOs is the access they have to SS7 nodes based on contracts they have with other international carriers, access that make available for them a wide range of SS7 exploits, including call interception and location tracking.
* Anomalous, but not malicious traffic. This can be everything from malfunctioning nodes, attempting to send for all subscribers rather than their own, to unusual implementations of legitimate services, to anything else which is not known to be malicious. The skill here is in identifying this and making sense of what is malicious and what isn’t – not always easy to understand.
* Malicious attacks, up to a medium-level complexity. These are the more well-known location tracking, fraud and information harvesting attacks, and were the main type of attacks that operators encountered when they started to investigate SS7 security in depth. As time has gone on, the perception of ‘simple’ has risen in complexity to cover more and more types of attacks.
* Malicious attacks, of advanced complexity. This is the type of attack that takes investigation to even identify in the first place, and once identified requires detailed understanding of what the attacker is trying to achieve and how, in order to build consistent defense against it. These are the most advanced type of attacks they will increase in complexity as time goes on.
We are actually seeing a progression over time (i.e. over the last 2 years), where some of the attackers who have access to the SS7 network have progressed to trying to use more and more sophisticated methods to achieve what they want, especially now that a large number of operators have begun to implement defense. Most relevant example: ULIN.
One more thing: as always when something is too nice to be true, you never know who is really hiding behind that servers. You have no means to check that russian MVNOs and its hidden strings that eventually lead to local intelligence services.
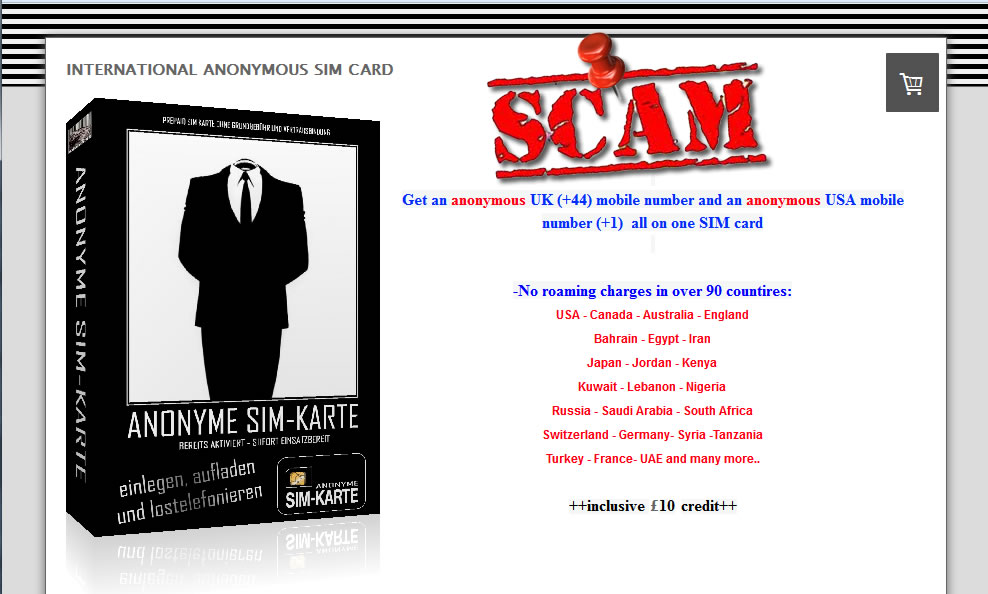
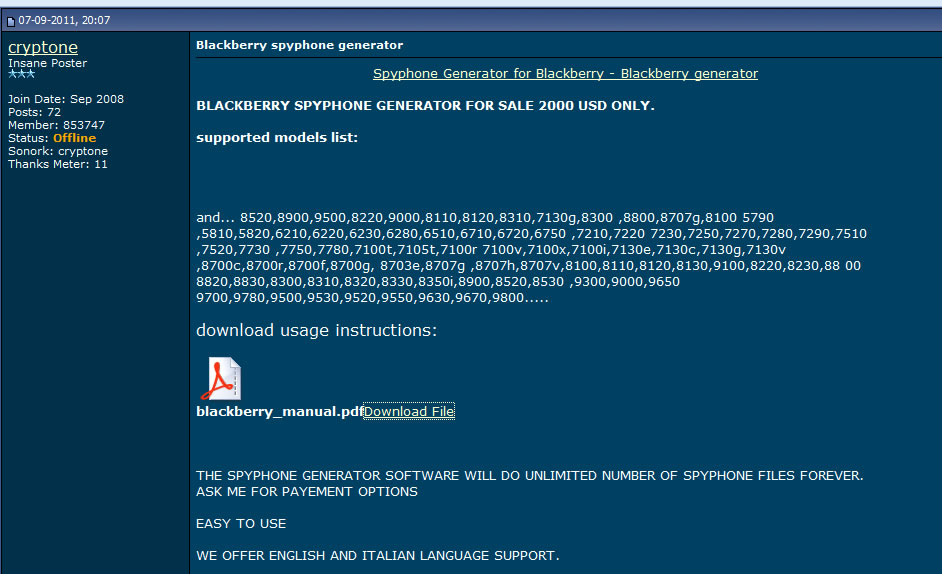
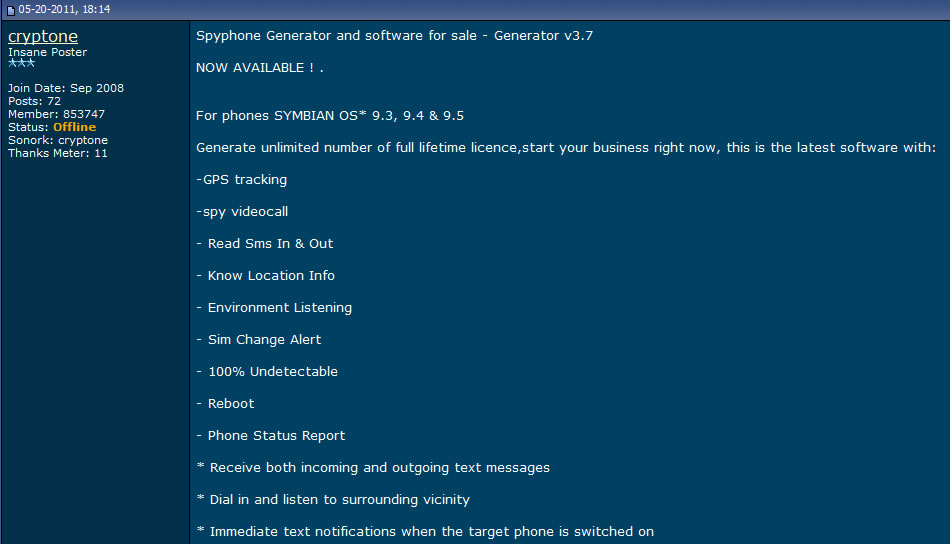
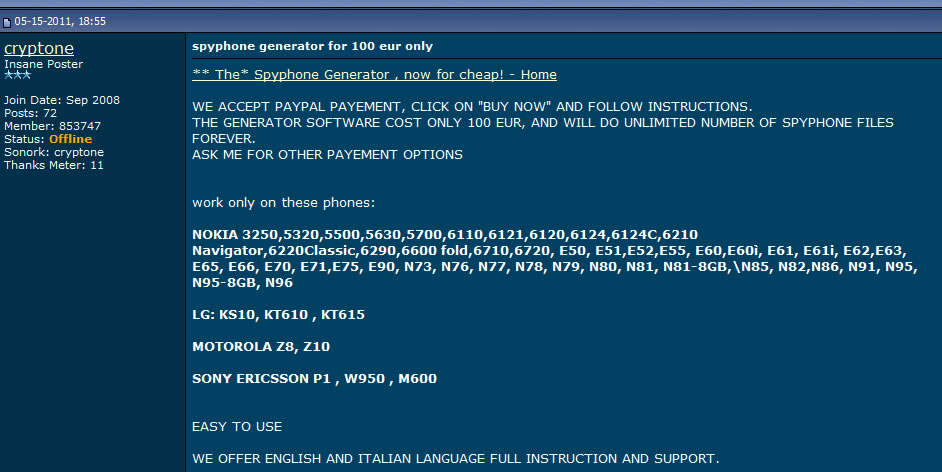
4. Writable/Programmable blank SIM cards, widely available on Alibaba and other Chinese web shops, also on eBay and Amazon, at really low prices that comes in bundle with read/wright device and software. This way, you can make your own SIM card, with any IMSI.
This is all you need:
a. A programable blank SIM card
b. SIM card Reader/Writer device
c. Software (usually 128k Milenage algorithm and XOR algorithm, Matching the standards of GSM11.11, GSM11.12, GSM11.14, GSM11.17)
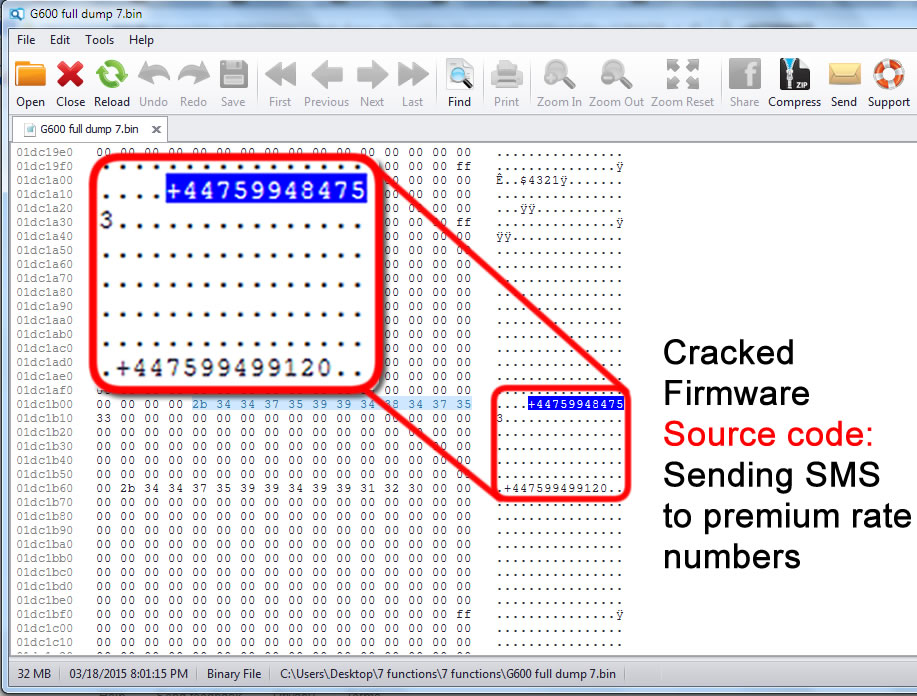
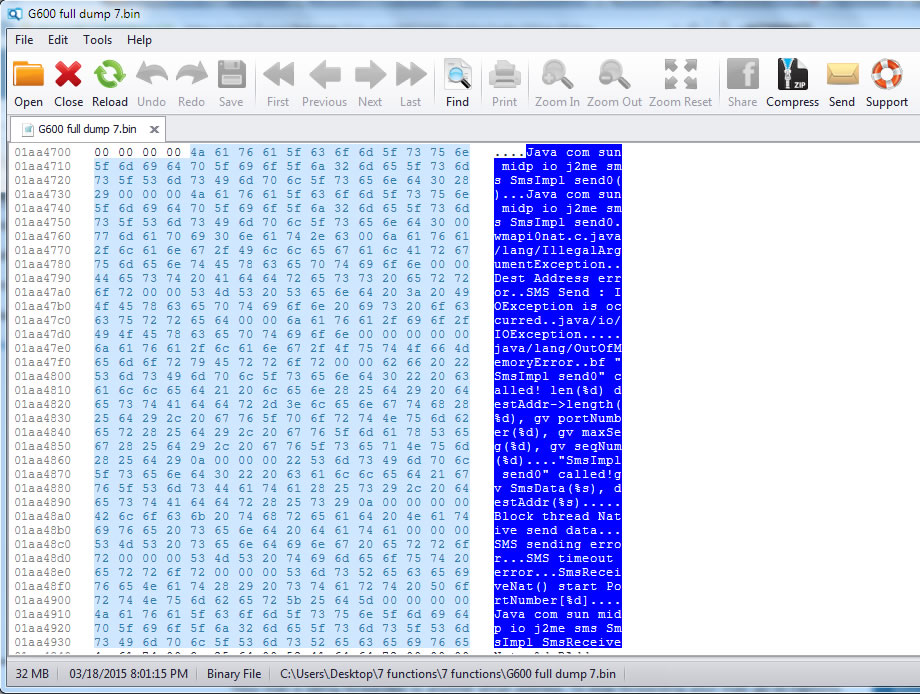
The (big) problem consist in Ki (encryption key) which need to be written on that new SIM. You need to know the Ki key, and there is no way to retrieve this key 99.9% of the time from another SIM card, because it is only known by the operator itself. This is why SIM cloning (comp128 v2, v3, v4) is not successful.
Ki problem can be easily solved by a malicious MVNO, which know the Ki and can program its own blank SIM cards.
Chinese vendors has solved this: SIM factory can program the SIM for you when ordering in bulk, including custom printing as you can see on most "anonymous" SIM cards. See it in action:
Cons
a. does not support GSM 11.14: digital cellular telecommunications system (Phase 2+) - specification of the SIM Application Toolkit for the Subscriber Identity Module - Mobile Equipment(SIM - ME) interface.
b. does not support GSM 03.48: security mechanisms for SIM Application Toolkit - Stage2 (GSM 03.48 version 8.8.0 Release 1999).
This mean that the SIM card is vulnerable to a wide range of remote SIM Toolkit attacks.
c. comes with STK menu that supports various applications, which can be updated by OTA download. That means you are not in control of your "anonymous" SIM card: various and potential dangerous executables can be downloaded and executed on your SIM, without your consent and acknowledgement.
The people behind the business
The victims
Phone number changing / substitution
Phone number changing take place on their servers, so the phone number will be changed only when routed call will arrive on their servers, on its way to called cell phone. The call is leaving your cell phone with the same IMSI and phone number every single time, and changes are done only when your phone call hits the server.
From the point of view of an IMSI Catcher or SS7 attack, NOT the phone number is relevant, but the IMSI. This is why interception systems are called "IMSI Catchers" and not "Phone number catchers".
And yes, your cell phone location can be tracked and your calls can be intercepted as any other ones. From law enforcement point of view, changing phone number have no relevance when it comes to call interception and location tracking just because the phone number is NOT STORED on SIM card. Phone number changing is actually the single feature that can be tested by the user, which will convince any skeptical person to buy a anonymous SIM card.
Find out more
source
Even a most technical study on Anonymous SIM card scams
| anonymous_sim_scam.pdf |



















 RSS Feed
RSS Feed