Test your "secure" phone. Now.
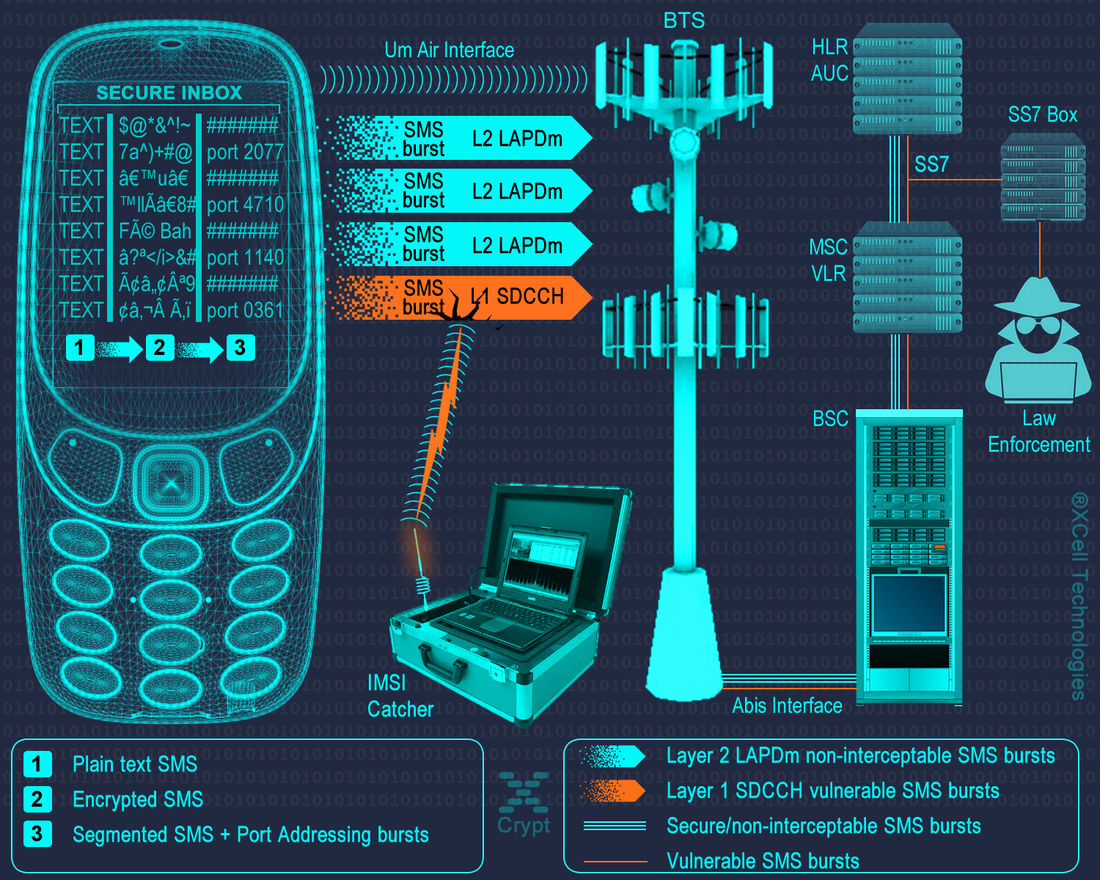
There are not so many hackers around that can actually track your cell phone, because of few simple reasons: expensive hardware needed, lack of knowledge regarding GSM stack and SS7 protocol effective exploits, not to mention that hackers have no interests on you, average Joe. Excepting your worried parents and jealous girlfriend, no one wants to know your (cell phone) geo-location. Tracking a cell phone is not a simple “push button” situation when is done by a hacker. That involve deep and extensive knowledge, pretty expensive hardware, time and not least, an considerable interest on you, average Joe. Which obviously is not the case unless you are just another skilled hacker or a high profile person.
The situation became serious when you did something bad or even illegal. Then, you became a target for law enforcement and/or intelligence agencies. And there is no way to hide your (cell phone) location. They have not only the legal ability to track down your cell phone at any time, but have also technological and human resources to do that, not to mention training and expertise.
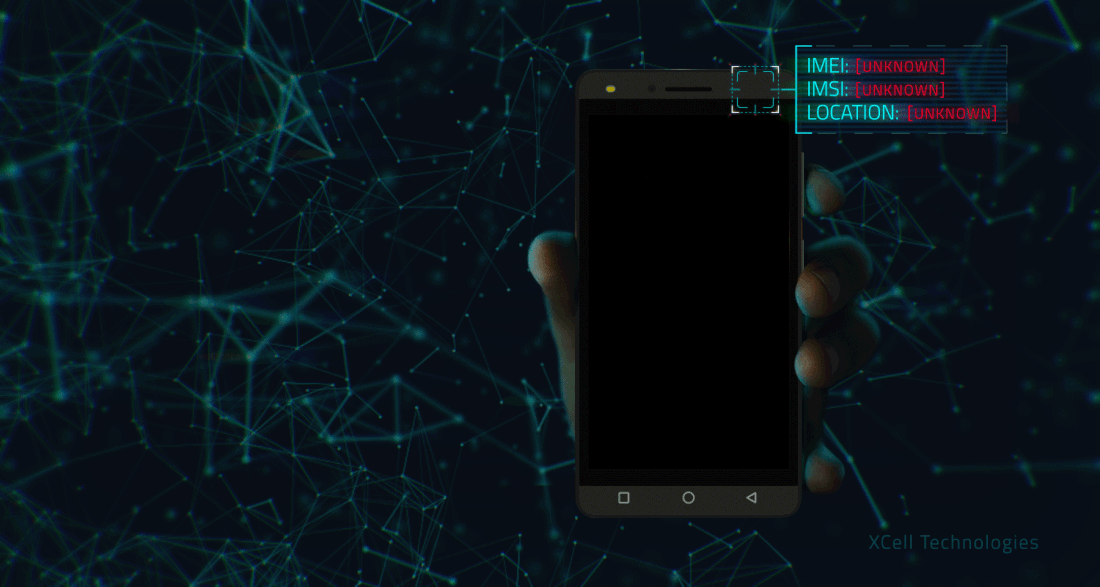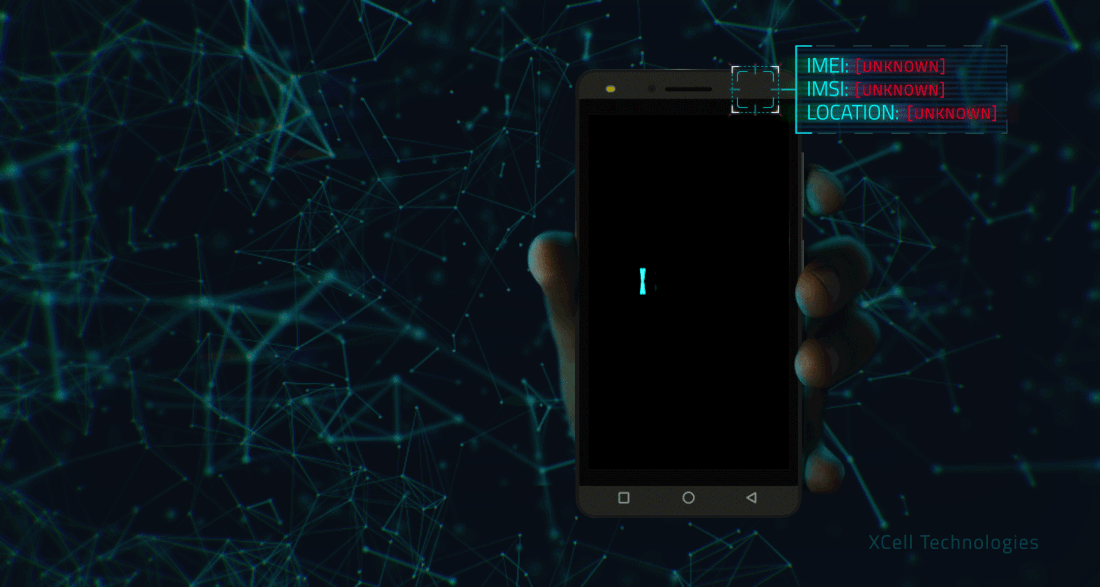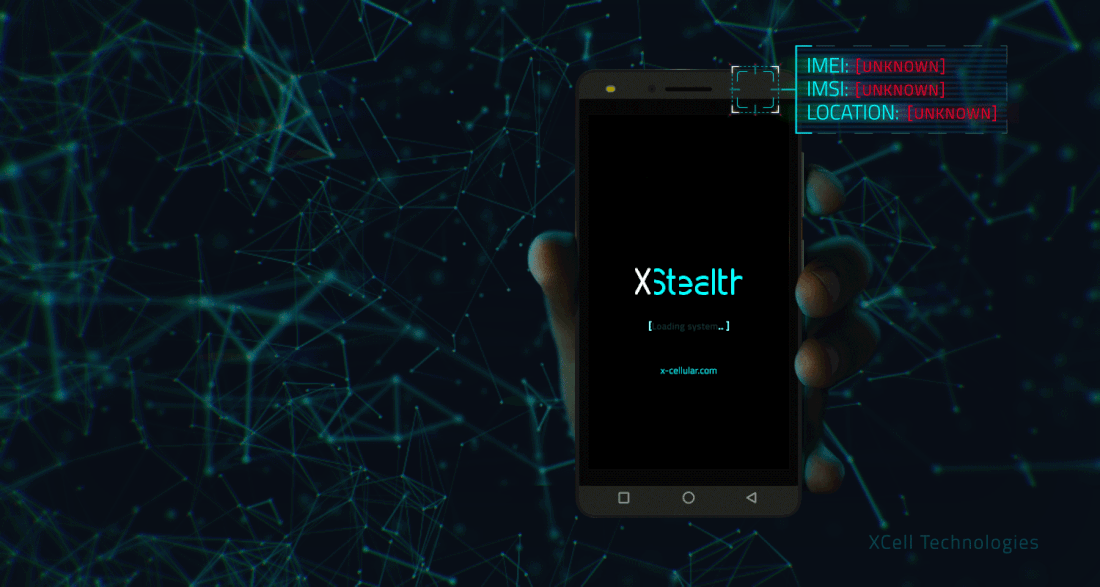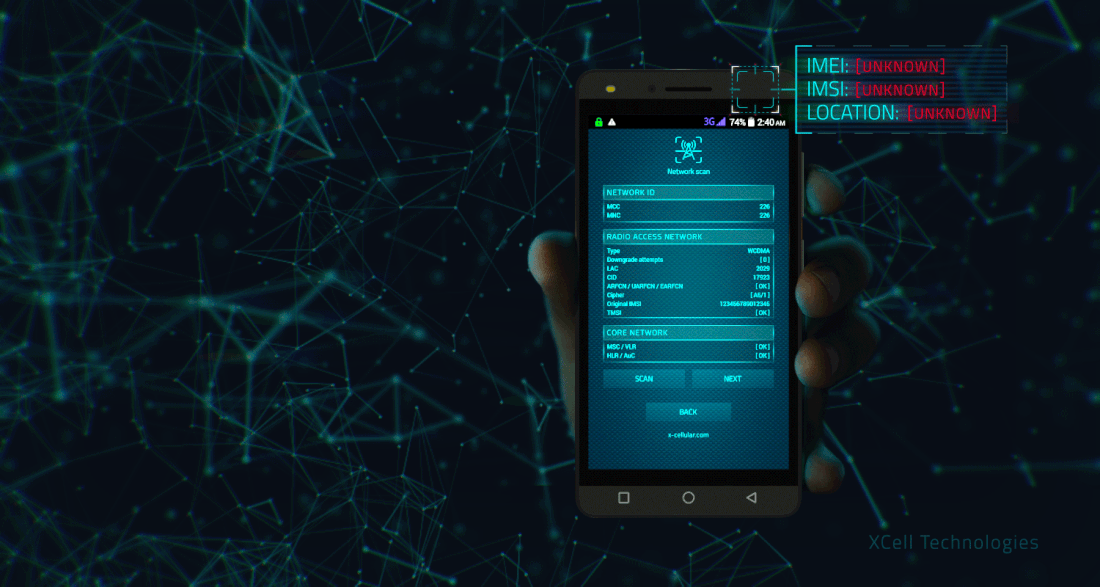
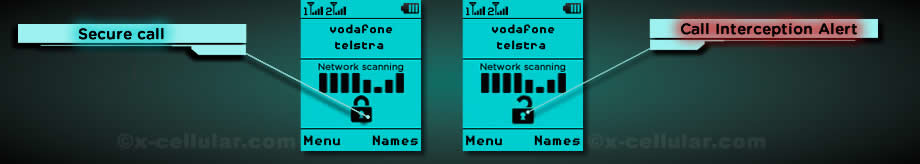
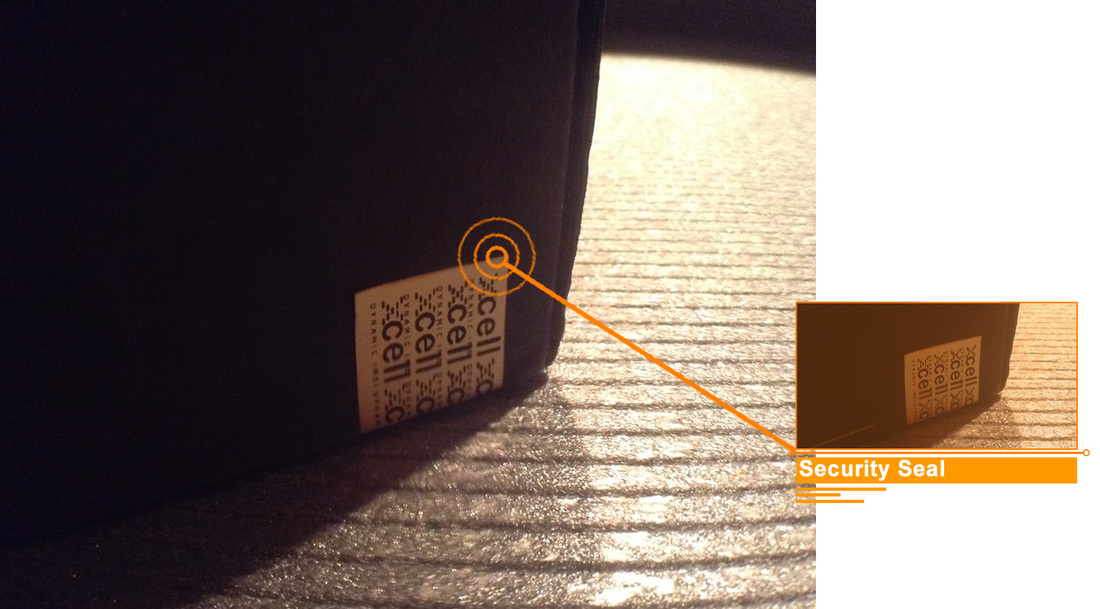
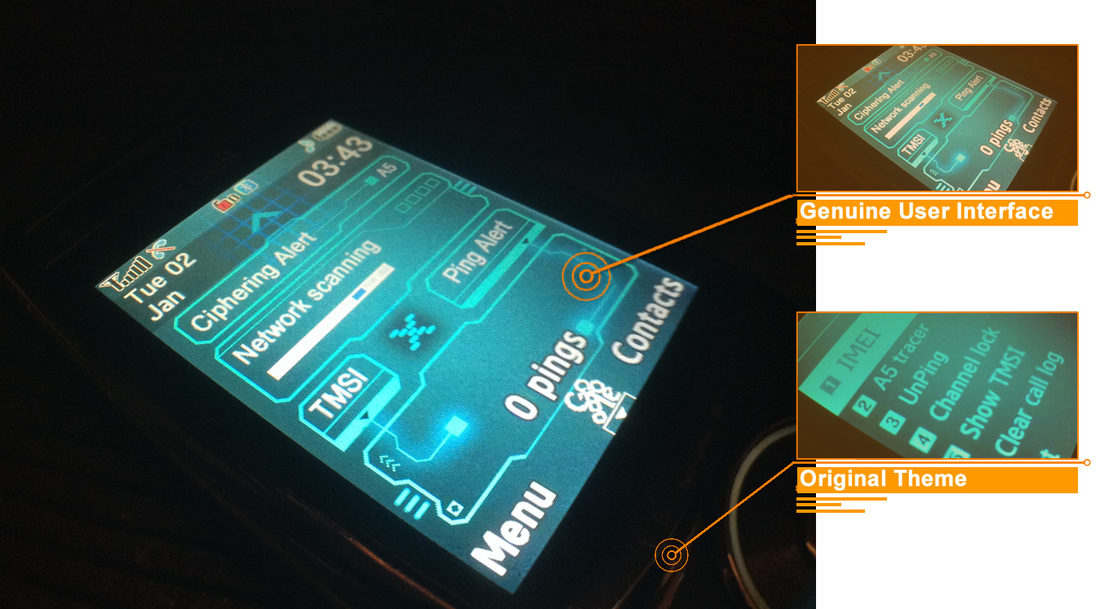
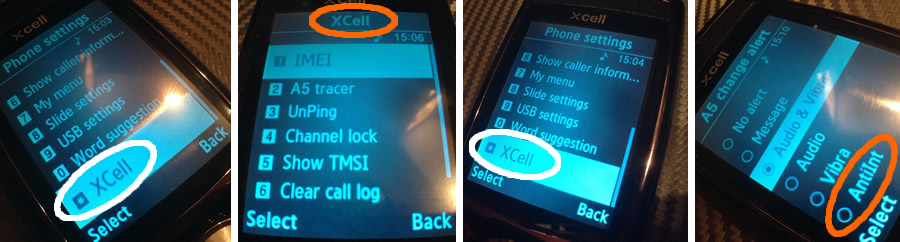
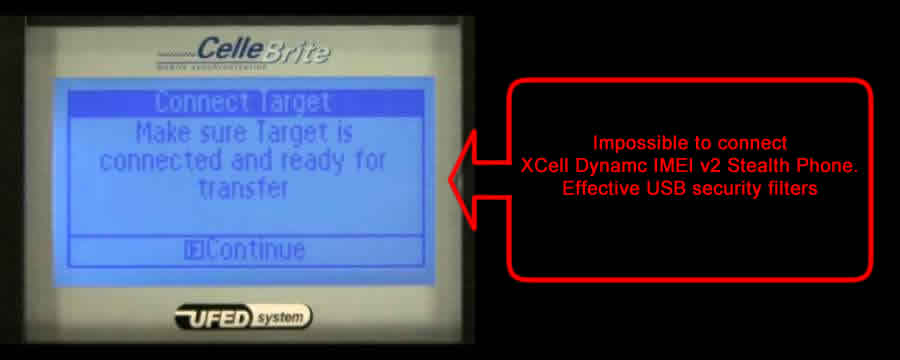
In case you think that your own cell phone is secure, its time for 2 simple tests.
TEST No. 1: NETWORK TESTING BY EMERGENCY CALL.
Read more here.









































 RSS Feed
RSS Feed