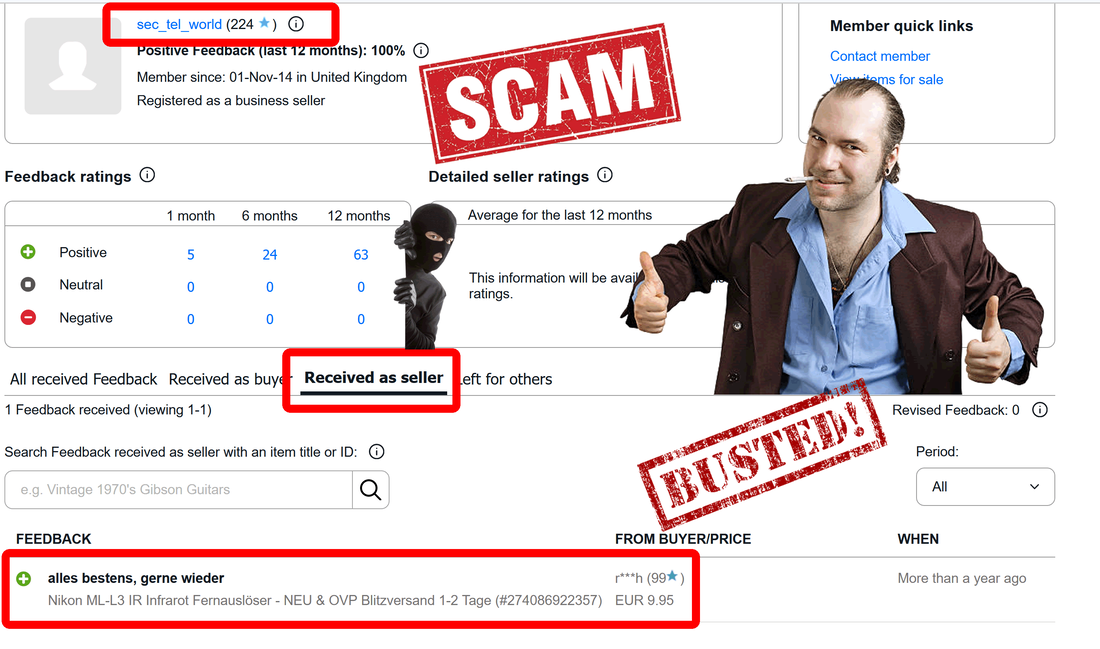
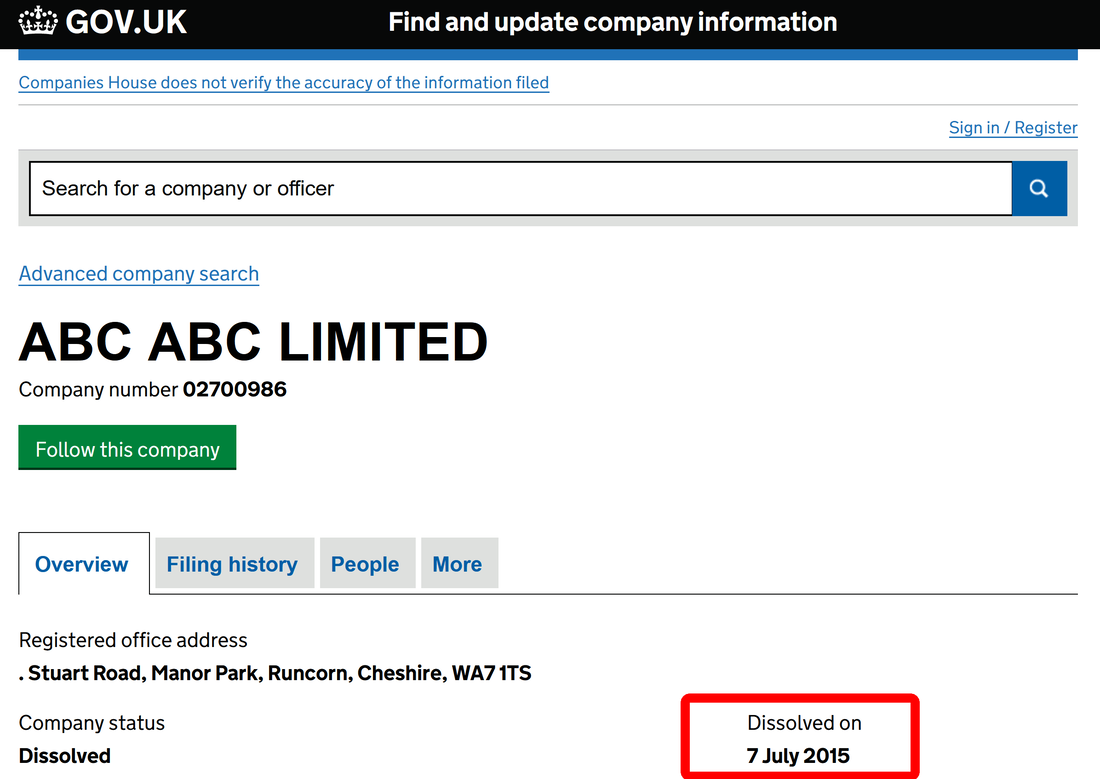
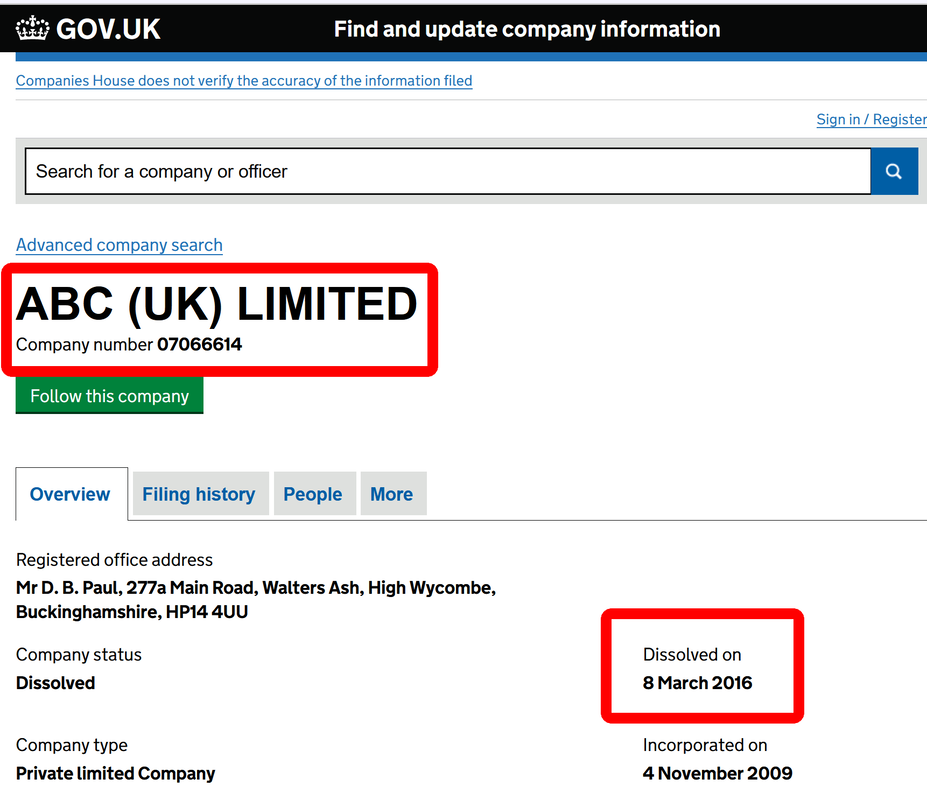
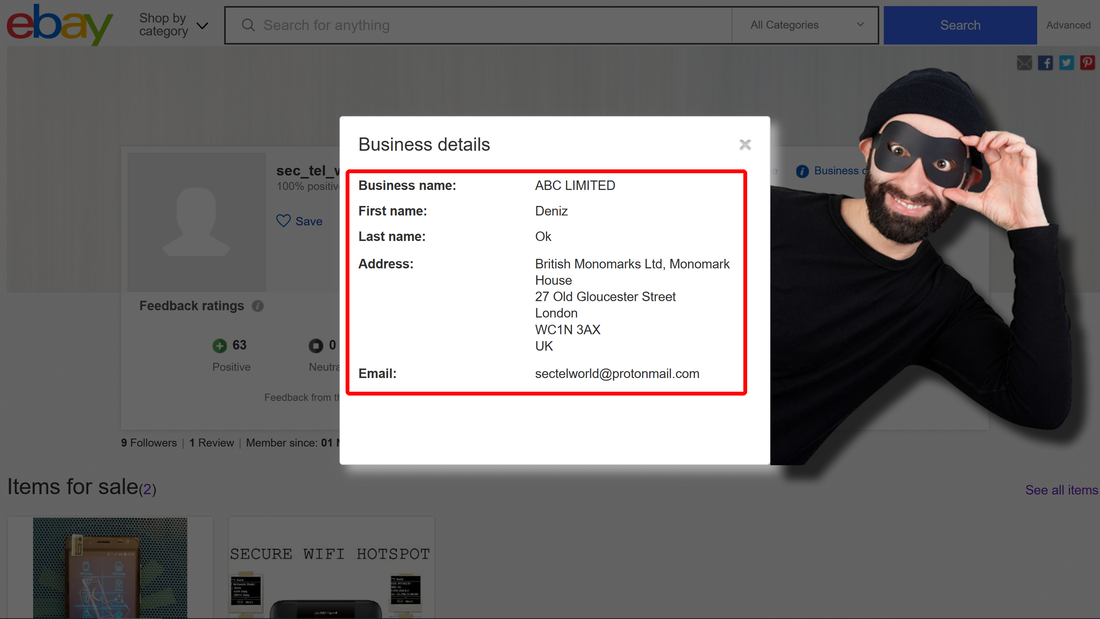
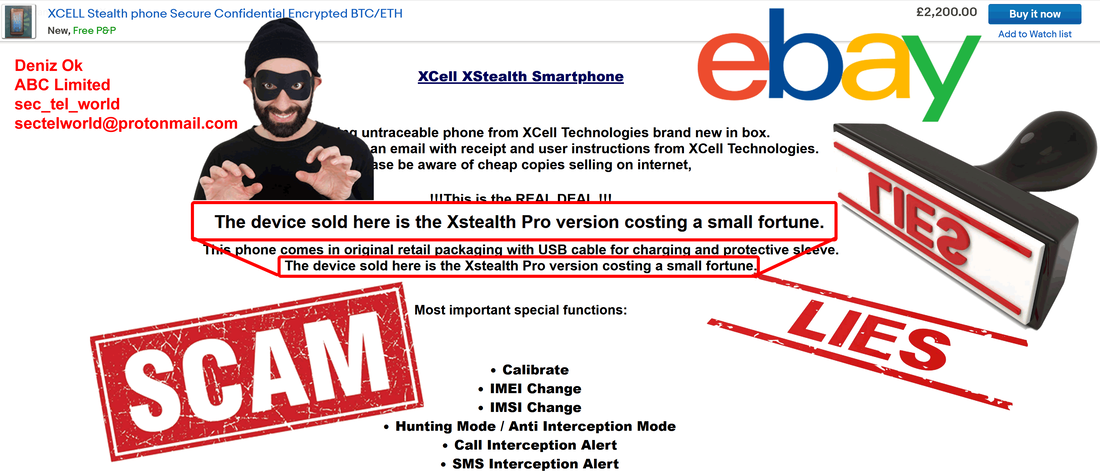
We have discovered a new kind of scam/fraud and the person behind that: Deniz Ok. Apparently is located in Düsseldorf (Germany) and London (UK), if we consider data he offer on eBay account. We doubt that is his real name, but he use this name to run all kind of scams and fraud, associated with 2 company names: ABC Limited (UK) and ABC Großhandel (Germany).
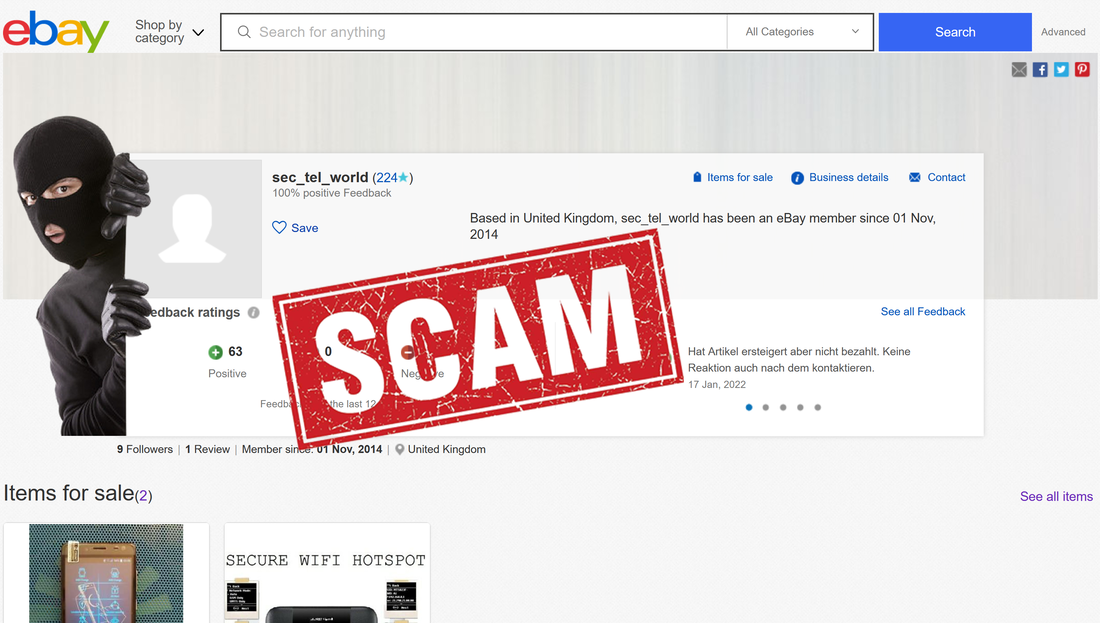
Late edit: Deniz Ok changed his eBay account name from sec_tel_world to secure_gsm, hoping to erase traces and continue this scam. It didn't work.
The fraud
1. All XStealth Phones were delivered without batteries (which are single cell custom made batteries that avoid pro bug insertion). Instead of genuine batteries, fraudster use regular batteries which not only last less than original batteries but are also vulnerable to location tracking and environmental listening when a battery cell is replaced with this sort of professional bug.
2. Based on Deniz Ok requirements, certain software components were removed, and also added other software applications which made those particular XStealth Phones vulnerable to location tracking and remote intrusion.
3. On top of that, due to the nature of products, the fraud was reported first in Germany to Federal Criminal Police Office (Bundeskriminalamt / BKA) and Federal Office for the Protection of the Constitution (Bundesamt für Verfassungsschutz / BfV) and then in the UK, to National Crime Agency (NCA), Metropolitan Police (MSP). MI5 and UK Counter Terrorism Policing. All above agencies got all necessary data to locate every single XStealth Phone ordered by fraudster.
By consequence, every buyer will be located and questioned by law enforcement, once powering up the phone. Instead of a highly secure stealth phone, you will get a banana phone...
This is not too smart for Deniz Ok, and seems like he doesn't care about his customers which are buying those phones to avoid exactly this type of problems.
The fraudster
In Germany, ABC Großhandel company is even strange: operates as ABC Grupp, having its headquarter in... Tallin, Estonia. The company have nothing to do with cellular phones whatsoever, being "mainly focused on the sale and maintenance of vehicles and the wholesale of food and consumer goods".
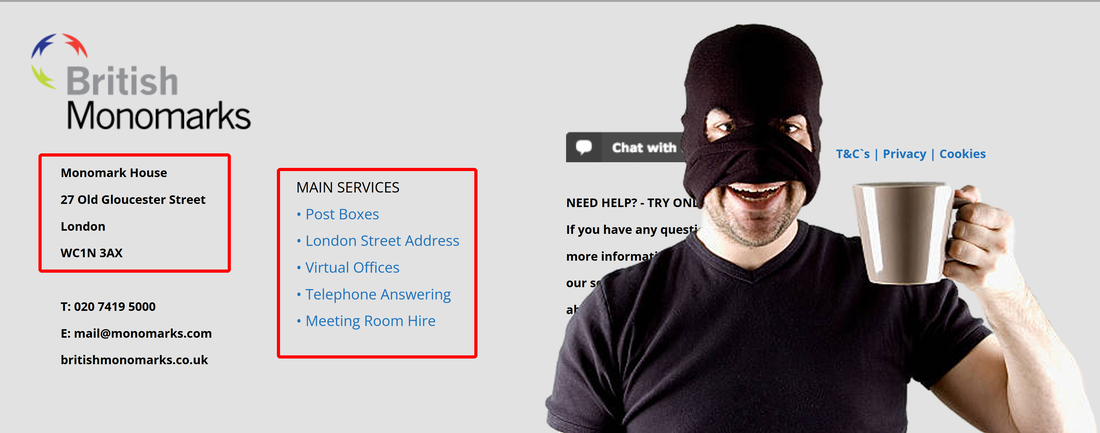
What is British Monomarks Ltd? Well, is not a office building as you might think. British Monomarks Ltd is providing mail forwarding service, virtual office and telephone answering services. Just perfect for any fraudster and scammer that want to convince you are dealing with a real and legit company located in the heart of London, and not with a scammer located in whatever country. This way, scammer think that no strings can lead to him, all inquiries stopping at British Monomarks Ltd. All good, until above mentioned law enforcement agencies are starting to put some unwanted and cheeky questions to British Monomarks Ltd.
The scam
Now, let's see: why buying "secure" cell phones from private persons, on eBay? Probably because of the cheap prices, without keeping in mind that cheap means less. Or even... nothing. And sure, you probably expect customer service, user manuals, accepted returns, extended warranty, repair and updates... from an eBay seller. Do you? If so, have fun with this. But remember that services are provided by companies and not by private individuals. Make sense to you, now? Sure, there are several small companies registered as eBay sellers, but you will never find serious and large companies selling on eBay. This is because eBay is addressing to private individuals rather than companies when it comes to sell an item. Same for eBay buyers: most of them are private persons. Have you seen other companies that manufacture secure cell phones, selling their products directly on eBay? Sure not! Boeing does not sell its Black phone on eBay. Sirin Labs does not sell their phones on eBay. Same for Silent Circle’s Blackphone. And so on. Why buying an XCell Stealth Phone from a private person on eBay, since there are official websites and resellers that provide those phones along with specific customer service, without any hustle and fear of scam?
This is why Deniz Ok sells his scams on eBay and not on a dedicated website: there is no company behind but only a single person. He is not a business man but a con man and a scammer. No need for a real company to do that, but only leaving buyers with a false sense of "serous business" he run. Not to mention the exposure that eBay can offer, even for a scammer like Deniz Ok.
This scammer can anytime delete his eBay account like he does many times before, leaving his "customers" with no help and explanations regarding phone use and various issues.
The lie
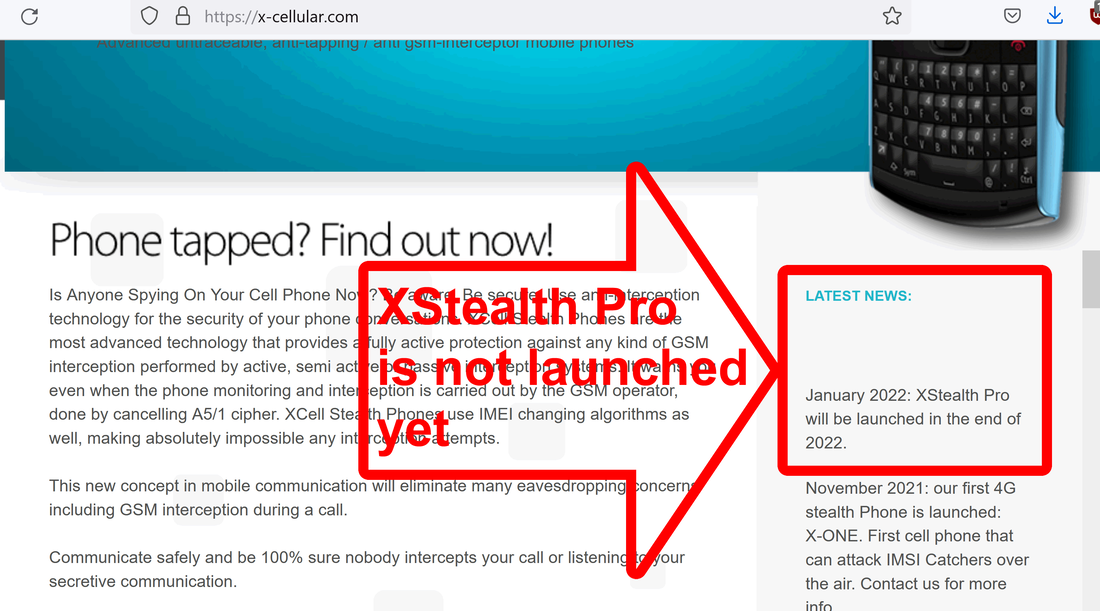
As anyone can read on XCell website, XStealth Pro is not yet released (this article is published today 27th January 2022). Based on XStealth developers declarations, Pro version will be released in the end of 2022. Despite that, Denis OK is offering for sale on eBay, XStealth Pro version (since 2021!):
The good news: until today, he didn't manage to scam any buyers. All stars he get on eBay account comes as buyer and not as seller, building a fake trust for novice buyers. "Buy with confidence from the 100% positive feedback" is obviously a ridiculous lie. There is no feedback as seller. He need all that ratings because of the price he is asking for XStealth "Pro". Big prices can be used only by old and trustworthy sellers, according to eBay policy. This scammer managed to bypass eBay checking.
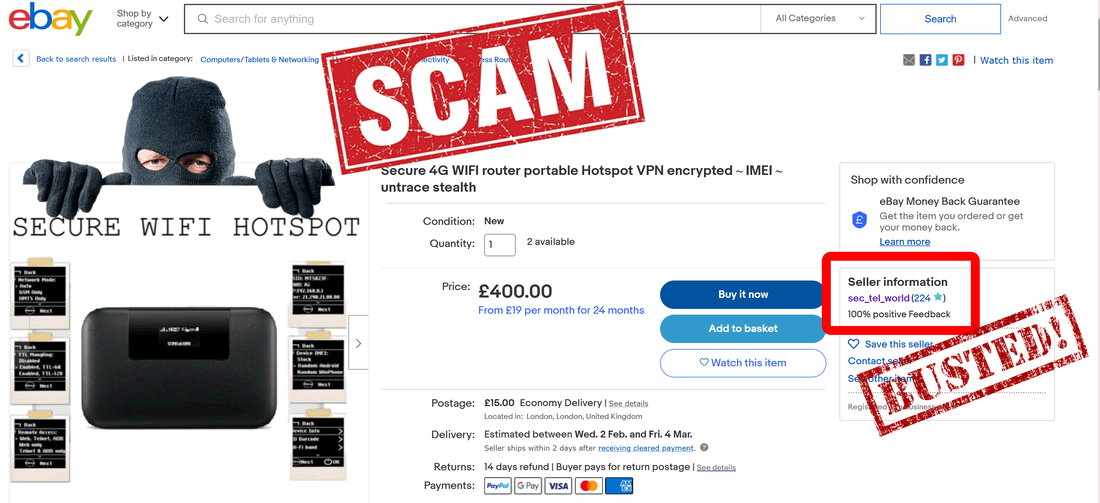
The 2nd scam: "Secure 4G WIFI router"
Huawei router price is only about 30-40 USD. You can check it on Google. Taking advantage on regular people lack of knowledge, scammer Deniz Ok is reselling this device with 400 GBP (about 540 USD) without making any modifications to make it more "secure". Nothing. Nada. Zero. But 200% profit margin. Cool or what?
On Aliexpress.com you can find the same product he sell (and same pictures he use on eBay), with detailed description. Nothing about "special" security, encrypted connection and all that sort of lies scammer use: www.aliexpress.com/item/32981395475.html Same here. And here.
No need to pay huge prices to this scammer. Here is how you can change regular router IMEI:
Here is why:
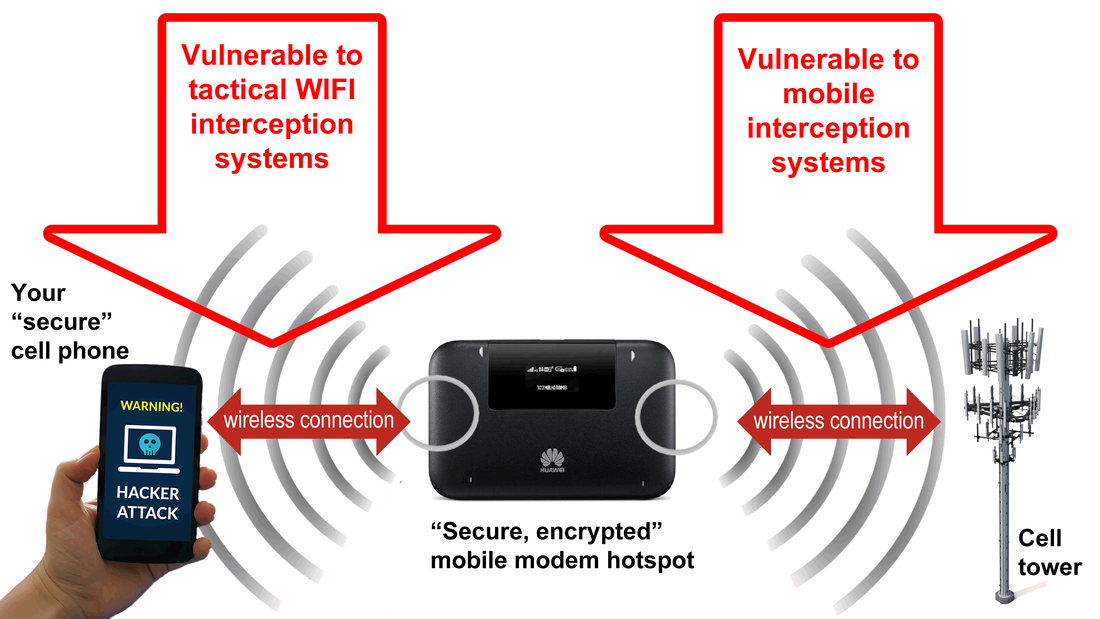
1. A mobile router/WIFI hotspot does need a SIM card in order to work. SIM card provide connection between router and mobile network (outer world, internet). And guess what: router will connect to mobile network trough... cell towers and not directly to internet because this is just impossible. Hence, no real security because to allow connection, cell tower (and mobile network servers) need to know 2 things about any device that is asking for connection (including mobile routers): IMEI (router ID) and IMSI (SIM card ID). Only after providing this sensitive information to network, a mobile router can connect to internet trough a cell tower. For those who don't know, there are some devices called IMSI catchers, used for location tracking, call interception and data interception. An IMSI catcher does what is supposed to do: collecting IMEI and IMSI, then using them for further operations as location tracking, call interception and data interception. Funny, isn't it?
If mobile router IMEI can be changed at will, IMSI cannot be changed unless you insert every time another SIM card. However, when mobile router will connect to cell tower both IMEI and IMSI are broadcasted over the air and used for interception purposes. If an IMSI catcher or GSM interceptor are active within range, interception, location tracking and monitoring is trivial.
When you are on the move, mobile router will connect to other cell towers (trough SIM card) exactly as any other cell phone when travelling. Hence, your location data is exposed and widely available for network provider and law enforcement (and even for hackers). Location tracking is trivial. And "security" is just a lie that scammer Deniz Ok tells you.
2. Every single mobile router does have a so called router ID: a 32-bit IP address that uniquely identifies a router in an Autonomous System. This is also vulnerable to interception.
3. Every single mobile router have a MAC address (hardware ID) which is also vulnerable to location tracking and surface attacks.
4. Every single mobile router does use a SSID (wireless network name) broadcasted in clear text over the air. This is also a vulnerability, transforming your "secure" mobile router in a sitting duck when it comes to lawful interception because will say "hey, here I am!" to any mobile interception systems.
Compared with regular cell phones, a mobile router is more vulnerable to remote attacks, interception and monitoring because is using 2 vulnerable wireless connections (since a cell phone usually have a single connection with cell towers): wireless connection with cell towers and wireless connection with your cell phone, laptop or PC. Different radio frequencies but same vulnerabilities:
1. Wireless connection between router and your mobile device (cell phone, tablet, laptop, PC, etc.). Intercepting WIFI is trivial and more easy to do than intercepting a cell phone, due to WIFI security lack (authentication procedures, encryption, etc.) compared to regular mobile networks. As a matter of fact, tactical WIFI interception systems are way more cheap than mobile interception systems. You can find plenty of such systems on a simple Google search. Just to name few:
www.shoghicom.com/wifi-interception.php
www.tarideal.com/product/tactical-wi-fi-interception/
https://pegasusintelligence.com/sigint/#TacticalWiFiInterception
https://test2.zonetex.net/our-products/wi-fi-interception-system/
cerberussolutions.co.id/productssservices-wifi-interception-solutions/
https://spectradome.com/wifi-interceptors/
https://www.stratign.com/product/wi-fi-interception-system/
Thinking of connecting your cell phone or PC to WIFI router / mobile hotspot via cable, which will reduce attack surface? Well, is remaining another vulnerable connection: data connection to cell tower that provide internet connection. If you think that your "secure" router is connected somehow directly (via cable?) to some sort of "secure" servers, you are completely wrong. This is not how it works. Your "secure" router will connect to the closest cell tower within your area (in the very same way as your cell phone does), in order to provide internet connection. Hence, no matter which kind of data connection exist between cell tower and the rest of the network: wireless connection is the weak point, exploitable by regular IMSI catchers and GSM interceptors that will intercept data connection (like this one), not to mention lawful interception systems.
Deniz Ok modus operandi
Scamming technique he use
If you are a buyer, scam is done pretty much straight forward: scammer pretend to sell "Real working untraceable phone from XCell Technologies brand new in box." In fact, all XStealth Phones he sell are marked and monitored by law enforcement agencies with the help of XCell Technologies programmers. This is possible because Deniz Ok ordered a custom made lot version that have vulnerable software apps installed on his demand for whatever reasons. We have to mention that regular XStealth Phones cannot be tracked and monitored even by the manufactirer (or programmers), not to mention law enforcement agencies or hackers.
This way, when you buy a stealth phone from Deniz Ok, will get no security nor privacy. Instead, you can get an entire Police squad at your door step once you power up the phone.
The same if you buy the other scam: "Secure 4G WIFI router portable Hotspot VPN encrypted ~ IMEI ~ untrace stealth" and start doing some online monkey business.
Situation is different if you sell secure cell phones, any other devices or whatever marchendise he is interested to "buy". Deniz Ok is using old fraud techniques, almost as a talenbted con man. According to XCell Technologies managing board, this fraudster will first pay for all devices he order. Then, right after shipping when fraudster is sure that the parcel is on its way and cannot be returned to seller, he will pretend that devices are defective and not manufactured based on his requests, demanding payment refund. Fraudster will keep all devices and will stop replying to any messages. Managing board mentioned that Deniz Ok used disposable phone numbers in order to contact them and assigned forwarding agent. This fraud might involve telephone service provided for Deniz Ok by famed British Monomarks Ltd.
Recently, Deniz Ok tried to scam a German reseller which is pretty new in business, pretending that he is calling on behalf of German Domestic Intelligence Service - Federal Office for the Protection of the Constitution (Bundesamt für Verfassungsschutz / BfV) and he want to order several dozens of stealth phones, being ready to pay for all quantity before shipping and without testing any stealth phone before payment, which is pretty unusual. Please note the same pattern used to scam XCell Technologies, before. Fraudster mistake was a beginner one: he considered his business "partner" (XCell Technologies German reseller) a newbie that have no idea about how any intelligence agency run technology aquisitions. Based on EU regulations, they have to set up a public tender even when buying office paper and pencils, not to mention hi-tech devices that cost a lot. Also fraudster Deniz Ok didn't prepared his fraud very well: he had no idea that BfV does not buy directly interception and security devices, because they don't use that directly. All technology is bought trough 2 support and research agencies for law enforcement and BfV, called ZITiS (Central Office for Information Technology in the Security Sector) and BSI (Federal Office for Information Security) with competences in information security and cyber security. So, German reseller realized that is a fraud on its very beginning, having fun with fraudster and playing with his nerves. In the end, fraudster tried to scare the reseller, threatening with BfV revenge, which was the most funny part of his failed fraud.
What you can do?
In case you have bought such device, call the Police and register a fraud complaint. Also report the account and products to eBay customer service. If really lucky, you can get a full refund for the scam.
If you really want to buy and not sure if you will buy an authentic Stealth Phone, you can contact us at any time, or you can contact devices manufacturer and its official distributors. Never get scammed again.
You can help others avoid secure phone scam, by distributing this article.













 RSS Feed
RSS Feed