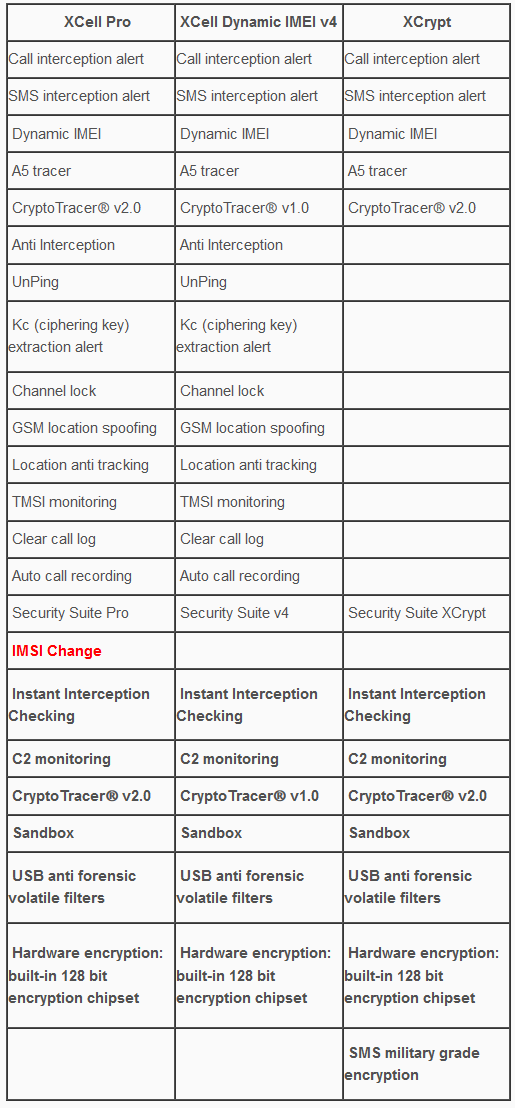
- XCrypt, a military grade SMS encryption Stealth Phone which combine active security measures (dynamic IMEI) and passive measures (SMS encryption). The phone can send/receive standard/unencrypted SMSs to/from any other cell phone.
- XCell Dynamic IMEI v4 Stealth Phone: will come with newly added Security Suite (cryptoTRACER v2.0, Interception Instant Check, Sandbox v2 and C2 Monitoring).
- XCell Pro: same as XCell Dynamic IMEI v4 Stealth Phone, but with a revolutionary and absolutely unique function: IMSI Change. This will be our next flagship product. A real weapon when used in a smart way. Also, cryptoTracer v3.0 will run on this device.
Please see below a few specs:
About Interception Systems
1. Active and semi active interception is easily detected due to the method by which this interception is done. The handset will detect any lack of standard GSM encryption (A5/1) generated by any active and semi active interceptors.
2. Newest GSM Interceptors, instead of "no ciphering" (A5/0), will lower encryption level from standard A5/1 to weaker A5/2 encryption algorithm (which can be decrypted in real time) managing this way to trick most of "secure" devices that claim to detect interception. XCell Stealth Phones will trigger Interception alert whenever will detect such low encryption, by displaying a yellow icon lock on top of the screen (instead of green lock icon):
However, most used interception systems nowadays are active and semi active (most of them are mobile systems), due to the high rate of success when it comes to call interception and also because interception warrants are not really required.
3. Lawful interception (also known as network switch based interception, SS7 interception or interception based on operator help) is made by using a special hardware installed on operator side at HLR/VLR level or most common at SS7 level (network switch), by law enforcement agencies. When a phone call or SMS is diverted by such hardware, will generate a specific delay due to hardware latency. Our proprietary algorithm called cryptoTRACER® is detecting this latency, alerting user when a phone call is monitored by SS7 means.
Special phone functions, explained
- Dynamic IMEI (available for XCell Pro, XCell Dynamic IMEI v4 and XCrypt)
All IMSI Catchers, GSM Interceptors and SS7 Interception Systems are using mainly phone IMEI in order to perform call interception.
Phone unique ID (IMEI) will be automatically changed after every single call or SMS, based on a special algorithm that generates valid IMEIs. Also, the user can set up a custom IMEI. Advantages of using a custom IMEI are explained in User Manual. By enabling Dynamic IMEI function, is like using a new cell phone for every outgoing and incoming call and SMS.
Legal note: original IMEI can be restored at any time by the user, by simply selecting “Use original IMEI” option. - A5 tracer (available for XCell Pro, XCell Dynamic IMEI v4 and XCrypt)
All communications on GSM networks are encrypted by default, using a stream cypher called A/5. In order to perform call interception, GSM Interceptors will disable network encryption or (the newest systems) will lower encryption level from A5/1 to weaker A5/2 which can be decrypted in less than a second.
The phone will permanently monitor standard A5/1 GSM encryption (provided by the GSM network), triggering alerts whenever lack of encryption or encryption switching will be detected, alerting this way the user about call interception before making a call or answering a phone call. - CryptoTracerⓇ (available for XCell Pro, XCell Dynamic IMEI v4 and XCrypt)
Beside IMSI Catchers and GSM Interceptors which are small and mobile (sometimes vehicle mounted) interception systems, law enforcement are using so called Lawful Interception (SS7 Interception or Interception by operator help), a special hardware connected directly to GSM core network (at network switch level).
CryptoTracerⓇ is a unique function based on XCell proprietary algorithms which can instantly detect lawful interception attempts, alerting user whenever calls and SMSs are intercepted by SS7 means.
When enabled, Anti Interception function will simply block any outgoing and incoming calls and SMSs, as long as interception is detected by the phone. The phone will remain silent during interception attempts.
5. UnPing (available only for XCell Pro and XCell Dynamic IMEI v4)
In order to locate the phone, law enforcement are sending to the phone so called Location Tracking Pings (LTP), which basically are malformed SMSs (invisible on ordinary cell phones, no matter the brand, price or technology used), usually by using GSM network. In response to received ping, an ordinary phone will send back his GSM location data (not to be confounded with GPS tracking) consisting in tower Cell ID data, which actually means the tower GPS position on which the phone is connected to.
When UnPing function is enabled, XCell Stealth Phone will:
a. trigger alerts whenever a Location Tracking Ping is received
b. block responses to received LTP, hiding this way the phone location. Certain special settings are involved.
Location tracking alerts are displayed on phone home screen, being also stored on a text file.
6. Kc (ciphering key) extraction alert (available only for XCell Pro and XCell Dynamic IMEI v4)
GSM Interceptors (semi active ones), in order to decrypt intercepted phone calls, need to know ciphering key (Kc) which is stored on the SIM card. In order to get Kc off the SIM, a GSM Interceptor will send to the phone so called challenges (special pings, other than LTP), to which the phone will reply with parts of ciphering key. Depending on GSM Interceptor type and brand, 5 to 20 pings needs to be sent to get a complete ciphering key.
XCell Stealth Phones will alert the user whenever such a ping is received, displaying alerts on phone home screen. Alerts history is saved on a text file.
7. Channel lock (available only for XCell Pro and XCell Dynamic IMEI v4)
A cell tower and a mobile phone are communicating by using a pair of radio channels (uplink and downlink), called ARFCN. Every cell tower is using different ARFCN, because of the GSM network requirements. When a cell phone moves from a cell tower on another, will change ARFCN (which is called handover). An IMSI Catcher or GSM Interceptors which basically are fake cell towers, will add a new ARFCN to local GSM network, in order to force the phones within area to connect to the “new cell tower”, performing this way call interception.
When enabling Channel lock function, XCell Stealth Phones will lock on a certain real cell tower, preventing this way a connection to any other cell tower, including fake ones (IMSI Catchers, GSM Interceptors). More info on User Manual. Phone handover will be blocked, so the phone will remain connected on the real GSM network.
8. Location spoofing (available only for XCell Pro and XCell Dynamic IMEI v4)
Mobile phone location tracking is based on the cell towers on which the phone is connected to. A cell phone can “see” 6 neighboring cell towers at a time (or less, depending on the area), and law enforcement is using this info in order to calculate accurately the cell phone location (+/- 5 meters) by using so called GSM triangulation procedures.
XCell Stealth Phone users can effectively hide (spoof) the real phone location, by using this special function. The phone will spoof location whenever is static or on the move, by randomly connecting on cell towers. This way, the phone will appear to be 1 to 10 Km away from its real location (depending on the network cell towers density).
For location spoofing, XCell Stealth Phones does not need to use Internet connection and/or third party servers, being a built-in feature. More info on User Manual.
Also, XCell Stealth Phones have no GPS modules, adding this way an extra security layer.
9. TMSI monitoring (available only for XCell Pro and XCell Dynamic IMEI v4)
Because IMSI (SIM card unique identifier) sending out to the network should be prevented for security reasons, the network will allocate instead IMSI, a temporary IMSI called TMSI. Based on GSM regulations, TMSI have to change on every phone restart, and when the phone is changing LAC (Location Area Code).
Once connected to a GSM Interceptor, the phone will display the same TMSI after restarting, due to low computing capabilities of the GSM Interceptor, compared with a GSM network.
If there are any doubts, the user can restart the phone and checking if a new TMSI pops up on the home screen. If not, that means the phone is connected to a fake cell tower, being at risk. This way, the user can instantly check out of the phone is connected to the real network or to a GSM Interceptor.
10. Clear call log (available only for XCell Pro and XCell Dynamic IMEI v4)
The phone will automatically clear call log, so no call history will be available in case of forensic analysis.
11. Auto call recording (available only for XCell Pro and XCell Dynamic IMEI v4)
The phone will automatically record every single phone call, saving audio files on phone internal memory or SD card. There is no notification recording at the beginning of the call, or an audible beep-tone for secret recording. Own call recordings are useful when audio editing is used on actual recordings, changing the meaning of the conversation (law suits).
12. SMS military grade encryption (available only for XCrypt)
XCrypt it’s a special software application used to send/receive two kind of messages: standard and encrypted SMSs. Since standard SMSs can be sent/received to/from any other cell phone, encrypted messages can be exchanged only between two or more XCrypt Stealth Phones.
Because XCrypt it’s a part of Operating System and does not run as a stand alone application, it is not possible to decompile or reverse engineering the obfuscated code, in order to find out which encryption algorithm is used, in order to attempt SMS decryption.
XCrypt does not use for encryption Internet connection and third party servers, but a special partition (Sandbox) that run on the phone.
13. Forensic bulletproof (available for XCell Pro, XCell Dynamic IMEI v4 and XCrypt)
The phones are protected against forensic analysis by volatile USB filters. No forensic device can extract any data or files off the phone. Once connected to a forensic device, PC or service box, volatile USB filters will trigger motherboard self-nuke, and the phone will get in protected mode (permanent boot loop) due to bootloaders auto-delete. If the phone is accidentally connected to a PC for charging purposes, the self-nuke mechanism will be triggered. Only provided wall chargers should be used for charging, being paired with the phones.
Security Suite
On new launched XCell Stealth Phones we have added a new section: Security Suite. Along with other special functions, all other functions contained by Security Suite run in a separate partition (Sandbox) for a faster operation.
1 - IMSI Change which along with IMEI change function is transforming the phone in a real sophisticated counterintelligence weapon. IMSI Change function does not require any Internet connection, third party servers or monthly subscription. This special function runs locally on the phone (Sandbox partition), being a unique function which no other phones offer at this time.
IMSI Change function allow user to change IMSI value (SIM registration number stored on the SIM card), by keeping the same phone number (MSISDN).
How does it work?
The phone will clone any SIM card inserted (please use only MNO SIM Cards) by using a Sandbox located app: IMSI Virtual Engine. Once cloned, the real SIM will be quarantined, being used instead a virtual SIM card which can change its IMSI by by generating valid IMSI’s. Please note that abusing this function can generate SIM network rejection (network dependent). Use it carefully.
IMSI Change does not work automatically, as IMEI change works. The user should launch IMSI Change every time when a new IMSI is needed, generating a new virtual IMSI and then exiting the application. The new generated IMSI will be used only for the next outgoing or incoming call. After that, the phone will return to original IMSI. If a new IMSI will be needed, the whole process should be repeated.
Please note that MSISDN (the phone number) will not change when using IMSI change function.
Used in conjunction with IMEI change, IMSI change function will transform your XCell Stealth Phone Pro in one of most powerful communications weapon: you will literally have a new phone (IMEI) and a new SIM (IMSI) for every single phone call. Use it with precautions.
2 - cryptoTRACERⓇ, which is a function that can detect lawful interception performed by SS7 Boxes (aka Network Switch Based Interception);
3 - Sandbox
IMEI engine and other software components has been moved in a separate partition (Sandbox) in order to make them working faster and smoother. System restarting has been suppressed in case of any abnormal network characteristics (i.e. generated by IMSI Catchers/GSM Interceptors).
4 - Interception Instant Check
Once launched, the function will start checking both Active and Passive interception, step by step. Regarding interception performed with Active/Semi Active GSM Interceptors, the phone will check:
1. BTS parameters
2. RSSI
3. Cell ID
4. LAC
5. ARFCN
6. Ki retrieving attempts (ciphering key stored on the SIM card).
7. Baseband attack attempts.
Regarding interception performed by Passive GSM Interceptors, the phone will check:
1. Uplink.
2. Downlink.
3. Will ping HLR/VLR core network, computing network redundancy and abnormal ping delays.
4. In the end, will generate a Network Security Rating.
5 - C1/C2 monitoring
By forcing cell reselection (C2 parameter), Active and Semi Active GSM Interceptors will force any cell phones to disconnect from home network and connect to the rogue BTS impersonated by the equipment. This is called also BCCH manipulation, being used by all modern GSM Interceptors. When launching this function, the phone will:
1. Extract C1 value, from serving cell.
Will compute C2 value by using a special algorithm, the same used by any GSM network
2. Will look for at least other 6 neighboring cell towers, ordered by RSSI value.
Will compare C1 to C2.
3. Will trigger alert if no neighboring cells are found (a clear indication that a GSM Interceptor is active within area).
Will look for CPICH, RSCP and BCCH.
4. Will display forced handover attempts (if any).
5. Will display Channel lock fails (if any).
XCell Pro, XCell Dynamic IMEI v4 and XCrypt comes in 3 flavors:
- Branded version (XCell logo, XCell URL, XCell homescreen, XCell boot animation and shut down animation, etc.)
- Unbranded (white label) version. Generic phone, will be delivered under Samsung brand name. No reference to XCell, no XCell logo.
- Customized version, based on customer requirements.
On demand, XCell Technologies provide the following:
- unbranded or customized user manual (no reference to XCell);
- unbranded cell phones (hardware and software) and boxes (no XCell logo).
- customized cell phones (hardware and software) with reseller logo.
Full phone customization (special branding) involve an extra payment of 2500 euro. This include:
- welcome screen (with your company logo and URL)
- welcome animation (your company logo animation)
- shutdown animation (your company logo animation)
- phone home screen with your company logo.
On customer request, Stealth Phones can be delivered without any brand name, in generic boxes and without any reference to the XCell Technologies. We can print on the phone and box any brand name you want (brand name of your business for example, or a trade name chosen by you).


 RSS Feed
RSS Feed